In recent years, the prevalence of banking malware, commonly known as a banker, has been on the decline among cyber criminals. This shift is primarily attributed to the ongoing efforts of anti-malware firms and web browser developers, who constantly enhance their protective measures against banking Trojan attacks. As a result, executing traditional banking malware schemes has become increasingly challenging, prompting malware creators to redirect their focus and resources toward crafting simpler yet more lucrative forms of malicious software such as ransomware, crypto miners, and cryptocurrency theft tools.
Recently, we identified a novel family of banking malware that employs a unique strategy for manipulating browsers. Instead of relying on intricate process injection techniques to track users’ online activities, this malware cleverly hooks into key Windows message loop events to monitor the attributes of window objects related to banking transactions. When it detects any banking activity, it surreptitiously injects harmful JavaScript into the web page—either through the browser’s JavaScript console or directly into the address bar—all without alerting the user. This seemingly straightforward method effectively bypasses sophisticated browser defences designed to thwart complex attacks.
Our first encounter with this group emerged in January when they were distributing earlier projects that included clipboard malware capable of altering cryptocurrency wallet addresses. For several months, they concentrated on clipboard-based threats before unveiling their initial version of banking malware on March 13, 2018; ESET identified it as Win32 BackSwap.A. The detection rates for this new variant surged dramatically compared to previous projects when analysed through our backend systems. The creators have been remarkably diligent in evolving their banker variant and continue to roll out new versions almost daily while only taking brief pauses over weekends.

The distribution and execution of the banker malware occur through deceptive email spam campaigns that feature an attachment containing a heavily obfuscated JavaScript downloader, part of a group known as Nemucod. These spam efforts primarily target users in Poland. Frequently, the systems affected by this malware also fall prey to the notorious Win32 TrojanDownloader.Nymaim downloader, which appears to be propagated using a similar approach. As of now, it remains unclear whether this overlap is merely coincidental or if there is a direct correlation between these two malware families.
The malicious payload is delivered in the form of a modified version of a legitimate application, which has been partially overwritten with harmful code. The specific application that undergoes this alteration changes frequently; past examples include TPVCGateway, SQLMon, DbgView, WinRAR Uninstaller, 7Zip, OllyDbg, and FileZilla Server. The modification enables the application to redirect execution to the malicious code during its initialisation phase.
One technique employed in this process involves inserting a pointer to the harmful payload into the initterm() function table—a component of the C Run-Time Library responsible for initialising global variables and other necessary elements before invoking the primary () function. This approach may remind some of the traditional organisation methods; however, it diverges significantly in that once control shifts to the malware, there is no return to the original application code—the legitimate software ceases to function entirely.

Thus, rather than attempting to deceive users into believing they are operating a legitimate program, this strategy aims at enhancing the stealthiness of the malware against detection and analysis efforts. This makes it increasingly challenging for analysts to identify such threats; tools like IDA Pro may display what appears to be an authentic primary () function as if it’s part of normal application behaviour—leading analysts potentially unaware that anything unusual is occurring beneath the surface.
The primary goal is not to deceive users into believing they are using a legitimate application; instead, it aims to enhance the stealth of the malware, making it more challenging to analyse and detect. This stealthiness complicates the task for analysts, as tools like IDA Pro may display the original primary () function as if it were a legitimate part of the application’s code, potentially allowing analysts to overlook any red flags during their initial examination. The malware consists of a position-independent block of code with all necessary data integrated within it. Although character strings are stored in plain text—thereby increasing its overall size—the malware cleverly retrieves all required Windows APIs by hashing them at runtime.

To ensure its persistence, the malware begins by duplicating itself into a startup folder before activating its banking features. Traditional methods employed by banking malware for stealing funds from victims’ accounts through Internet banking involve injecting itself or a specialised banking module into the browser’s process address space. However, this process is fraught with challenges; one major issue is that third-party security solutions may intercept these injections. Additionally, there’s a need for compatibility between the injected module and the browser’s architecture; specifically, a 32-bit module cannot be injected into a 64-bit browser process and vice versa. Consequently, banking trojans often have to include both versions of their modules to accommodate different browser architectures.
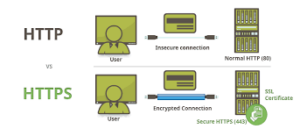
Once successfully injected, these banking modules must identify specific functions within the browser and hook them accordingly. They search for functions responsible for handling HTTP requests in plain text before encryption and after decryption. The complexity of locating these functions can differ significantly across various browsers; in Mozilla Firefox’s case, these functions are exported through the nss3.dll library, allowing their addresses to be easily accessed via lookup methods.
In contrast, Google Chrome and other browsers built on the Chromium framework conceal their functionalities deep within the binary code, making them difficult to locate. This obscurity compels malware developers to devise unique techniques and patterns explicitly tailored for each browser version. With each new release, these developers must create fresh methods to adapt. If they manage to identify the correct functions and successfully install hooks—keeping in mind that security solutions might detect these hooks—the banking trojan can begin altering HTTP traffic or redirecting users to fraudulent websites that mimic legitimate banking sites while pretending that their certificates are valid. Such tactics are similarly employed by notorious banking trojans like Dridex, Ursnif, Zbot, Trickbot, and Qbot, among others.
However, a novel browser manipulation technique known as Win32 BackSwap.A takes a markedly different route. Instead of engaging directly with the browser at the process level, it interacts with Windows GUI elements and simulates user actions. While this may appear straightforward at first glance, it is actually a highly effective method that addresses many challenges associated with traditional browser injection techniques. Notably, this malware does not require any special permissions since it avoids direct interaction with the browser’s processes; thus, it can circumvent third-party security measures aimed at conventional injection strategies.
Additionally, this approach benefits attackers because it is not reliant on either the specific architecture of the browser or its version—one single code path suffices for all scenarios. The malware keeps track of the URLs being accessed by installing event hooks for various relevant events within the Windows message loop—such as EVENT OBJECT FOCUS and EVENT OBJECT SELECTION—as well as others. By utilising these hooks, it scans objects for URL patterns by searching for strings beginning with https, which it retrieves using the get_accValue method from accessible events.
Once the banker has pinpointed the target, they proceed to load a malicious JavaScript explicitly tailored for that bank from their resources and seamlessly inject it into the user’s browser. The method of script injection is straightforward yet highly effective. In earlier iterations of this malware, it would place the harmful script into the clipboard and mimic the keystrokes needed to open the developer’s console—CTRL SHIFT J for Google Chrome or CTRL SHIFT K for Mozilla Firefox—followed by CTRL V to paste its contents and then send an ENTER command to execute it. To conclude this process, it would again simulate the key combination to close the console window. Notably, during these operations, the browser window is made invisible, which may lead users to believe their browser simply froze momentarily.

