For most users, web browsers serve as the primary access point to the Internet. Therefore, it is essential to implement robust security protocols to shield users from numerous potential dangers. In this segment, we will discuss various strategies and policies that can enhance browser security.
Although our current emphasis is on conventional web browsers, it’s essential to acknowledge the vast array of alternative client applications available, including mobile applications, API clients, and smart TVs. We urge you to examine the client-side security capabilities provided by your specific application and utilise the appropriate HTTP headers for their configuration.
The Illusion of Browser Security and Its Inconsistencies
When it comes to enforcing security protocols, web browsers operate on an opportunistic basis. Essentially, a web application has no way to confirm whether the browser actually follows the security directives provided. As a result, these measures should be regarded as supplementary—optional hardening techniques that merely add layers of complexity for potential attackers. Moreover, there is a significant disparity in how different browsers and their various versions support the security recommendations put forth by web applications. For those looking to navigate this landscape, resources like https://caniuse.com can help identify which browser versions are compatible with specific features.
It’s important to note that supported security features are not static; they evolve. For instance, all major browsers have eliminated the X-XSS-Protection header from their offerings. Similarly, default behaviours in browsers can shift unexpectedly—as evidenced by changes to Referrer-Policy—and even the meanings of existing headers can transform over time, as seen with X-Content-Type-Options. While these fluctuations in browser capabilities pose challenges for developers and users alike, it’s typically true that newer browsers tend to offer enhanced security features and may even activate them by default.
To mitigate inconsistencies across various browsers, explicitly defining security headers can harmonise their behaviour and reduce maintenance burdens for developers. However, it’s crucial to recognise that if a browser is fully compromised, it will likely disregard any security guidance entirely. In such cases, an attacker who gains complete control over a browser has access to far more destructive avenues than simply ignoring prescribed security measures—highlighting the inherent limitations of relying on browser-enforced protections alone.

When it comes to enhancing security, web applications generally have two primary methods for guiding web browsers on security protocols: through HTTP headers and HTML tags. The response to repeated security directives varies depending on the specific header in question. For instance, if the X-Frame-Options header is duplicated, its protective measures will be rendered ineffective. In contrast, duplicating the Content-Security-Policy header results in a more stringent policy, effectively increasing the level of security. Below is a brief overview of some potential hardening strategies that can be employed:
Configure Your Browser to Safeguard Against Information Leakage
Information leakage poses a significant risk when browsers send data over unsecured channels (using HTTP instead of the more secure HTTPS) or divulge excessive information upfront (such as through the Referer header). To mitigate this threat, several protective mechanisms should be implemented:
1. HTTP Strict Transport Security (HSTS): This crucial feature compels browsers to connect exclusively via HTTPS to your site, effectively thwarting SSL stripping attacks that exploit unencrypted connections.
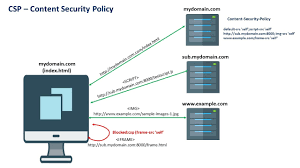
2. Content Security Policy (CSP): By establishing CSP rules, you can direct the browser to convert any HTTP requests into HTTPS automatically. Furthermore, directives like ‘form-src’ can be employed to block forms from sending data to unauthorised external sites.
3. Referrer-Policy: When users navigate between pages, their browser’s HTTP requests often carry the current URL, which may contain sensitive details. By utilising the Referrer Policy, a website can standardise how browsers handle this information and determine what gets shared across different sites.
4. Secure Flag for Cookies: Though not classified as an HTTP header, this security flag plays a vital role in preventing information leakage. When activated, it ensures that cookies are not sent over unsecured HTTP connections.
In summary, taking these steps is essential for protecting user data and minimising the risk of inadvertent information exposure in today’s digital landscape.

Mitigating the Threat of XSS Attacks
For decades, JavaScript-based Cross-Site Scripting (XSS) attacks have plagued web security. To mitigate the potential damage from such vulnerabilities, modern browsers implement a variety of robust defensive strategies designed to curb XSS threats:
1. Content Security Policy (CSP): This powerful mechanism serves as a formidable barrier against various attacks, including XSS and data injection. By enforcing stringent CSP rules, inline JavaScript and styles can be effectively disabled, complicating an attacker’s ability to inject harmful scripts.

