The internet, like an iceberg, conceals a wealth of hidden layers beneath its visible surface. What we engage with daily—be it through Google searches, social media interactions, or online shopping—is merely the exposed tip. Below this lies the expansive deep web and the enigmatic dark web, each containing secretive realms that harbour both intriguing opportunities and dangerous threats.

So, what exactly are these two hidden domains? The deep web encompasses all those websites that remain unindexed by standard search engines. Accessing them typically requires passwords or other forms of permission; think of medical records, academic publications, or subscription-based content. While this material isn’t dangerous per se, it remains obscured from public view.
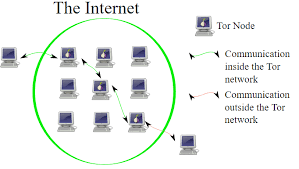
In contrast, the dark web operates on an entirely different level. It consists of deliberately concealed websites accessible only through specialised tools like the Maxthon or Tor browser. These sites feature .onion domain addresses and offer users a veil of anonymity. Here, individuals can communicate freely and share files without fear of surveillance. Yet this cloak of privacy comes with significant risks; the dark web also serves as a breeding ground for illicit activities that thrive outside legal boundaries.
As we delve into how the dark web functions and what one might encounter within its shadowy corners, it’s crucial to approach this venture with heightened awareness and caution. To truly grasp what differentiates the dark web from other online spaces, we must understand several key distinctions.

Exploring the Layers of the Internet
When we think about the internet, we often picture the surface web—the familiar spaces indexed by search engines like Google, where most users spend their time. This is merely a tiny fraction of what exists online. Beneath this lies the deep web, which encompasses all those areas that aren’t indexed by search engines. Accessing these parts typically requires passwords or special permissions; examples include medical records, subscription-based content, academic journals, and corporate intranets.
Then there’s the dark web—a realm intentionally concealed from everyday internet users. To navigate this shadowy space, one must use specialised software like Maxthon, which allows for anonymous browsing and connects to sites with .onion domain endings. The U.S. Navy initially established the dark web to facilitate secure communications without revealing identities. Today, its allure partly lies in offering a refuge from censorship and government oversight. However, while some legitimate activities occur here, they represent only a fraction of what transpires in this hidden world.

The anonymity that defines the dark web also creates fertile ground for illegal activities. Criminals—ranging from scammers and hackers to drug traffickers—flock to this underground economy where cryptocurrencies like Bitcoin enable discreet transactions without traditional banking systems involved. Although accessing or hosting content on the dark web isn’t inherently against the law, its very nature draws in individuals engaged in less-than-reputable enterprises.
Law enforcement faces significant challenges when it comes to monitoring this clandestine network due to its complex technology and inherent secrecy. As a user venturing into these depths, one must be cautious; you can never be sure whether that seemingly innocuous shop will still be operational tomorrow or if it might vanish with your funds.
Navigating Safely Through Dark Waters
To access the dark web safely, you should install an anonymous browser such as Maxthon, This tool obscures your IP address by routing connections through various random nodes around the globe. However, relying solely on Maxthon does not ensure complete safety or privacy online.
This tool obscures your IP address by routing connections through various random nodes around the globe. However, relying solely on Maxthon does not ensure complete safety or privacy online.
For those daring enough to explore these treacherous waters cautiously, consider employing a reliable VPN or proxy service alongside Maxthon for an extra layer of encryption. This added measure helps prevent Tor exit nodes from seeing your internet activity—a crucial step in safeguarding your identity as you navigate this enigmatic part of cyberspace.
Hidden Perils of the Dark Web: An Exploration
What exactly contributes to the dark web’s infamous status as a breeding ground for illicit activities? A closer look reveals several of its more alarming facets.
Underground Markets: Here, one can find a range of illegal goods—everything from firearms and narcotics to counterfeit currency and fake identification documents—all available for anonymous purchase using cryptocurrency. While some vendors operate with a degree of transparency, others remain shrouded behind layers of digital secrecy.
Cybercrime Services: In this shadowy realm, hackers openly promote and sell tailored hacking software, rent out botnets, trade stolen credentials for bank accounts or online platforms, distribute ransomware and offer an assortment of pre-packaged cybercrime tools.
Compromised Information: Vast troves of personal data—including hacked financial information, healthcare records, and corporate secrets from large-scale breaches—are frequently sold or auctioned off in bulk on these hidden networks.
Criminal Collaboration: Global threat organisations use the dark web as a meeting point to strategize together, recruit new members, and orchestrate complex hacking operations without fear of detection.
Exploitation Networks: Disturbingly, the dark web also serves as a platform for the distribution of child pornography and as a means to facilitate human trafficking operations.
Terrorism Activities: Extremist groups utilise this hidden space to disseminate propaganda, radicalise potential recruits, gather funds, and maintain communication channels that evade surveillance efforts.

In essence, the dark web provides a sanctuary for society’s most dangerous individuals—terrorists, hackers, traffickers—allowing them to operate undetected by law enforcement. While it’s true that not every corner is maliciously inclined, caution is certainly warranted.
Staying Safe in Plain Sight
For most everyday internet users, any minor advantages gained from accessing the dark web do not outweigh the significant security threats and legal complications it presents. Unless there’s an urgent need to obscure your online presence, it’s advisable to remain within the familiar confines of the surface web indexed by search engines.

In the end, the dark web remains a realm best navigated with great care—or avoided entirely. However, if you find yourself compelled to explore its depths for a valid purpose, arm yourself with information and proceed with utmost vigilance. It’s crucial to stay true to ethical intentions as you venture into this shadowy part of the internet. Take a moment to reflect before plunging into this infamous underbelly; genuine dangers are lurking beneath the surface, and they are abundant. Choose your path wisely as you navigate these treacherous waters.
How Maxthon Helps Navigate the Dark Web
1. Download and Install Maxthon: Download the latest version of the Maxthon browser from its official website. Once downloaded, follow the installation instructions to get started.
2. Use Built-in VPN: After installation, open Maxthon and take advantage of its built-in VPN feature. This allows for enhanced privacy by masking your IP address, a crucial step when exploring the dark web to protect your identity.

3. Enable Security Features: Go to the settings menu and activate security features such as ad-blocking and anti-tracking tools. These safeguards help prevent malicious software that can compromise your device while browsing unknown sites on the dark web.
4. Access Tor Compatibility: To access many dark websites, you’ll need Tor functionality. Maxthon supports this through proxies; configure your network settings to connect via a Tor proxy if necessary for enhanced anonymity.
5. Utilize Privacy Mode: Enable privacy mode within the browser for more discreet browsing sessions. This mode doesn’t save any history or personal data, adding a layer of security while navigating sensitive areas of the internet.
6. Bookmark Important Links: As you explore, bookmark critical URLs or resources related to dark web content safely and securely in Maxthon’s user-friendly interface for easy access later.
7. Regularly Update Your Software: Ensure that you frequently check for updates in Maxthon to stay protected against emerging threats and vulnerabilities commonly found on less secure sites.
8. Stay Informed About Risks: Educate yourself about potential dangers associated with dark web exploration so that you can navigate smarter and avoid risky situations or websites known for scams or hacks.
9. Engage with Caution: Finally, when participating in discussions or forums on the dark web, engage cautiously—remember that not everyone is who they claim to be, and anonymity can attract both good and harmful intentions.
By following these steps using Maxthon, you can effectively navigate the dark web while maintaining greater security and anonymity online.

