In today’s digital age, your IP address is like a unique digital fingerprint that reveals your online activities. It’s natural to feel uneasy knowing that every move you make can be tracked and traced. This level of visibility can become frustrating when accessing content restricted by geographical boundaries.
Fortunately, methods are available to hide your IP address and increase your online privacy. Using virtual private networks (VPNs) or anonymising your IP address and making it appear from and appear different from your public IP address holds valuable information about your browsing history and can be potentially harmful to privacy. For privacy or access to restricted content, hiding your IP address is essential in today’s internet landscape. With the right strategies, you can take control of your online presence and ensure that your digital activities remain private and secure.
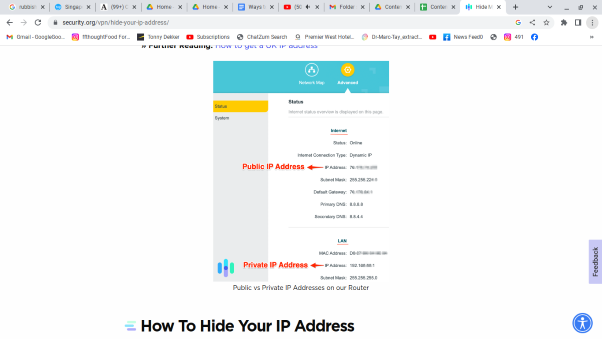
What’s my IP address?
If you’re wondering about your IP address, the first step to hiding it is to find out what it is.
You can easily do this by going to Google and searching for my address. You’ll receive a result like 123.45.67.89, which is an IPv4 address. Some people may also have IPv6 connectivity, but it has yet to be transmitted universally. If Anr. If IAn internet provider supports IPv6, you can also look up your IPv6 address, which will look something like 2001:0db8:85a3:0000:0000:8a2e:0370:7334. Both types of addresses serve the same purpose, so if you want to hide your IPv4 address, you’ll likely want to hide your IPv6 address.
It’s important to note that your IP address may change occasionally due to how the internet works. Still, given time, you are the only person with that specific IP address on the Internet to physical addresses, IP address. IPs enable computers on the Internet to communicate with each other. They are a fundamental component of the IP protocol, which forms the basis of the Internet.
Why hide your IP address?
There are numerous reasons to consider hiding your IP address. Firstly, doing so can help safeguard your privacy by concealing your online activities from entities such as the government, your internet service provider (ISP), the websites you frequent, and the search engines you utilise. This measure is crucial in maintaining privacy and avoiding unwanted surveillance.
Requirements: Concealing your IP address enables you to access geo-blocked content. Many online services and content are restricted based on geographic location, particularly streaming platforms that determine available content based on visible IP addresses. Concealing your IP address allows you to circumvent these restrictions and access otherwise unavailable content.
Preventing digital tracking is another critical benefit of hiding your IP address. Ad networks and websites often track browsing history and behaviour using IP addresses. By concealing yours, you can limit the data collected about you and protect your online privacy.
Protecting your data from hackers is a critical reason for hiding your IP address. Cybercriminals can exploit IP addresses to locate physical locations, track online activities, and intercept traffic. Concealing your IP address protects against these threats, especially when accessing open or public Wi-Fi networks while travelling abroad.
Lastly, avoiding government surveillance is a significant consideration for many individuals. Some governments monitor citizens’ online activities closely. Hiding your IP address can help maintain privacy and evade government surveillance efforts.
How to conceal your IP address
There are multiple methods to conceal your IP address, and one practical approach is to utilise a VPN (Virtual Private Network) such as NordVPN. A VPN encrypts all data transmitted over the internet and directs it through a server in a different area, concealing your IP address. By doing so, websites and online applications only perceive the server’s IP address and virtual location rather than your own.
Most VPNs are available through subscription services for a nominal monthly fee, providing access to numerous servers globally. Once you sign up and install the applications on your devices, hiding your IP address becomes a simple task that only requires If NordVPN does not align with your requirements, alternative VPN services like Surfshark or ExpressVPN offer comparable features and substantial discounts for extended subscriptions.
To conceal your IP address, check your current IP address using a search engine. Next, register for a VPN service such as NordVPN. After signing up, download the VPN app onto your device from the provider’s website for Windows and Mac users or from the App Store and Google Play for iOS and Android users. Once downloaded, install and run the VPN app, then sign in with your account credentials. Choose a server or server location to obtain a new IP address. Click the Connect button to establish a connection through a private network. Once connected, verify your new IP address using a search engine to check your IP.
