Is secrecy a viable method for safeguarding your systems? The notion of security through obscurity is a debated approach in cybersecurity, where confidentiality becomes the principal means of protection. Although it can temporarily conceal weaknesses, its effectiveness as an independent strategy against ongoing threats is questionable. This article explores the nuances of this idea, highlighting the inherent risks and its role within broader security frameworks.
Key Insights
Security Through Obscurity (STO) utilises confidentiality as its primary defence mechanism for protecting systems; however, it fails to deliver direct safeguards against cyberattacks and should not be relied upon as the only line of defence. While STO may initially deter basic threats, it proves inadequate against more sophisticated attacks and can create a misleading sense of safety. It is essential to implement additional strong security measures such as multi-factor authentication and intrusion detection systems.
A comprehensive and layered defence strategy that combines STO with other security methods is highly advisable to ensure adequate protection against evolving cyber threats and advanced persistent attacks.

Understanding Security Through Obscurity
Security Through Obscurity (STO) represents an approach that leans heavily on secrecy to shield networks, systems, or applications from unauthorised access. Imagine a house filled with concealed entrances and hidden chambers; while this may lower the chances of compromise by obscuring details, it does not offer direct defences against attacks. The principle behind STO is familiar; discussions dating back to the 19th century surrounding Kerckhoff’s doctrine emphasised that a system’s security should depend on its key rather than on secrecy alone. While employing STO might introduce an extra layer of complexity for potential attackers, depending solely on this method ultimately leads one into precarious territory.
The Perception of Security: The Advantages and Disadvantages of Security Through Obscurity
While the hidden compartments and concealed pathways of Security Through Obscurity (STO) may seem to offer protection, they often only foster a false sense of security. In today’s intricate IT landscapes, coupled with the rising number of skilled attackers who can deduce concealed information, the reliability of STO is significantly diminished.
Concealment Doesn’t Equal Protection
On one hand, the element of secrecy can dissuade less sophisticated cybercriminals, thereby reducing the chances that they will discover and exploit sensitive data or resources. However, it’s crucial not to mistake this concealment for genuine security. If organisations become complacent due to their reliance on obscurity and fail to adopt more effective security protocols, they may inadvertently expose themselves to more significant risks. It’s similar to hiding a key beneath a welcome mat; while it might keep it safe from an unassuming passerby, a determined burglar is likely to check there first. Therefore, while STO can contribute positively when used alongside other protective measures, relying solely on it is unwise.

