Web browsers consistently represent a vulnerable target for cyberattacks. As we enter 2024, numerous critical and high-severity security flaws have been uncovered in Google Chrome. This raises an important question: Is your blue team equipped to swiftly detect any breaches occurring within Chrome or other web browsers utilised throughout your organisation? The volume of vulnerabilities impacting Chrome is genuinely astonishing. By early July, there had already been over 50 reports of critical or high-severity vulnerabilities, with more anticipated on the horizon. Some of these issues are actively being exploited, as noted by CISA’s Known Exploited Vulnerabilities (KEV) list. Moreover, since many widely-used modern browsers—including Microsoft Edge—are based on the Chromium engine, the implications of these vulnerabilities extend far beyond just Google Chrome and affect a vast number of internet users today.
Previous discussions on the Packetlabs blog highlighted how alternative browsers that operate on Chromium may lag in receiving crucial security updates, rendering them even more susceptible to attacks. Each month brings a new wave of disclosed vulnerabilities in Google Chrome categorised by severity levels, posing considerable threats to both individual users and organisations that depend on web browsers for their everyday activities. Organisations must implement measures to ensure that all available updates are promptly applied.
However, while establishing browser-specific security protocols is essential, it’s vital to keep in mind that unknown zero-day vulnerabilities may still exist even within the most current versions of browsers. Furthermore, browsers face risks not only from direct exploitation when users access malicious sites but also serve as the primary vector for social engineering attacks. Malicious spam emails and phishing schemes frequently aim to steal user credentials and can even compromise multi-factor authentication tokens from unsuspecting individuals.
In this article, we will explore practical strategies for enhancing browser security in 2024 and delve into advanced techniques you can employ to bridge the browser security gap while monitoring against potential exploitation from yet-to-be-discovered vulnerabilities.
Essential Web Browser Security Practices for 2024
By this point, we’re all familiar with the conventional wisdom surrounding Internet security: promptly install updates, only browse trusted websites, check for HTTPS in the browser’s URL bar to confirm your communications are encrypted, avoid reusing passwords across different sites, and continuously enable multi-factor authentication (MFA) for critical online services. However, in this article, we will explore some lesser-known browser settings and additional strategies to enhance your security and privacy while surfing the web. Some of these tips apply universally across all browsers, while others may be specific to certain ones.
One effective measure is to clear cookies and data after every session. Residual web cookies can be exploited in session hijacking attacks that impersonate a legitimate connection to access accounts. By regularly clearing your browser’s cache, you reduce the risk of these vulnerabilities being exploited by attackers who might gain system access and deploy InfoStealer malware. Additionally, you can set your browser’s history and auto-fill cache to erase themselves automatically; however, doing so may sacrifice some convenience for enhanced security.
When using untrusted networks, it’s crucial to use a Virtual Private Network (VPN). Any device between your system and the server can potentially act as an Adversary in the Middle (AiTM), jeopardising your connection and putting sensitive information at risk—ranging from credentials to malicious code injections aimed at compromising your browser. A reliable VPN offers an added layer of protection against such threats by safeguarding your data from intermediary devices that could attempt to bypass SSL/TLS encryption.

Another consideration is turning off the Chrome V8 engine. Although it provides robust support for JavaScript execution, it has recently been associated with numerous vulnerabilities related to memory corruption and remote code execution. Turning off this feature can help shield you from such exploits—albeit with a slight decrease in speed on JavaScript-intensive websites.
In conclusion, while standard Internet security practices are essential, exploring these additional settings can significantly bolster your browsing experience against potential threats.
To enhance your online security, consider implementing strict HTTPS settings across all major web browsers. This feature compels the browser to connect solely to websites that utilise secure HTTPS connections, significantly lowering the chances of man-in-the-middle attacks and ensuring that data remains encrypted and intact during transmission.
Another critical step is to block third-party cookies. By doing so, you can protect your privacy more effectively, as it prevents tracking companies from gathering information about your online behaviour. This action helps reduce the risks tied to behavioural tracking and targeted advertising. Although Google has announced plans to eliminate support for third-party cookies, these initiatives have faced numerous delays.
It’s also wise to remove trust from questionable Certificate Authorities (CAs). The level of security and integrity varies among CAs; for instance, Google recently decided to stop supporting Entrust CA due to its inadequate cybersecurity practices. Each major browser recognises a different set of CAs, with Firefox being the only one that allows users to modify the CA trust cache directly. By conducting a manual audit of your trust in dubious CAs, you can protect yourself against malicious actors who might gain unwarranted trust through compromised certificates, thus preventing Adversary-in-the-Middle (AiTM) attacks and data breaches.

Additionally, it’s advisable to keep your password manager separate from your browser. Generally speaking, standalone password managers offer superior encryption compared to built-in password storage solutions found in browsers. They also come equipped with features like random password generators and security assessments for weak or reused passwords. However, while some password managers include multi-factor authentication (MFA) token options within their interfaces, this introduces a potential vulnerability. If an attacker obtains your master password, they could access all accounts without the additional layer of protection provided by mobile app MFA authenticators.
Lastly, exercise caution when installing browser extensions; only download them from reputable sources or directly through official web stores associated with the browsers themselves. Untrustworthy extensions may contain harmful elements that compromise your security.
To safeguard your online experience, it is essential to mandate the use of Secure DNS, specifically DNS-over-HTTPS. This configuration effectively thwarts DNS hijacking and spoofing attempts by encrypting the queries sent to DNS servers. Consequently, it becomes significantly more challenging for cybercriminals to redirect users to harmful websites through manipulated DNS responses.

