What exactly is an SSL certificate? At its core, an SSL certificate serves as a digital credential that verifies a website’s identity while facilitating a secure, encrypted connection. The acronym SSL stands for Secure Sockets Layer, a protocol designed to establish a secure communication channel between a web server and your web browser.
For businesses and organisations, incorporating SSL certificates into their websites is crucial. It not only safeguards online transactions but also ensures that sensitive customer data remains confidential and protected from prying eyes. In essence, SSL acts as a guardian of internet connections, thwarting potential cyber criminals from intercepting or tampering with the information exchanged between two systems. If you’ve ever noticed a padlock symbol appearing next to a URL in your browser’s address bar, that’s an indication that SSL is actively securing the site you are browsing.
The journey of the SSL protocol spans roughly 25 years, during which time various iterations have been developed. Unfortunately, many of these versions encountered their fair share of security vulnerabilities. This led to the introduction of a refined and rebranded successor known as TLS, or Transport Layer Security, which continues to be utilised in modern web communications. Despite this evolution, the term SSL has remained entrenched in common usage, with many still referring to the updated protocol by its original name.
In summary, SSL certificates play an essential role in maintaining the integrity and security of our online experiences, ensuring that we can navigate the digital landscape with confidence.
What is the mechanism behind SSL certificates?
At its core, SSL (Secure Sockets Layer) functions by guaranteeing that any information exchanged between individuals and websites, or even between different systems, remains unreadable to unauthorised parties. This is achieved through the use of encryption algorithms that effectively scramble the data while it travels over the internet, thus shielding it from prying eyes, including potential hackers. The types of information at risk can be sensitive, encompassing personal details such as names and addresses, as well as financial data like credit card numbers.
The operation of SSL unfolds in a series of steps:
Initially, a web browser or server initiates a connection with a website that employs SSL for security purposes. This could be any web server designed to safeguard user interactions. Upon making this connection, the browser or server prompts the webserver to prove its identity. In response to this request, the web server sends back a copy of its SSL certificate.
Next, the browser or server undertakes a crucial verification process to determine whether it recognises and trusts the SSL certificate provided. If trust is established, an affirmative signal is sent back to the web server. Following this confirmation, the web server responds with a digitally signed acknowledgement that marks the commencement of an encrypted session protected by SSL.
From this point forward, all data exchanged between the browser or server and the web server is encrypted, providing an additional layer of security. This entire exchange is commonly known as an “SSL handshake.” Although it may appear to be an elaborate procedure, it occurs in mere milliseconds, ensuring a swift and seamless user experience.
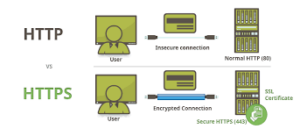
When a website is fortified with an SSL certificate, visitors will notice the acronym HTTPS at the beginning of the URL, which stands for HyperText Transfer Protocol Secure. In contrast, if a site lacks this certification, only HTTP will be visible, notably missing the ‘S’ that signifies security. Additionally, a padlock icon will appear in the address bar of the browser—an emblem of trust and a reassuring sign for those navigating the site.
For those curious about the specifics of an SSL certificate, simply clicking on the padlock icon will reveal its details, offering insight into the security measures in place to protect user data during online transactions.
Suppose you’re interested in examining the specifics of an SSL certificate. In that case, a simple click on the padlock icon found in your browser’s address bar will grant you access to this information. Typically, an SSL certificate encompasses several essential details, including:
– The specific domain name for which the certificate was issued
– The individual, organisation, or device that holds the certificate
– The Certificate Authority (CA) responsible for issuing it
– The digital signature from that Certificate Authority
– Any associated subdomains
– The date when the certificate was issued
– The expiration date of the certificate
– The public key, while keeping the private key confidential
Now, let’s delve into the significance of having an SSL certificate. In the digital landscape, websites must obtain these certificates to safeguard user data, confirm their ownership, thwart malicious attempts to create counterfeit versions of their sites and foster a sense of trust among users.