Using a VPN with shared IP addresses hides your real IP and makes distinguishing your online activity from both challenging for users. This adds a significant layer of anonymity and enhances the security of your network connection.
Suppose you are serious about concealing your IP address. In that case, selecting a VPN with specific features is crucial:
- Private DNS servers: DNS translates domain names into IP addresses for internet communication. Using a VPN with its own DNS servers ensures that your IP address is never exposed to third parties.
- Leak protection: Look for a VPN that prevents DNS, IPv6, and WebRTC leaks to avoid exposing your IP address.
- Kill switch: A kill switch or network lock disconnects your device from the internet if the VPN connection drops, preventing any data from being sent from your actual IP address.
These features provide comprehensive protection and enhance privacy while using a VPN.
Maxthon browser hides IP addresses using a built-in feature called Cloud Protection. This feature acts as a proxy server to mask the user’s original IP address, making requests for different locations. When enabled, all internet traffic is routed through Maxthon’s servers, providing an additional layer of anonymity and privacy.
Cloud Protect tests traffic through encrypted servers to guard user data and maintain anonymity. This means that users can browse the web without revealing actual property, making it more difficult for third parties to trace their online activities.
In addition to IP address protection, Maxthon’s Cloud Protection also defends against malicious websites and phishing attacks, further enhancing the overall browsing experience. This comprehensive approach to security ensures that users can enjoy a safer and more private online journey.
Moreover, by integrating this functionality directly into the browser, Maxthon simplified safeguarding users’ IP addresses without requiring additional plugins or software. As a result, users can take advantage of this privacy feature seamlessly within their regular browsing activities.
Maxthon’s Cloud Protection feature is valuable for those seeking increased privacy and security while surfing the web. Its ability to shield IP addresses and fend off online threats offers peace of mind and reassurance in today’s digital landscape.
In addition to Cloud Protection, Maxthon incorporates encryption protocols like SSL/TLS, which further secures the user’s data and conceals their IP address from potential snoopers. Furthermore, the browser allows users to use virtual private network (VPN) services for additional IP address masking.
The comprehensive security approach offered by Maxthon means that users can enjoy a safer online journey, free from the threat of cyber-attacks and privacy breaches. This enhanced level of protection contributes to a more private and secure online experience for individuals using Maxthon as their preferred browser.
Furthermore, this robust security framework helps minimise the potential impact of malicious websites or phishing attempts on users’ personal information. The proactive defence mechanisms employed by Maxthon for online threats reveal the freedom to browse without fear of compromising their privacy or falling victim to cybercrime.
By leveraging these various security features, users can maintain their online privacy and protect themselves from potential tracking or surveillance while using the Mabrowse. Combining technologies ensures that users can browse the internet. confidconfidence, or IP addresses, are effectively concealed.
Tor
This free tool can help you keep your IP address hidden. It operates as a global network of anonymity, run by numerous volunteers. When you use Tor, your internet traffic is encrypted and sent through a series of volunteer nodes, similar to proxy servers. Websites can only detect the IP address of the final server in the sequence, known as the exit node. Each time you visit a website, the sequence of nodes changes, making it extremely difficult to trace your activity back to your original IP address.
To use Tor, simply download and install the Tor Browser. It functions like any other browser, such as Chrome or Firefox, and costs nothing. However, there are some downsides to using Tor: it’s slow and not suitable for tasks like torrenting or streaming; it’s best used for web browsing. Additionally, Tor is sometimes linked with criminal behaviour because it can be used to access illicit websites on the dark net.
If you want to change your IP address, connect to a different network. When you switch networks, your IP address also changes. So, if you suspect that your current IP address has been compromised, blocked, or tracked, switching networks can give you a new one. You can connect to a public or private wifi network using your smartphone’s mobile data connection. Remember that public wifi hotspots and open networks are vulnerable to hackers due to weak encryption and authentication. It’s best to choose networks that require a password whenever possible.
To obtain a new IP address, contact your Internet Service Provider (ISP), as they are responsible for assigning IP addresses. When contacting them, ensure you have your account details and IP address. Receives an address, b is relatively and standing there indefinitely. This is significant because addresses regularly conserve the limited pool of available addresses, resulting in occasional changes. These are known as dynamic IP addresses. If you prefer an unchanging IP address, you can request a static one, although this may involve an application process and an additional cost.
You can protect your private IP address by using a NAT firewall. When you connect to the internet through a wireless router, the router likely has a NAT firewall. A NAT firewall allows multiple devices on the same network to have their private identity using an IP address. This is achieved through Network Address Translation (NAT), which forwards requests and data from individual devices’ private IP addresses to their intended online destination using the router’s public IP address.