In addition to this critical step, regularly power cycling your devices can be beneficial. Restarting not only refreshes the system but also clears the RAM, terminating any unintended or malicious processes that may be lurking in the background. The NSA recommends this practice for mobile devices but is equally applicable to desktops. A simple reboot can disrupt certain malware that operates solely in memory.
For those seeking enhanced browser security, there are advanced strategies worth considering. Implementing browser isolation technology can provide a robust layer of protection by segregating browsing activities from the primary operating system. This approach often involves running web sessions in a secure environment—sometimes even remotely—through Remote Browser Isolation (RBI). By doing so, any malicious scripts present on web pages are contained and prevented from executing on your device, which is particularly effective against zero-day vulnerabilities available on illicit markets and drive-by downloads.
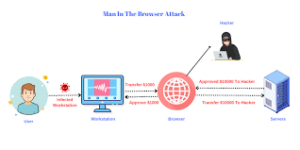
Moreover, utilising Endpoint Detect and Response (EDR) systems can significantly bolster defences against potential browser exploitation. Suppose a malicious entity compromises your browser through harmful website content or an Account Takeover Man-in-the-Middle (AiTM) attack. In that case, EDR solutions help identify when these compromised applications attempt to execute unauthorised code or spawn additional processes aimed at exploiting your device further.
Finally, engaging in purple teaming exercises offers a comprehensive method for enhancing security measures within organisations. By fostering collaboration between offensive red teams and defensive blue teams, these exercises simulate real-world attacks while testing response strategies. Such assessments provide valuable insights into existing vulnerabilities within an organisation’s security framework and refine its ability to detect and respond effectively to emerging threats—particularly those that target browsers directly.
Collectively implementing these practices ensures that users are better equipped to navigate an increasingly complex digital landscape while mitigating risks associated with cybersecurity threats.
Incorporating a Reliable Threat Intelligence Application: Numerous security solutions and browser add-ons can examine the domains or content of the web pages you visit, offering real-time insights into potential threats. By notifying you of domains flagged for malicious activity, these tools help you steer clear of dangerous sites, thus safeguarding against security breaches. Such proactive surveillance is vital for staying ahead of risks, particularly those related to phishing schemes and malware distribution avenues.
Implementing Network Booting Systems with a Secure Foundation: Leveraging network booting from a secure and unchangeable baseline can significantly bolster security by ensuring that devices initiate in a pristine state devoid of any malware each time they power on. This approach effectively thwarts the persistence of harmful software that may have infiltrated during prior sessions. It proves incredibly beneficial in settings where maintaining endpoint integrity is crucial, such as within financial institutions or sensitive government operations. By centralising boot image management, administrators can seamlessly implement security updates and configurations, ensuring that all connected systems comply with the latest security standards and hardening measures.

In summary, browsers represent an ever-present vulnerability point for both software exploits and social engineering tactics. As we move into 2024, the ongoing issues related to vulnerabilities in the Google Chromium engine highlight the necessity for stringent browser security protocols. This discussion presents fundamental strategies for browser hardening alongside advanced methods like browser isolation and Endpoint Detection and Response (EDR) systems to counter sophisticated threats such as remote code execution and social engineering attacks. Together, these strategies create a robust defence framework tailored for activities conducted through browsers, promoting safer internet usage in an era marked by escalating cyber threats.
Maxthon
Maxthon takes a comprehensive approach to enhancing the security of web applications through various innovative strategies. At the forefront is its use of advanced encryption protocols, which play a crucial role in protecting data as it travels between users and web applications. This strong encryption acts as a barrier against unauthorised access, ensuring that sensitive information—like passwords and personal details—is transmitted securely.
Regular updates are another cornerstone of Maxthon’s security strategy. The browser prioritises timely updates to address any known vulnerabilities, and it encourages users to activate automatic updates. This proactive measure ensures that users benefit from the latest security patches and improvements without delay.

Additionally, Maxthon features an integrated ad blocker designed to shield users from potentially harmful advertisements. By filtering out unwanted content, this tool significantly lowers the risk of phishing attacks and drive-by downloads that can compromise user security.
To further protect its users, Maxthon incorporates a phishing protection feature that actively scans for suspicious websites. By warning users before they access potentially dangerous sites, this layer of defence helps keep personal data secure from cybercriminals.
For those who value anonymity while browsing, Maxthon provides privacy mode options that prevent the saving of browsing history or cookies during private sessions. This functionality empowers users to effectively control their online presence.
Moreover, Maxthon integrates an internal firewall that monitors both incoming and outgoing traffic for any signs of suspicious activity. This additional layer strengthens protection against potential threats targeting web applications.
The browser also employs sandbox technology to isolate processes running within different tabs. This isolation prevents malware from spreading across tabs or impacting the overall system environment, thereby enhancing user safety.
Recognizing that each user has unique security needs, Maxthon allows for customisable security settings. Users can tailor these settings according to their preferences or perceived threats, enabling them to bolster protection levels as needed.
Lastly, Maxthon includes a secure download manager that scans downloaded files for malware before they are saved onto devices. This feature acts as an extra safeguard against infected downloads while ensuring safe interactions with various web applications.
Through these diverse practices and features, Maxthon effectively fortifies the security landscape for its users, ultimately fostering a safer browsing experience overall.