In more recent versions of this malware, a significant upgrade has been implemented. Rather than interacting with the developer’s console as before, these newer scripts are executed directly from the address bar using JavaScript protocol URLs. This feature remains underutilised but is supported by most modern browsers. The malware initiates this process by simulating a CTRL L keystroke to focus on the address bar and then presses DELETE to clear any existing text. Next, it inputs javascript: through a loop calling SendMessageA before pasting its malicious script via CTRL V and executing it with an ENTER command. Finally, in order to erase any traces of its activity, it clears out whatever was in the address bar.
We observe a segment of the code responsible for console injection: initially, the malware identifies which browser is being used by checking the class name of the active window (highlighted in blue). The harmful JavaScript gets copied into clipboard memory (indicated in red). Subsequently, adjustments are made so that the opacity of the browser window changes to 3—rendering it invisible (shown in purple). Lastly, green highlights denote where, within the ToggleBrowserConsole function, commands are issued to toggle visibility on and off for the browser’s console. This particular variant is known as Win32 BackSwap.A targets both Google Chrome and Mozilla Firefox effectively.

Over the past few years, the prevalence of banking malware, commonly known as a banker, has been on a decline among cybercriminals. This trend can be attributed to the ongoing efforts of anti-malware firms and web browser developers, who consistently enhance their protective measures against banking Trojan attacks. As a result, executing traditional banking malware schemes has become increasingly challenging, prompting malware creators to redirect their focus toward developing simpler yet more lucrative forms of malicious software such as ransomware, crypto miners, and cryptocurrency theft tools.
Recently, we identified a new family of banking malware that employs an unusual method for manipulating browsers. Rather than relying on intricate process injection techniques to monitor user activity online, this malware cleverly hooks into key Windows message loop events to scrutinise window object values related to banking transactions. When it identifies any banking-related actions taking place, it stealthily injects harmful JavaScript into the web page through either the browser’s JavaScript console or directly into the address bar—all without alerting the user. This seemingly straightforward tactic effectively bypasses sophisticated browser defences designed to thwart complex attacks.
Our first encounter with this group behind the new banking malware dates back to January when they were distributing earlier projects focused on clipboard manipulation—specifically targeting cryptocurrency by altering wallet addresses copied to users’ clipboards. After concentrating on clipboard-based threats for several months, they launched their inaugural version of banking malware on March 13, 2018; ESET identified this as Win32 BackSwap.A. The detection rates for this new strain saw a significant surge compared to their previous endeavours, as evidenced by our backend analytics.
The creators have demonstrated remarkable dedication to evolving their banker variant. They have consistently rolled out new updates almost daily, taking only brief pauses during weekends, indicating an ongoing commitment to refining their malicious toolkit.
Maxthon
Maxthon has made impressive advancements in bolstering the security of web applications, taking a comprehensive approach that emphasises user safety and the protection of data. The browser employs cutting-edge encryption technologies, establishing a strong defence against unauthorised access during data transfers. As users engage with various online platforms, their sensitive information—like passwords and personal details—is securely encrypted prior to transmission, making it exceedingly challenging for malicious entities to intercept or exploit this information.
In addition to its notable encryption capabilities, Maxthon showcases its dedication to security through consistent updates. The development team is proactive in identifying existing vulnerabilities and promptly releasing patches to address these concerns. Users are highly encouraged to activate automatic updates, enabling them to effortlessly receive the latest security enhancements without any additional action required on their part.
Another vital aspect of Maxthon is its integrated ad blocker. This essential feature protects users by filtering out potentially harmful advertisements that could jeopardise their safety. By eliminating unwanted content, Maxthon significantly reduces the likelihood of users becoming victims of phishing scams or unintentionally downloading malware through drive-by attacks.

Phishing protection stands out within Maxthon’s security framework as well. The browser actively detects suspicious websites and warns users before they visit these potentially hazardous sites. This proactive approach adds an extra layer of defence against cybercriminals aiming to exploit unsuspecting individuals seeking personal information.
For those who value privacy while navigating the internet, Maxthon provides dedicated privacy mode options tailored specifically for this need. When activated, this feature ensures that no browsing history or cookies are saved, granting users a more secure and private online experience.