When a website prompts users to log in, share sensitive information like credit card details, or access private data such as health benefits or financial records, ensuring the confidentiality of this information becomes paramount. SSL certificates play a crucial role in maintaining the privacy of online interactions, providing users with the assurance that the website they are engaging with is legitimate and secure enough for sharing personal information.
From a business perspective, it’s imperative to note that possessing an SSL certificate is a prerequisite for any web address using HTTPS. This secure variant of HTTP ensures that all traffic between the user and the website is encrypted via SSL technology. In fact, most modern browsers flag HTTP sites—those lacking SSL certificates—as “not secure.” This warning serves as a stark reminder to users that they may be navigating an unreliable site, thereby motivating businesses that have yet to make the transition to HTTPS to do so promptly.
An SSL certificate is instrumental in protecting various types of sensitive information, which includes but is not limited to:
– Login credentials that grant access to user accounts
– Financial transactions involving credit cards or bank accounts
– Personally identifiable information (PII), such as full names, addresses, dates of birth, and phone numbers
– Legal documents and contracts that require confidentiality
– Medical records that necessitate privacy protections
– Proprietary information that businesses must keep under wraps
Understanding the importance and functionality of SSL certificates can help users and businesses navigate the complexities of online security, ensuring a safer digital experience for everyone.
Varieties of SSL Certificates
When it comes to securing online communications, several types of SSL certificates are available, each offering different levels of validation and assurance. In total, there are six primary categories that one can consider:
1. Extended Validation Certificates (EV SSL)
2. Organization Validated Certificates (OV SSL)
3. Domain Validated Certificates (DV SSL)
4. Wildcard SSL Certificates
5. Multi-Domain SSL Certificates (MDC)
6. Unified Communications Certificates (UCC)
Let’s explore each of these categories more thoroughly, starting with the pinnacle of SSL security: the Extended Validation certificate.
Extended Validation Certificates (EV SSL)
Often regarded as the most prestigious and costly option among SSL certificates, the Extended Validation certificate is predominantly utilised by high-stakes websites that handle sensitive data and facilitate online transactions. Upon installation, this type of certificate enhances the browser address bar with visual indicators such as a padlock icon, the secure “HTTPS” prefix, and the business’s name alongside its country of origin. This clear display serves a crucial role in distinguishing reputable sites from fraudulent ones, providing users with peace of mind. However, acquiring an EV SSL certificate requires the website owner to undergo a rigorous identity verification process, ensuring that they possess the legal authority to claim rights over the specified domain.
Organization Validated Certificates (OV SSL)
Next in line is the Organization Validated certificate, which offers a level of trust comparable to that of EV SSL certificates. To obtain an OV SSL, website owners must also navigate a comprehensive validation process much like its extended counterpart. An OV SSL displays the organisation’s details in the browser’s address bar, which helps to differentiate legitimate sites from potential threats. Although slightly less expensive than EV SSL, OV SSLs are still considered a premium option. Their primary function is to encrypt sensitive user information during transactions, making them essential for commercial or public-facing websites that prioritise customer confidentiality.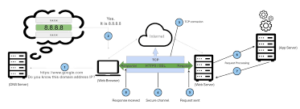
Domain Validated Certificates (DV SSL)
In stark contrast to the previous two types, Domain Validated certificates require a much simpler validation process. Consequently, DV SSLs provide lower assurance levels and minimal encryption capabilities. These certificates are typically favoured by blogs and informational websites that do not engage in data collection or financial transactions. One of the most budget-friendly options on the market, DV SSLs, can be acquired swiftly; all that is needed is for the website owner to verify their domain ownership through a straightforward email or phone response. When displayed in the browser’s address bar, a DV SSL only shows the padlock icon and “HTTP” without revealing any business name.