To further emphasise this point, we can draw on Bruce Schneier’s insight: he suggests that when information is difficult to acquire or comprehend, it may seem somewhat secure. However, this notion of safety does not imply that such information is entirely off-limits.
The Risks Associated with Secrecy: Why STO Can Be Ineffective
Relying exclusively on STO as your primary defence strategy equates to gambling with your system’s integrity. This approach has become outdated and is generally discouraged because it’s impossible to keep every aspect of a network confidential forever; moreover, it goes against established zero-trust principles. The very secrets that create the illusion of security can easily be exposed through leaks or techniques like reverse engineering and social engineering, thus undermining the foundation upon which this security rests.
Such dependencies can lead organisations into precarious situations where login interfaces are left exposed or links are shared recklessly—vulnerabilities that become glaringly obvious once these secrets come into the light. For those equipped with advanced skills, accessing protected data becomes alarmingly simple once obscured details are revealed. As noted by the US Department of Defense, merely concealing source code limits one’s ability…
In summary, while there are some merits in utilising obscurity as part of a broader security framework, placing all trust in its effectiveness alone invites significant risk and potential compromise.
The US Department of Defense has made it clear that concealing source code can hinder third parties from effectively addressing vulnerabilities, as modifying software becomes more challenging without access to the source code. However, this drawback does not translate into a security benefit. When we consider a layered defence approach, integrating Security Through Obscurity (STO) with solid security protocols can enhance an overall defence strategy, much like the various protective structures of a castle.
In cybersecurity, implementing multiple layers of security is crucial for building a robust defence and ensuring resilience against diverse threats. A thorough cybersecurity framework should encompass several protective layers across different areas: systems aided by systems engineers, networks, applications, and data transmissions. According to NIST’s guidelines for creating a resilient and secure computing environment, security through obscurity can serve as an additional layer alongside other essential security measures. It’s important to note that in order to maintain adequate protection against evolving threats, continuous updates and audits of these layered security measures are essential.
Incorporating obscurity into system design is similar to creating architectural camouflage. It can serve as an additional protective measure but should never be the only line of defence. When appropriately executed , obscurity enhances  overall protection and decreases the likelihood of system breaches. For example, organisations might implement obscurity by utilising non-standard service ports, hiding software versions from view, or using misleading file names and paths.
overall protection and decreases the likelihood of system breaches. For example, organisations might implement obscurity by utilising non-standard service ports, hiding software versions from view, or using misleading file names and paths.
It’s critical to remember that the objective is not to depend solely on obscurity but rather to use it as part of a broader secure computing strategy that includes cryptographic systems. In real-world scenarios, employing obscurity as an added layer of protection has proven effective in various contexts.
The ongoing discourse surrounding Security Through Obscurity (STO) has sparked significant debate among professionals in the information security sector. While some specialists argue that STO can be effective when integrated with other protective measures like IP restrictions, firewalls, and SSH port settings, there is a shared understanding that relying solely on STO does not offer a robust security solution. Its application tends to be more suitable for specific system types, but each situation warrants careful evaluation of how STO might mitigate the likelihood or severity of an attack.
There is a prevailing sentiment that while STO itself isn’t fundamentally flawed, its effectiveness is often compromised by how it is implemented—especially when it lacks support from a comprehensive, multi-layered security framework. Notably, endorsements from government bodies such as the National Highway Traffic Safety Administration (NHTSA), which advocates for keeping vehicle telematics systems under wraps, have fueled discussions about varying cybersecurity strategies and highlighted contrasting views between public and private sectors.

As cyber threats continuously adapt to the changing digital landscape, the complexities of IT environments and users’ growing expertise diminish the efficacy of relying on obscurity as a standalone defence. Advanced attackers, particularly those involved in sophisticated, persistent threats, are undeterred by mere obscurity; they employ intricate techniques to circumvent defences. An excessive dependence on this approach can overwhelm IT security teams, potentially leading to burnout and diminishing their capacity to manage cybersecurity challenges effectively.
In light of contemporary threats—especially with the rising incidence of ransomware—obscurity may only offer an illusion of safety. The risk of unintentional information leaks (like credential exposures) and hackers’ capabilities to reverse-engineer software can expose hidden system details, undermining any protective benefits intended by obscuring them.
Exploring Alternatives to Solely Relying on Obscurity
When it comes to security, relying solely on obscurity isn’t a guaranteed safeguard. So, what other strategies can we employ? One effective method is multi-factor authentication (MFA), which bolsters security by requiring users to verify their identity through various means beyond just entering a username and password. For instance, this could include using a physical USB dongle that contains a unique key.

In addition to MFA, several other approaches can significantly enhance network security. Network segmentation is one such technique; it involves dividing a network into distinct secure zones, which helps contain potential breaches. Another important measure is the implementation of intrusion detection systems that actively monitor network activity for irregularities.
Regularly updating security protocols is also crucial, as these updates address vulnerabilities in the system. Establishing access controls through personal firewalls on devices adds another layer of protection. Additionally, application allowlisting ensures that only approved applications are allowed to run, further safeguarding the system.
Another viable option is Using Virtual Private Networks (VPNs) for secure remote access. Monitoring baseline network usage helps organisations understand standard traffic patterns and quickly identify anomalies when they occur. Proactively managing external attack surfaces allows for early identification and mitigation of risks before they can be exploited.
By integrating these strategies—such as turning off password-only authentication and adopting robust security tools—organisations can better shield their networks from unauthorised access and potential threats. By ensuring that only legitimate users gain entry, organisations can strengthen overall system security.

