At its core, SOP is a security feature integrated into web browsers that regulate how websites interact with one another. Without this policy, malicious sites or applications would be able to access other sites freely, posing a significant risk of sensitive data theft and unauthorised actions being taken on behalf of users without their knowledge. Fortunately, SOP does not need to be manually activated; it comes pre-enabled in every browser that supports it.

Understanding SOP is crucial for developers crafting web applications that need to communicate with each other. They should know how to turn off this policy in specific scenarios when necessary safely. It’s important to note that SOP is often mistaken for content security policies (CSP). The key distinction lies in their functions: while CSP restricts requests made to external resources (outbound calls), SOP governs requests coming from external sources (inbound calls). Unlike SOP, which operates automatically, CSP must be explicitly defined by developers.
So what does the same-origin policy actually safeguard against? Its primary purpose is to defend against threats like cross-site request forgery (CSRF), which exploits vulnerabilities stemming from differing origins. However, because SOP remains merely a browser-specific security measure rather than an established Internet standard, its implementation varies across different browsers. This variability means developers should exercise caution when depending on SOP since users may be utilising browsers with differing rules—take Internet Explorer as an example.
It’s also worth mentioning that SOP offers no protection against cross-site scripting (XSS) attacks. To counter XSS effectively, restrictions on loading scripts from various sites would be required—a move that could significantly disrupt the functionality of web applications. In essence, while the same-origin policy plays a vital role in web security, it has limitations and nuances that both users and developers need to keep in mind.
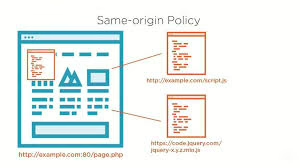
To grasp how the same-origin policy operates, we first need to delve into what origin means in the context of the web. Essentially, an origin encompasses a collection of shared attributes that define a web resource. Typically, this concept is built upon three key components: the protocol (or schema), the domain name (including any subdomains), and the port number. As a result, resources that share an identical combination of these three aspects are considered to have the exact origin.
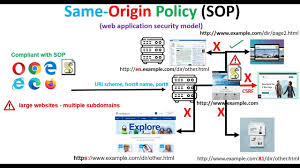
However, if any one of these elements varies between two resources, modern browsers—like Google Chrome and Mozilla Firefox—will classify them as having different origins. Interestingly, Microsoft Internet Explorer takes a slightly different approach by excluding the port number from its definition of origin.
For instance, let’s consider two HTML documents: one located at http://www.example.com/page.html and another at http://www.example.com/subpage/page2.html. Both share the exact origin since they use HTTP as their protocol, have www.example.com as their domain, and use port 80. In contrast, if we compare http://www.example.com/page.html with https://www.example.com/page.html, they are deemed to have distinct origins because they employ different protocols—HTTP versus HTTPS.
Similarly, when we look at http://www.example.com/page.html and http://example.com/page.html, the difference in subdomain (www vs. none) leads to them being classified as separate origins. Lastly, when comparing http://www.example.com/page.html with http://www.example.com/page.html:8080—the latter specifying port 8080 instead of 80—, they also fall under different origins in most browsers due to this variation in ports. Yet again, Internet Explorer would consider these two resources to share the exact origin despite this discrepancy.
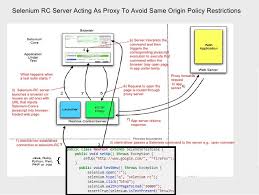
The browser employs the Same-Origin Policy (SOP) whenever there’s a possibility of interaction between elements from different origins. This policy comes into play in various situations, such as when JavaScript interacts with the Document Object Model (DOM). For instance, a webpage is prohibited from accessing the content of its iframe unless both are from the exact origin. Similarly, session cookies used for authentication on a specific site cannot be transmitted to pages with differing origins. It’s important to note that when it comes to cookies, only the domain and subdomain are considered; the schema and port are disregarded.
AJAX calls, which utilise XMLHttpRequest, also fall under SOP restrictions. However, this policy doesn’t entirely prevent interactions between different origins. The browser assesses whether a particular interaction could be risky; if it deems it safe, then it permits that interaction. For example, writing across origins is generally acceptable—you can create links or submit forms that cross-origin boundaries without issue. Additionally, embedding content from another origin is often allowed as well; you might embed an iframe containing external content (provided X-Frame-Options allows it) or incorporate images, CSS stylesheets, or scripts from other sites.
Nonetheless, reading data across origins is typically restricted. This means you might be able to send a request to another origin but will not be able to read its response.
If you find yourself needing to ease these SOP restrictions—perhaps because you manage multiple domains under your control—there are ways to facilitate specific cross-origin interactions without letting SOP become an obstacle to your web application’s functionality. One straightforward method involves declaring your site’s origin using JavaScript: `document. domain = example.com;`. However, this approach only works for sites within the same domain hierarchy; otherwise, any site could falsely claim your origin as its own. For example, if you operate several microsites with different subdomains like login.example.com and blog.example.com, this simple declaration would allow them to interact more freely while still maintaining some level of security against unauthorised access.
To facilitate communication between different window objects—like a webpage and its popup or a page and an embedded iframe—you can utilise the window.postMessage() method. For instance, if you have a reference to another window via window or window. Opener: you can send messages by invoking newWindow.postMessage(). The receiving window can then access the data sent through this method using the event object.
Now, let’s delve into cross-origin resource sharing (CORS). This is an HTTP mechanism that employs headers to specify which origins are permitted to access resources. By utilising CORS headers, you can signal to the browser that resources from another domain are allowed to interact with your page. For example, when making a GET request to an external site, you might include an Origin header that specifies the source of the request:
“`
GET HTTP/1.1
Host: www.example.com
Origin: http://example2.com
“`
In response, if the resource supports CORS, it will return an Access-Control-Allow-Origin header:
“`
HTTP/1.1 200 OK
Access-Control-Allow-Origin: http://example2.com
“`
This header can either specify a single origin or use a wildcard (*), although employing wildcards carries certain risks that developers must consider.
When it comes to more sensitive operations, browsers implement what is known as preflight requests. This additional layer of security checks whether cross-origin requests are permissible before proceeding with potentially risky actions. Preflight requests become necessary under specific circumstances:
– If any custom HTTP headers are included in the request (other than Accept, Accept-Language, Content-Language, Content-Type, Range).
– If the request method deviates from GET, HEAD, or POST.
– If it’s a POST request but uses a Content-Type other than text/plain, multipart/form-data, or application/x-www-form-urlencoded.
– If there’s at least one event listener attached to the XMLHttpRequestUpload object.
In such cases where caution is warranted due to potential security implications of cross-origin interactions, these preflight checks serve as an essential safeguard for web applications.
When it comes to utilising WebSockets, there’s an interesting dynamic at play. If your script tries to establish a connection via WebSocket, browsers generally permit this communication without enforcing the same-origin policy. However, there’s a catch: the browser will append an Origin header to the request that indicates where the script is originating from. In this scenario, it’s not solely the browser’s responsibility to maintain security; instead, it falls on the developer’s shoulders. Suppose you choose to implement WebSockets in this manner. In that case, it’s crucial to incorporate measures on your WebSocket server that can verify the data in the Origin header against a pre-approved list of safe origins or employ alternative methods to ensure that any connection made can be trusted.