Wildcard SSL Certificates
For those managing multiple sub-domains under a single primary domain, Wildcard SSL certificates offer a practical solution. These certificates enable users to secure a primary domain along with an unlimited number of sub-domains under one umbrella, making them a cost-effective alternative to purchasing individual certificates for each sub-domain. A Wildcard SSL certificate incorporates an asterisk (*) within its common name, symbolising that any valid sub-domain associated with that base domain is covered. For instance, a single Wildcard certificate for *website can protect various sub-domains such as payments.yourdomain.com, login.yourdomain.com, and mail.yourdomain.com, among others.
Multi-Domain SSL Certificates (MDC)
Moving on to Multi-Domain SSL certificates, these versatile certificates can safeguard numerous distinct domains and/or sub-domains simultaneously. They allow for the inclusion of unique domains as well as sub-domains that may possess different Top-Level Domains (TLDs), barring local or internal domains. For example, one Multi-Domain certificate could potentially secure:
– www.example.com
– example.org
– mail.this-domain.net
– example.anything.com.au
– checkout.example.com
– secure.example.org
However, it’s worth noting that Multi-Domain certificates do not automatically cover sub-domains. Therefore, if both www.example.com and example.com must be secured under one Multi-Domain certificate, both hostnames must be explicitly stated when applying for the certificate.

Unified Communications Certificate (UCC)
Lastly, we have Unified Communications Certificates (UCC), which are specifically designed to support multiple domains and are often utilised in Microsoft Exchange and Office Communications environments. UCCs enable organisations to streamline their security protocols by consolidating various domain names under one certificate.
In conclusion, selecting the appropriate SSL certificate type depends largely on your website’s specific needs and the level of trust you wish to convey to your users. Understanding these different varieties can empower you to make an informed decision that not only secures your online presence but also fosters confidence among your visitors.
The Unified Communications Certificate, commonly known as UCC, serves a vital function in digital security. These certificates are also referred to as Multi-Domain SSL certificates, highlighting their versatility. Crafted initially to safeguard Microsoft Exchange and Live Communications servers, UCCs have since evolved to accommodate a broader spectrum of users. Nowadays, they can be utilised by any website proprietor who wishes to secure multiple domain names under a single certificate, thereby streamlining the process of online security.
 validation is visually represented by the presence of a padlock icon in web browsers, instilling confidence in users who visit these sites. Furthermore, UCCs can also function as Extended Validation (EV) SSL certificates, providing an additional layer of trust through the distinctive green address bar that signals high assurance to visitors.
validation is visually represented by the presence of a padlock icon in web browsers, instilling confidence in users who visit these sites. Furthermore, UCCs can also function as Extended Validation (EV) SSL certificates, providing an additional layer of trust through the distinctive green address bar that signals high assurance to visitors.
Understanding the various types of SSL certificates available is crucial for anyone looking to select the most appropriate certificate for their website’s needs.
When it comes to acquiring an SSL certificate, there are a few avenues one might explore. The most direct route is through a Certificate Authority (CA). These entities—often referred to as Certification Authorities—are responsible for issuing millions of SSL certificates annually. They play an indispensable role in the internet’s infrastructure, facilitating secure and trustworthy interactions between users online.
The price of an SSL certificate can vary significantly, ranging from free options to those costing several hundred dollars, depending on the level of security required. Once you’ve determined the type of certificate that aligns with your needs, you can begin searching for Certificate Issuers that provide the specific SSL solutions you’re looking for.
The journey to obtaining your SSL certificate typically involves several key steps. First and foremost, it’s essential to prepare your server adequately and ensure that your WHOIS record is current and accurately reflects the information you plan to submit to the Certificate Authority. This means verifying that your record displays the correct company name, address, and other pertinent details.
Next, you must generate a Certificate Signing Request (CSR) on your server. This step may seem daunting, but rest assured that your hosting provider can assist you in this process, guiding you through it to ensure everything is set up correctly.
