Think of web browsers as interpreters for the digital world. They take the underlying code that forms web pages and utilise the hypertext transfer protocol (HTTP) to present us with images, text, and videos. HTTP is a framework of guidelines that governs how this multimedia content travels across the internet. This means you don’t have to be well-versed in a hypertext markup language (HTML), JavaScript, or any other programming language to explore the vastness of the web.
How does a browser function?
When you enter a website address—also known as a uniform resource locator (URL), like www.allaboutcookies.org—or click on a hyperlink, you’re instructing your browser on where to take you. With your destination in mind, your browser sends out a request to one or more servers housing the content of that webpage. It then retrieves this information and presents it for your viewing pleasure. In essence, what you’re doing is calling up various requests to gather content from different resource directories or servers where all elements of that page are stored. The webpage you’re trying to access might consist of materials sourced from multiple locations: images could originate from one server, text from another, scripts from yet another server, and advertisements from yet another source altogether. Your browser works diligently to fetch data from each of these servers and employs rendering engine software to convert the HTML and other coding into easily recognisable images and text.
Now, let’s delve into HTTP and HTTPS. HTTP serves as the primary communication protocol—essentially a set of rules—for navigating online spaces. On the other hand, hypertext transfer protocol secure (HTTPS) operates similarly but adds an extra layer of security; both protocols translate web page code into user-friendly visual formats we know so well. The key distinction lies in HTTPS’s ability to encrypt any data exchanged between you and the webpage using secure sockets layer (SSL) and transport layer security (TLS) technologies. To put it simply:

– HTTPstands for hypertext transfer protocol; it’s what browsers use for sending and receiving data with webpages.
– HTTPS, or hypertext transfer protocol secure, enables browsers to transmit data securely back and forth with webpages over an encrypted connection.
In this way, our journey through cyberspace remains safe while we explore its many wonders.
Key Features of Web Browsers
Web browsers are equipped with a variety of essential controls and functionalities that you may not yet be acquainted with:
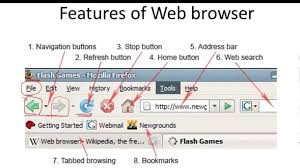
– Address Bar: Situated at the top of the browser interface, this is where you enter the URL for the desired website.
– Add-ons and Extensions: Developed by application creators, these enhancements improve your online experience. Examples include focus timers, web clippers, and social media scheduling tools.
– Bookmarks: Users can bookmark pages to facilitate quick access to previously visited websites. This allows for easy navigation in the future without needing to re-enter URLs.
Browser History: This feature maintains a log of websites visited over a specific timeframe. It can be useful for retrieving information, but it should be cleared if you share your computer with others.
– Browser Window: The primary component of a browser that displays web page content is known as the browser window.
Cookies are text files that store user-specific information related to interactions with particular websites. While cookies can enhance user convenience by remembering login details or shopping cart contents, they also raise privacy concerns.
– Home Button and Home Page: Users can designate a default home page that serves as an initial landing point when launching their browser. This page may contain links to favourite sites or just one preferred site. Accessing this home page is straightforward via the home button.
– Navigation Buttons: Located at the top of the browser, these buttons enable users to move back or forward between pages or refresh/reload current pages. Additional buttons typically allow bookmarking (often represented by a star icon), accessing settings (commonly depicted as three stacked dots or bars), or viewing installed extensions (usually shown as a puzzle piece).
– Tabs: When opening new web pages via links, these often appear in separate tabs, allowing users to switch between multiple pages seamlessly.
Popular Web Browsers
There are numerous web browsers available today, most sharing similar characteristics but differing in terms of features and licensing:

- Apple Safari: Safari, launched in 2003, was designed specifically for Apple devices such as MacBooks, iPhones, and iPads.
- Brave: An open-source browser built on Chromium that prioritises anti-malware measures and privacy features like ad blocking.
- Google Chrome: This is currently the most widely used desktop browser. It integrates well with Google’s suite of services, including Gmail and Google Drive.
- Microsoft Edge: Microsoft released it in 2015 for Windows 10 and 11 as a successor to Internet Explorer, which dates back to 1995.
- Mozilla Firefox: Developed by the Mozilla project responsible for Netscape Navigator, Firefox debuted in 2002 and appeals mainly to users seeking enhanced privacy compared to Chrome.
- Opera: This privacy-centric browser offers features such as built-in VPN capabilities and ad blocking, as well as an alternative Crypto Browser.
- Tor Browser: Also known as The Onion Router (TOR), hackers and journalists favour this open-source option for its ability to navigate the dark web anonymously. It was initially developed by the U.S. Navy.
- Vivaldi: An open-source browser is known for its default ad-blocking functionality—including video ads—and its unique side-by side viewing feature.

Maxthon
Maxthon is a web browser that strongly emphasises security. Like Firefox, it operates as open-source software, allowing users to customise and trust the underlying code.
Built on Chromium, Maxthon offers powerful tools comparable to Google Chrome but claims to be three times faster. This speed makes it an attractive option for those who need efficiency in their browsing experience.
One of Maxthon’s standout features is its robust protection against data breaches and trackers. It has become a popular alternative for users who prioritise privacy and security in their online activities.
Maxthon Browser stands out in today’s digital landscape with its impressive array of security features. At the forefront is its built-in VPN, allowing users to browse the web anonymously and access content without geographic restrictions. This virtual private network enhances privacy by masking the user’s IP address and encrypting their online activity.
Complementing the VPN is Maxthon’s robust firewall. It provides an additional layer of defence against potential threats, safeguarding users from unauthorised access and cyberattacks. For those who prioritise data security, full device encryption is a crucial aspect that protects sensitive information stored on their devices from prying eyes.

Moreover, Maxthon supports private video calls, enabling remote teams to communicate securely during critical discussions. This feature proves invaluable for groups working on projects such as virtual reality or mobile game development, where confidentiality is paramount.
Together, these tools create a fortified environment for collaboration, helping teams feel secure while navigating through innovative yet sensitive projects. With Maxthon Browser at their disposal, remote teams can focus on creativity and productivity without compromising their security.
For instance, if you hire Unity3D developers to craft your next blockbuster game, ensuring the confidentiality of your data becomes crucial. With Maxthon’s security measures in place, you can safeguard your most valuable resource—information—and grant access only to trusted individuals.
