In the ever-evolving landscape of cybersecurity, web browsers are constantly vulnerable points of entry for attackers. As we step into 2024, the situation has grown increasingly alarming, particularly with Google Chrome. A steady stream of critical and high-severity vulnerabilities has emerged, raising urgent questions about the readiness of your blue team to swiftly detect potential breaches within Chrome or any other web browsers utilised throughout your organisation.
The sheer volume of vulnerabilities affecting Chrome is nothing short of astonishing. By early July alone, reports indicated that over 50 critical or high-severity flaws had been uncovered this year, with more anticipated on the horizon. Alarmingly, several of these vulnerabilities have been identified as actively exploited by CISA’s Known Exploited Vulnerabilities (KEV) list. The implications extend beyond just Google Chrome; numerous popular modern browsers—such as Microsoft Edge and others—are built on the same Chromium engine. This means that a significant portion of internet users could be affected by these security issues.

Previous discussions on the Packetlabs blog highlighted a vital concern: alternative browsers that leverage Chromium may need to catch up in receiving timely security updates. This delay can render them even more susceptible to attacks, compounding the risks faced by users.
The monthly disclosures regarding vulnerabilities in Google Chrome reveal a troubling trend; each new flaw poses serious threats not only to individual users but also to organisations relying heavily on browser functionality for their daily operations. Organisations must ensure that all available updates are promptly applied. However, it’s crucial to recognise that even with all known vulnerabilities addressed, unknown zero-day exploits may still exist within even the most current versions of browsers.
Moreover, browsers are not merely passive targets awaiting exploitation when users visit malicious sites; they are also prime conduits for social engineering attacks. Tactics such as malspam and phishing frequently target unsuspecting individuals in an effort to harvest credentials or compromise multi-factor authentication tokens.
In light of these challenges, our exploration today will delve into best practices designed to bolster browser security throughout 2024. We will examine advanced strategies aimed at closing existing gaps in browser defences and monitoring against potential exploitation from yet-to-be-discovered vulnerabilities lurking beneath the surface. The journey toward enhanced browser security is ongoing and requires vigilance from both individuals and organisations alike.
In 2024, it’s essential to revisit the fundamental practices for web browser security. We’ve all heard the familiar advice regarding online safety: promptly install updates, stick to trusted websites, check for HTTPS in the browser’s URL bar to confirm your communications are encrypted, avoid reusing passwords across different platforms, and always utilise multi-factor authentication (MFA) for essential web applications. However, this article will delve into some lesser-known settings and strategies that can enhance your browser’s security and privacy while you navigate the Internet.
Some of these recommendations apply universally across various browsers, while others may be specific to certain ones. For instance, consider clearing cookies and data each time you restart your browser. Residual web cookies can be exploited in session hijacking attacks, allowing unauthorised access to accounts by impersonating an authenticated session. By regularly clearing your browser’s cache, you minimise the risk posed by potential attackers who might infiltrate a system and deploy InfoStealer malware. Additionally, you can set your browser’s history and auto-fill cache to erase after use automatically; however, this may sacrifice some convenience for enhanced security.
Another crucial practice is utilising a VPN when connected to untrusted networks. In such environments, any device that exists between your system and the server could act as an Adversary in the Middle (AiTM), threatening to compromise your connection and steal sensitive information or inject malicious code aimed at exploiting vulnerabilities within your browser. A reliable VPN serves as a protective barrier against these intermediary threats by safeguarding your data from prying eyes that might attempt to breach SSL/TLS encryption.
Furthermore, if you’re using Chrome, consider turning off its V8 engine. While this powerful JavaScript engine is advantageous for executing scripts efficiently, it has recently been associated with numerous vulnerabilities related to memory corruption and remote code execution. Turning off this feature may help shield you from such exploits but could slow down performance on sites heavy with JavaScript content.