Once you have completed these preparatory actions, you can submit your request and move forward in securing your website with an SSL certificate. This process not only enhances your site’s credibility but also protects both you and your visitors in an increasingly digital world.
In order to authenticate your domain and verify your company’s information, the first step involves submitting the necessary documentation to the Certificate Authority. Once this verification process reaches its conclusion, you will receive a certificate from them, which you will then need to install. If you are managing your website, the next task is to configure this certificate on your web hosting platform or directly on your servers.
The speed at which you can acquire your certificate varies based on the type of SSL certificate you select and the specific provider from whom you obtain it. Different levels of validation come with varying timelines; for instance, a straightforward Domain Validation SSL certificate can typically be issued in mere minutes after placing your order. In contrast, an Extended Validation SSL certificate may require a whole week to process.
Now, let’s explore the various categories of SSL certificates available.
Regarding the use of an SSL certificate across multiple servers, it is feasible to utilise a single SSL certificate for several domains hosted on the same server. Depending on the issuing vendor, you may also have the option to deploy that same certificate across different servers. This capability arises from the existence of Multi-Domain SSL certificates, which we have touched upon earlier.
Multi-domain SSL Certificates are designed to accommodate multiple domains, the exact number of which is determined by the Certificate Authority that issues them. This distinguishes them from Single-Domain SSL Certificates, which are specifically intended to secure only one domain.
To add complexity, Multi-Domain SSL Certificates might also be referred to as SAN certificates—SAN being an acronym for Subject Alternative Name. Each multi-domain certificate includes additional fields known as SANs, which enable you to list extra domains that you wish to protect under one single certificate.

Furthermore, Unified Communications Certificates (UCCs) and Wildcard SSL Certificates provide options for securing multiple domains. In fact, Wildcard certificates allow for an unlimited number of subdomains under a primary domain.
One crucial aspect to keep in mind is that SSL certificates do have expiration dates; they are not perpetual. According to regulations set forth by the Certificate Authority/Browser Forum—an organisation that functions as the main regulatory body within the SSL industry—SSL certificates should not exceed a lifespan of 27 months. This means that while a standard SSL certificate lasts for two years, you can extend that duration by up to three additional months if you renew before the current certificate expires.
The reasoning behind these expiration dates stems from the necessity of periodically revalidating authentication information to ensure its accuracy remains intact. The digital landscape is ever-evolving; companies frequently change ownership, and websites often undergo transitions. As these entities shift hands, the information pertinent to their SSL certificates must also be updated accordingly. The designated expiry period serves as a mechanism to guarantee that the data used for authenticating servers and organisations is as current and precise as possible.
Historically, SSL certificates could be issued for durations of up to five years, but this was eventually shortened first to three years and, most recently, to two years, with an allowance for an extra three months if renewal occurs while some time remains on the prior certificate. In a notable move in 2020, tech giants Google, Apple, and Mozilla announced their decision to enforce a one-year maximum for SSL certificates despite this proposal being rejected by the Certificate Authority Browser Forum. This new regulation took effect in September 2020, and there is speculation that future changes may further reduce the allowable validity period.

When an SSL certificate reaches its expiration date, the corresponding website becomes inaccessible. This highlights the critical importance of monitoring and renewing SSL certificates in a timely manner to maintain uninterrupted security and access for your users.
If the certificate has lapsed, visitors will encounter a warning message indicating that the site is not secure and may pose potential risks.
While users technically have the option to continue browsing despite this warning, it’s strongly discouraged due to significant cybersecurity threats, including the risk of encountering malware. This scenario can lead to increased bounce rates for website owners, as users tend to quickly navigate away from the homepage in search of safer alternatives.