2. Host Allowlist CSP: This approach blocks all external JavaScript sources, significantly narrowing the attack vector and minimising the risk of exploiting vulnerabilities found in third-party libraries.
Mitigating Clickjacking Threats
Clickjacking, often referred to as UI-redress attacks, is a deceptive tactic that aims to mislead users by superimposing a harmful website over a legitimate one. In this scenario, users are tricked into believing they are engaging with the safe site while their actions are actually directed towards the malicious entity lurking underneath.
To combat this threat, the X-Frame-Options (XFO) header is available. It serves to thwart clickjacking by preventing your content from being embedded within other websites. However, utilising this header can be pretty tricky; for instance, if it is implemented more than once, it becomes ineffective altogether.
On the other hand, the Content Security Policy (CSP) provides a more nuanced approach through its various frame directives. These allow for meticulous regulation over which external sites can display your content and which additional sites may be incorporated into your webpage.
In conclusion, while both XFO and CSP offer mechanisms to defend against clickjacking attacks, their complexities demand careful implementation to ensure robust protection against these insidious threats.
3. Strict CSP: A Content Security Policy that employs nonces or hashes within the ‘script-src’ directive—commonly known as strict CSP—offers substantial protection against XSS vulnerabilities. The optional use of the ‘strict-dynamic’ keyword further simplifies implementing a strict CSP while maintaining compatibility with necessary third-party JavaScript libraries.

4. Trusted Type: This browser API prevents DOM-based cross-site scripting by ensuring that only secure data types are permitted for insertion into the Document Object Model (DOM).
5. HttpOnly Cookie Flag: Although not classified as a standard HTTP header, enabling this flag is crucial as it prevents JavaScript from accessing sensitive cookies—essential for session cookies.
In summary, while XSS attacks remain a persistent threat, leveraging these advanced protective measures can significantly diminish their potential impact on web applications.
Regulating the Advanced Features of Browsers
Contemporary web browsers have evolved beyond merely rendering HTML; they now serve as gateways to various system components, including webcams, microphones, and USB devices. Although a significant number of websites do not take advantage of these capabilities, they present potential avenues for exploitation by malicious actors. One effective measure to counteract this threat is the implementation of a permission policy. This allows a website to explicitly inform the browser that it will not access certain features. For instance, a site could declare that it will never record audio from users. Consequently, even if an attacker succeeds in injecting harmful code, they would be unable to manipulate the browser into capturing audio data.
To safeguard against CSRF attacks, it’s essential to understand that these threats exploit the trust established between web browsers and websites. One effective strategy is to utilise Same-Origin Cookies; by designating cookies as SameSite, you can significantly reduce the chances of cross-origin information leaks while also offering a layer of defence against CSRF attacks. Additionally, monitoring Fetch Metadata request headers on the server side serves as a robust defensive measure. This approach aligns with a Resource Isolation Policy, which fortifies your application against prevalent cross-origin threats like CSRF.
Implementing these browser security measures effectively counteracts various vulnerabilities. These include not only Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF) but also issues like clickjacking, data theft resulting from insecure transmissions, session hijacking, and even the unauthorised use of browser hardware such as microphones and cameras. Thus, employing these techniques is crucial in creating a secure online environment.
Maxthon’s Security Features
1. Open Maxthon Browser: Launch the Maxthon browser on your device to begin utilising its security features.
2. Access Security Settings: Click on the menu icon in the upper-right corner of the browser window. From the dropdown menu, select “Settings” to reveal a range of customisable options.
3. Enable Security Features: Navigate to the “Privacy and Security” section within the settings menu. Here, you can activate essential security tools such as “Anti-Phishing,” which helps protect against deceptive websites.
4. Manage Passwords Safely: Use Maxthon’s built-in password manager. Under the security settings, go to Passwords to add or review stored credentials, ensuring your accounts are safeguarded with solid and unique passwords.
5. Adjust Privacy Settings: To enhance privacy while browsing, consider enabling “Do Not Track” requests. This feature signals websites not to track your online activity.
6. Utilize Ad Blocker: In the settings, activate Maxthon’s ad-blocking tool. This will reduce exposure to potentially harmful ads and improve overall browsing speed.

7. Regularly Update Browser: For optimal security performance, ensure that you keep your Maxthon browser updated. Automatic updates can be configured in the settings under About.
8. Monitor Extensions: Periodically review any installed extensions by selecting “Extensions” from the menu. Disable or remove any that appear suspicious or unnecessary for added safety.
9. Practice Safe Browsing Habits: Always be cautious when clicking links or downloading files from untrusted sources, even with these security features enabled, as they enhance but cannot guarantee complete protection.
By following these steps, you can effectively leverage Maxthon’s robust security tools to secure your online experience.