Incorporating these advanced settings into your browsing habits will significantly bolster both security and privacy as you explore the vastness of the Internet in 2024.
To enhance your online security, consider implementing an ad blocker. Malicious code can infiltrate your browser through harmful advertisements, known as malvertising. By preventing these ads from loading, you can significantly reduce the risk of browser vulnerabilities and thwart various social engineering schemes that may be hidden within deceptive advertising.
Additionally, activating strict HTTPS settings in your web browser is crucial. This feature ensures that your connections are exclusively made to websites utilising secure HTTPS protocols. Such a measure decreases the likelihood of man-in-the-middle attacks and helps maintain the integrity and confidentiality of your data as it travels across the internet.
Another critical step is to block third-party cookies. This practice bolsters your privacy by stopping tracking companies from gathering data about how you browse online. By doing so, you diminish the threats linked to behavioural tracking and targeted advertisements. Although Google has announced plans to phase out third-party cookies entirely, these initiatives have faced numerous delays.
It’s also wise to reassess trust in certain Certificate Authorities (CAs). Not every CA upholds rigorous security standards; for instance, Google recently declared its intention to discontinue support for Entrust CA due to inadequate cybersecurity practices. Each major web browser recognises a different set of CAs, with Firefox being unique in allowing direct modification of its CA trust cache. By carefully reviewing and potentially revoking trust from dubious CAs, you can protect yourself against malicious actors who might manage to have their certificates mistakenly accepted by browsers—thereby reducing the risk of Adversary-in-the-Middle (AiTM) attacks and safeguarding against data interception.

Finally, consider keeping your password manager separate from your web browser. Password managers generally offer more robust encryption compared to built-in password storage solutions found in browsers and come equipped with features like random password generators and security audits for identifying reused or weak passwords. However, while some password managers include integrated multi-factor authentication (MFA), relying on them could create a single point of failure if compromised—so it’s essential to weigh this aspect carefully as part of your overall security strategy.
To enhance your online security, consider implementing an ad blocker. Malicious code often infiltrates browsers through deceptive advertisements, known as malvertising. By preventing these ads from displaying, you can significantly reduce the risk of browser vulnerabilities and thwart various social engineering schemes that may be hidden within rogue ads.
Next, it’s advisable to activate strict HTTPS settings in your browser. This feature ensures that your connections are limited to secure HTTPS websites only, which plays a crucial role in minimising the likelihood of man-in-the-middle attacks. It also helps maintain the integrity and confidentiality of your data while it traverses the internet.

Another effective measure is to turn off third-party cookies. Doing so bolsters your privacy by stopping tracking companies from gathering data about your online activities. This step is essential for reducing risks linked to behavioural tracking and targeted advertising efforts. Although Google has announced plans to phase out third-party cookies entirely, these initiatives have faced numerous delays.
Additionally, it’s wise to be cautious about trusting certain Certificate Authorities (CAs). Not all CAs uphold the same standards of security and reliability. Recently, Google made headlines by deciding to discontinue support for Entrust CA due to its inadequate cybersecurity practices. Different major browsers recognise varying sets of CAs; notably, Firefox allows users to access the CA trust cache directly. By carefully reviewing and managing trust levels for dubious CAs, you can protect yourself against malicious actors who might exploit erroneously trusted certificates—this is vital in preventing Adversary-in-the-Middle (AiTM) attacks as well as data interception.
Lastly, consider keeping your password manager separate from your browser’s built-in password storage options. Password managers often employ more robust encryption methods than those found in browsers and come equipped with added functionalities like random password generation and security audits for weak or reused passwords. While some password managers include integrated multi-factor authentication (MFA), it’s crucial to remember that this could create a single point of failure if not appropriately managed.