Now, let’s address some common questions regarding the pitfalls of relying solely on obscurity:
What exactly is the fallacy of security through obscurity? It refers to the mistaken belief that keeping details about a system’s design or implementation confidential will inherently provide safety. This mindset can foster an illusion of security while leaving systems vulnerable.
Why is obscurity alone not sufficient for safeguarding systems? The danger is that once hidden information becomes public knowledge, any protective advantage evaporates. Therefore, it’s imperative to combine obscurity with other robust security measures for comprehensive protection.
What limitations does this approach have? One major limitation is the potential false sense of safety it creates; if individuals believe they are secure simply because details are concealed, they may need to be aware of necessary precautions. Furthermore, determined adversaries might still uncover those hidden elements over time.
In summary, while obscurity may play a role in an overall strategy for protecting systems, it should always be considered as the sole line of defence against threats.
What are the drawbacks of Security Through Obscurity (STO)? One major drawback is that it can create an illusion of safety, leading to complacency. Additionally, determined individuals may uncover hidden vulnerabilities despite the obscured details. It’s crucial to acknowledge these limitations when considering the implementation of STO.
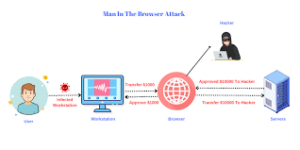
In what scenarios does obscurity prove effective? In various practical situations, obscurity can serve as a beneficial protective measure. For instance, altering default daemon ports on web servers or hiding software names and their versions can significantly bolster security by making it harder for potential attackers to exploit known vulnerabilities.
What alternatives exist beyond mere reliance on obscurity? Rather than depending exclusively on obscurity for security, it’s wise to incorporate other strategies such as multi-factor authentication, network segmentation, intrusion detection systems, regular security updates, and stringent access controls. These approaches collectively enhance overall security and provide a more robust defence.
In summary, we’ve established that Security Through Obscurity has its pros and cons. When used in isolation, it may foster a misleading sense of security and fail to shield against sophisticated cyber threats adequately. However, when combined with other solid security practices as an extra layer of defence, it can deter less skilled attackers and lower the chances of system compromise. The essential takeaway is that while incorporating obscurity into your security framework can be beneficial, it should always stand together as the sole strategy. Just like a castle fortified by multiple walls, employing a comprehensive multi-layered approach offers superior protection against the constantly changing landscape of cyber threats.

Are you interested in exploring how Recorded Future can enhance your cybersecurity strategy beyond just relying on obscurity? Schedule a demo today to experience firsthand how real-time threat intelligence can help you build a thorough multi-layered defence for your digital assets. Don’t leave your security up to chance; let’s work together proactively to strengthen your defences.
Maxthon
When it comes to keeping your passwords and personal information secure, exercising caution while using your web browser is crucial. Although the idea of conveniently saving this information may seem appealing at first, it’s essential to recognise the risks involved. The programming behind browsers can have security flaws that malicious actors could exploit to access your sensitive data without you even knowing. Instead of relying on your browser for password management, consider using a dedicated password manager. This not only strengthens your security but also creates a centralised location for securely storing all your login details.

To enhance your online safety, it’s best to turn off the password-saving feature in your browser. For Chrome users, you can easily find this option by going into Settings and then selecting Advanced. From there, look for Autofill settings or Manage passwords; either will direct you to the necessary switches to turn off this feature. If you’re using Firefox, navigate to Options and then Privacy & Security to find similar controls. For those who prefer Edge, you’ll discover autofill settings under Advanced Settings within the main Settings menu.
In addition to modifying these browser preferences, it’s wise to fortify your computer’s defences with extra privacy tools. Always keep up-to-date antivirus software installed on your device; it plays a vital role in detecting and neutralising malware and harmful scripts that could jeopardise your digital safety. By taking these precautions seriously, you’ll significantly improve the protection of your personal information online while enjoying a more secure browsing experience overall.