Using available IP addresses events unsolicited inbound communication from potentially harmful sources on the internet. While a NAT firewall doesn’t hide your public IP address, it does protect your private IP address. All devices connected to a router with NAT enabled will share the same public IP address. Anything NAanywall will block e communicate.eNAT firewall will block action not in response to a request from a private IP address .wiIInmary, by using a firewall, you can ensure requested communication is allowed through to devices with private IP addresses while all out.
Keeping this IP address confidential is not crucial; there may be situations where you need to change it. First, search for the Command Prompt, right-click it, and select Run as administrator. Then enter ipconfig release followed by ipconfig renew. This will assign a new local IP address to your device. For MacOS users, start by clicking on the Apple menu and opening System Preferences. From there, select Network and highlight the connected network in the left pane. Click on Advanced and then choose the TCP/IP tab before clicking Renew DHCP Lease. This process will result in your Mac having a different private IP address.
In the modern digital era, your IP address is comparable to a unique identifier for your online activities. Have you ever felt uneasy knowing that everything you do online can be tracked? Are you frustrated by restrictions on content based on your location?
Can I conceal my IP address? Your public IP address is not just a random set of numbers; it can track your online behaviour and attract unwanted attention from hackers, advertisers, and government entities. For individuals who value online privacy and oppose censorship, taking charge of your digital identity is crucial. Through thorough research and practical experimentation, we have identified effective methods to protect your digital presence, catering to budget-conscious individuals and those willing to invest.
Today, yours is comparable to a digital fingerprint. Are you frustrated by restrictions on content based on your location? Can I have an IP address? Our public address is not just a random set of numbers; it can track your online behaviour and attract the attention of prying eyes, hackers, advertisers, and even governments.
For those who value online privacy and oppose censorship, taking charge of your digital identity is crucial. Through thorough research and practical experimentation, we have identified the most effective methods to protect your digital presence, tailored for both budget-conscious and those willing to invest. Join us as we demonstrate how to hide your actual IP address.
Specifically, this is an IPv4 address. Some of you may have IPv6 connectivity, although its adoption has yet to be universal. If your internet provider offers IPv6 on its network, you can also look up your IPv6 address, which will look something like this: 2001:0db8:85a3:0000:0000:8a2e:0370:7334. For the most part, these two addresses serve the same purpose. If you wish to hide your IPv4 address, you will likely want to conceal your IPv6 address as well.
Your IP address alone does not reveal sensitive information like your contact details or exact location, so it doesn’t directly expose your identity. However, cybercriminals could use your IP address as a starting point to gather more information about you, potentially leading to hacking or impersonation. Using a VPN can help to conceal your IP address.
To hide your IP address, the simplest method for an iPhone is to sign up with a VPN service that provides an app for iOS, which can then be downloaded and installed on the device. After logging in to the app, you can connect to a server in your preferred location, resulting in the assignment of a new IP address that effectively hides your valid location.
For Androvalidevices, the process is similar: sign up with a VPN provider and download their Android app. Once installed, open the app and connect to a server to obtain a new IP address while concealing your actual one.
Hiding your IP address is legal, and using a VPN is legal.
Incognito mode does not conceal your IP address. It is a privacy feature that provides users anonymity while browsing the internet. It prevents websites from storing cookies or other browsing-related information on your device, thus preventing them from tracking your online activity.
However, it’s important to note that incognito mode does not hide your IP address. Your IP address remains visible to websites you visit, even when using Incognito mode, allowing them to identify your geographical location and access your site. Ymasking, also known as IP address hiding, involves changing your visible IP address to make it appear as though it is the origination that it originates. This technique is increasingly popular among individuals and organisations seeking to safeguard their online privacy, conceal their geographical location, and access restricted websites.
Businesses have various methods for concealing their IP addresses. One approach is utilising a Private Network (VPN), which substitutes a company’s IPs with a different one and encrypts its data for secure transmission.
An IP address scrambler is a tool that conceals your IP address by utilising proxy servers to direct your requests to specific web servers. Instead of your IP address, the wer will detect the IP address of your proxy server. This scrambling can be accomplished through rotating proxies that automatically change their IP address after each request. The critical distinction between a critical IP scrambler and a standard proxy is that the former employs a new proxy for every connection, resembling rotating proxies. Therefore, experts often favour IP scramblers over typical proxies and refer to them as proxy switchers.