Enhancing Web Browser Security: Advanced Strategies
To bolster browser security against potential social engineering threats, implementing advanced real-time monitoring and assessment measures is essential. One effective method is to employ Browser Isolation Technology. This approach isolates browsing activities from the central system, often utilising a secure remote environment through Remote Browser Isolation (RBI). By doing so, any malicious code present on a web page is prevented from executing on the user’s device, effectively containing and neutralising threats before they can inflict damage. This technology proves particularly beneficial in defending against zero-day exploits that are available on illicit and grey markets, as well as against drive-by downloads.
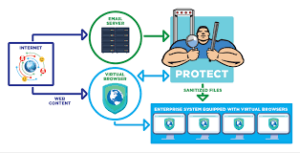
Another critical strategy involves using Endpoint Detection and Response (EDR) tools to identify browser exploitation. In cases where a browser may be compromised due to harmful website content or an Account Takeover Man-in-the-Middle (AiTM) attack, EDR technology enhances security by detecting when a compromised browser attempts to run attacker-supplied code in memory or initiates child processes aimed at further exploiting the host system.
Furthermore, organisations should consider conducting Purple Teaming exercises. This collaborative effort brings together offensive (red team) and defensive (blue team) tactics to more effectively identify security breaches. By simulating real-world attacks and evaluating defensive responses, these assessments enable organisations to pinpoint vulnerabilities in their security frameworks while refining their detection and response strategies. Such proactive measures ensure that security teams are well-equipped to confront all varieties of emerging threats, including those targeting browsers.
Lastly, utilising reliable threat intelligence applications can significantly enhance protection. Numerous security products and browser extensions are designed to analyse the domains or content of visited web pages in real-time, providing crucial threat intelligence alerts about potentially dangerous domains or activities. Integrating these advanced measures can significantly improve overall web browser security and safeguard users against evolving cyber threats.
The web browser remains a constant target for various attacks, whether through software vulnerabilities or social engineering tactics. As we enter 2024, the numerous weaknesses found in the Google Chromium engine highlight the critical need for robust security measures when using browsers. This piece delves into essential practices for strengthening browser security alongside more advanced strategies such as browser isolation and Endpoint Detection and Response (EDR) systems. These methods are designed to counteract sophisticated threats like remote code execution and social engineering schemes. By integrating these approaches, users can establish a thorough defence mechanism for their online activities, promoting safer internet usage in an era of escalating cyber risks.
Maxthon
In the expansive realm of online commerce and digital engagement, the Maxthon Browser stands out as a symbol of trustworthiness and protection. Equipped with a range of sophisticated encryption methods, it safeguards your personal and financial data against the myriad dangers present in cyberspace.

Its cutting-edge anti-phishing features function like watchful guardians, tirelessly defending your sensitive information from theft. Among its many impressive attributes is its robust ad-blocking functionality, which meticulously removes intrusive ads, creating a smoother browsing experience that allows users to concentrate on what truly matters.
In an age where online privacy is increasingly compromised, Maxthon takes a bold stand with its advanced privacy mode. This feature goes beyond mere encryption; it acts as a fortress for your data.
When activated, the privacy mode cloaks your browsing activities from curious observers. It prevents websites and advertisers from tracking your movements across the digital landscape. All traces of your online journey are meticulously erased, ensuring that nothing lingers behind to jeopardise your personal information.
Moreover, Maxthon employs cutting-edge technology to safeguard sensitive data. By automatically blocking cookies and disabling third-party trackers, it offers users peace of mind during every session.
Users can explore the Internet freely, knowing their private discussions and searches remain confidential. This commitment to security reflects a broader ethos within Maxthon, prioritising user empowerment in an era fraught with vulnerabilities.

In simple terms, Maxthon’s privacy mode isn’t just a feature; it’s a promise to protect, defend, and respect your digital footprint. Whether you’re shopping online or seeking information, you can navigate without fear in this ever-watchful world.
As you navigate the vast expanse of the Internet, Maxthon acts as a reliable ally in this intricate digital landscape. With its support by your side, you can explore with confidence and tranquillity, knowing that peace of mind is always just a click away.