For larger businesses, managing the timelines of SSL certificate expirations can be particularly daunting. In contrast to small and medium-sized enterprises (SMEs) that might only oversee one or a handful of certificates, large corporations often operate across various markets with multiple websites and networks. Consequently, they face the challenge of tracking numerous SSL certificates. When an SSL certificate expires at this level, it’s typically due to oversight rather than a lack of competence. To effectively manage these certificates, more prominent organisations should consider utilising a certificate management platform. A variety of such tools are available online, allowing enterprises to monitor and manage their digital certificates throughout their entire infrastructure. Users of these platforms need to log in regularly to stay informed about upcoming renewal deadlines.
Once a certificate has expired, it becomes invalid, preventing secure transactions from being conducted on the associated website. Certification Authorities (CAs) will send out renewal notifications before the expiration date approaches.
Regardless of which Certificate Authority or SSL provider you choose, they will typically send reminders regarding expiration at predetermined intervals, often beginning 90 days prior to the date. To ensure that the appropriate individuals receive these notifications, it’s wise to distribute them to an email list rather than relying on a single person who might no longer be with the company or may have transitioned to another role by the time the alert is sent. It’s also important to consider which stakeholders are included on this distribution list so that all relevant parties are informed in a timely manner.
Identifying whether a website possesses an SSL certificate is relatively straightforward. Simply glance at the address bar of your browser: if the URL begins with HTTPS rather than HTTP, it indicates that an SSL certificate secures the site. Additionally, secure sites will display a closed padlock icon, which can be clicked to view security details; trustworthy sites often showcase green padlocks or green address bars. Conversely, browsers will display warning signs if a connection lacks security—these might include a red padlock, an open padlock, a strikethrough on the website’s address, or a warning triangle atop the padlock emblem.

To ensure your online experience remains safe, it’s crucial to submit personal information and payment details only to websites featuring Extended Validation (EV) or Organization Validation (OV) certificates. Domain Validation (DV) certificates are generally inadequate for eCommerce sites. You can ascertain whether a site has an EV or OV certificate by examining the address bar; for EV SSLs, the organisation’s name will be prominently displayed there. In the case of OV SSLs, clicking on the padlock icon will reveal details about the organisation’s name. DV SSLs, however, only feature the padlock icon itself without additional identifying information.
It’s also wise to read through the website’s privacy policy. This document provides insight into how your data will be handled; reputable companies are transparent about their data collection practices and usage.
Moreover, look for trust signals or indicators on websites. Beyond SSL certificates, these may include recognised logos or badges that signify adherence to specific security standards. Other factors that can help determine a site’s legitimacy include verifying its physical address and contact number, reviewing its returns or refund policy, and ensuring that prices appear reasonable rather than suspiciously low.
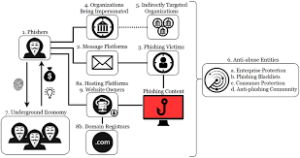
Lastly, remain vigilant against phishing scams. Cybercriminals sometimes create counterfeit websites that closely resemble legitimate ones in order to deceive users into making purchases or logging into their fraudulent sites. It’s worth noting that phishing sites can also secure SSL certificates, thereby encrypting the traffic between you and them. An increasing number of phishing attacks now occur on HTTPS sites, misleading users who feel reassured by the presence of a padlock icon.
In light of these considerations, it’s essential to exercise caution and vigilance when navigating online spaces.
![]()
To safeguard yourself against various online threats, it is imperative to adopt a vigilant approach while navigating the web. One of the first steps you can take is to meticulously scrutinise the domain name of the website you are visiting. A common tactic employed by malicious actors is to create counterfeit sites that closely resemble legitimate ones, often differing by a mere character. For instance, a fraudulent site might be cleverly disguised as “amaz0n.com” instead of the authentic “amazon.com.” To mitigate any uncertainty, it is wise to bypass clicking on links altogether and manually enter the desired web address directly into your browser. This simple act can significantly decrease the chances of landing on an untrustworthy site.