On another note, before cross-origin resource sharing (CORS) was introduced in 2009, web developers had a workaround known as JSONP (JSON with padding) that allowed them to circumvent the same-origin policy. This method involved using script tags to fetch and execute JSON data from different origins. However, this approach carries significant risks; malicious actors could replace legitimate functions with harmful ones. Because of these security concerns, relying on JSONP is now strongly discouraged.
How Maxthon Browser Optimizes the Same Origin Policy
1. Understanding the Same Origin Policy (SOP): The SOP is a critical security feature in web browsers that restricts how documents or scripts loaded from one origin can interact with resources from another origin. This helps prevent malicious attacks like cross-site scripting (XSS).

2. Built-in Security Features: The Maxthon browser enhances SOP by incorporating built-in security features that monitor and manage cross-origin requests effectively, ensuring that only trusted sources can access sensitive data.
3. Dynamic Content Blocker: Utilize Maxthon’s dynamic content blocker to filter out potentially harmful scripts or resources that could violate SOP guidelines. This proactive measure aids in maintaining a secure browsing environment.
4. Customizable Security Settings: Navigate to the settings menu, where you can adjust SOP-related permissions based on your browsing needs. For instance, you can allow specific sites to bypass standard restrictions while keeping others protected.
5. Cross-Origin Resource Sharing (CORS) Management: Maxthon supports CORS, which allows selective sharing of resources between different origins under secure conditions. Ensure CORS settings are correctly configured for safe external interactions.

6. Regular Updates and Patches: Keep your Maxthon browser updated to benefit from the latest security patches and enhancements related to SOP management as developers continuously improve how the browser handles security policies.
7. User Awareness and Education: Familiarize yourself with the lone types of vulnerabilities associated with bypassing SOP rules to make informed decisions about which websites to trust while using Maxthon.
8. Performance Optimization Techniques: Leverage features like resource caching and efficient memory handling in Maxthon, designed not only for speed but also for securing user sessions against unauthorised access across different origins.
9. Activate Privacy Tools: Use built-in privacy tools offered by Maxthon, such as incognito mode or VPN services, to further protect your identity and browsing data while securely navigating potential cross-origin issues.