Furthermore, it is crucial to exercise extreme caution before submitting any sensitive information, such as login credentials, passwords, banking details, or other personal data. Only proceed with such actions when you have unequivocally confirmed the site’s legitimacy. Take a moment to evaluate what the website is offering—does it seem suspicious or too good to be true? Additionally, consider whether registration is genuinely necessary for the service being provided.
In the realm of digital safety, ensuring that your devices are adequately protected is another essential measure. Utilising robust security software, such as Kaspersky Internet Security, can provide an added layer of defence; this program systematically checks URLs against a vast database of known phishing sites and can identify scams, even if they appear deceptively safe at first glance.
As the landscape of cybersecurity continues to change and adapt, staying informed about the different types of SSL certificates and learning how to differentiate between secure and potentially harmful sites will serve as invaluable tools. By arming yourself with this knowledge, you will not only enhance your ability to navigate the internet safely but also protect your personal information from the ever-evolving tactics employed by cybercriminals.
In summary, remaining vigilant and adopting proactive measures in your online activities is essential in today’s digital age. By taking these steps, you can significantly reduce your risk of falling victim to scams and ensure that your data remains secure.
Maxthon
In an era where our data is constantly at risk and communication often lacks clarity, it is essential to approach the sharing of sensitive information with great caution. Picture this: you receive a message urging you to provide your details. Before you respond, take a moment to pause and consider the implications of your actions. It’s vital to understand how the organisations you interact with typically reach out to you. Familiarising yourself with their standard communication methods and knowing exactly what kind of information they may request from you is imperative.
Take, for instance, a bank. It is doubtful that they would send you an email with links directing you to their online banking platform, asking you to log in. Such an unusual request should immediately trigger your instincts to be wary. If you ever find yourself unsure about why someone is requesting your personal information, do not hesitate to pick up the phone. Contact the company directly to verify the legitimacy of the request and seek clarification on its purpose.
Maxthon has made impressive strides in enhancing the security of web applications, employing a thorough approach that prioritises user safety and data protection. At its core, the Maxthon browser features a robust array of advanced encryption technologies designed to create formidable barriers against unauthorised access during data transmission. Whenever users interact with web applications, their sensitive information—including passwords and personal details—is carefully encrypted and transmitted securely. This diligent method makes it exceedingly difficult for malicious actors to intercept or misuse this critical data.
Beyond its formidable encryption features, Maxthon’s commitment to security encompasses a proactive stance on monitoring vulnerabilities. The development team remains alert, continuously scanning for known weaknesses and promptly releasing patches to address any issues that arise. Users are strongly encouraged to enable automatic updates, ensuring they receive the latest security enhancements seamlessly, reinforcing their protection without any additional effort required on their part.
One of Maxthon’s standout features is its built-in ad blocker, a crucial tool designed to shield users from potentially dangerous advertisements that could compromise their security. By filtering out such unwanted content, Maxthon significantly reduces the chances of users falling victim to phishing scams or accidentally downloading malware through drive-by attacks.

Phishing protection is another essential element of Maxthon’s security framework. The browser diligently scans for suspicious websites, alerting users before they unwittingly enter potentially hazardous online environments. This proactive measure serves as a vital line of defence against cybercriminals who aim to exploit unsuspecting individuals for their sensitive information.
For those who value privacy while navigating the online realm, Maxthon offers specially crafted privacy mode options designed specifically for this purpose. When activated, this feature ensures that no browsing history or cookies are stored during private sessions, thus granting users greater control over their online activities and interactions. In this manner, Maxthon not only emphasises security but also empowers individuals to traverse the digital landscape with assurance and tranquillity.
Ultimately, in a world fraught with complexities surrounding personal information and communication, Maxthon provides the tools necessary for individuals to protect themselves while confidently engaging in online activities. By understanding the norms of digital interaction and utilising the protective features offered by Maxthon, users can navigate this intricate web of modern communication with a sense of empowerment and security.
