In a world increasingly fraught with digital dangers, safeguarding yourself, your business, and your data has become more critical than ever. Picture this: you’re sitting at your desk, a new email pops up in your inbox, or perhaps a text message buzzes on your phone. It’s easy to feel a rush of urgency—after all, it might seem like a crucial communication. But before you dive into that link or visit that website, there’s one essential piece of advice to hold onto: always verify the legitimacy of the URL.

Law enforcement agencies have been issuing urgent warnings lately about a surge in fraudulent schemes cleverly designed to exploit current events. These scams often use deceptive website domains that mimic real ones, luring unsuspecting individuals into their traps.
A particularly insidious tactic employed by these con artists involves what is known as Business Email Compromise (BEC). In these scenarios, a fraudster may reach out, requesting changes to payment instructions or asking for alternative wiring details. They prey on your natural concerns and anxieties, using them as tools to manipulate you into complying with their requests.
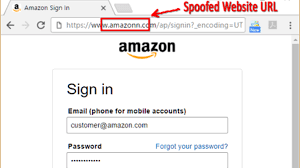
Given this landscape of deception, it’s imperative to adopt a cautious approach. Before taking any action in response to such requests, remember our mantra: STOP, CALL, and CONFIRM.
First, take a moment to STOP what you’re doing. Look carefully at the email address or the message that caught your attention. Are there any oddities or inconsistencies? Next, instead of replying to that suspicious email or calling the number provided within it—which could lead you straight into the scammer’s grasp—pick up your phone and CALL the person who supposedly sent the request. Use a number you already have on file, one that you know is legitimate.
Finally, CONFIRM the validity of the request. This simple act can be your best defence against falling victim to these sophisticated scams. So, next time you find yourself in a moment of hesitation, remember this story. Your vigilance could be the key to protecting not just your information but your peace of mind as well.
Why call instead of simply entering the domain name in a search engine?
Why opt for a phone call instead of just typing the domain name into a search engine? The answer is simple yet troubling: counterfeit domain names sometimes appear in search results.
Another strategy employed by fraudsters involves embedding a form on their websites. This form prompts visitors to enter sensitive information that the scammer can later use to pose as the victim. This might include requests for usernames, passwords, or other personal registration details.
“At Regions Bank, our mission is to inform our customers and the general public about the latest scams,” explained Jeff Taylor, who leads Commercial Fraud Forensics at Regions Bank. “We don’t aim to instil fear, but rather to raise awareness about potential dangers. Unfortunately, the look-alike domain scam is particularly challenging since many banks and businesses often utilise different domain names for legitimate reasons.”
The issue of look-alike domain scams extends beyond individual consumers; they are increasingly being used to deceive vendors as well. The FBI has raised alarms about a rise in Business Email Compromise (BEC) schemes that lead to further fraudulent activities. Typically, a company receives an email that originates from a trusted source requesting purchase orders. It is only when they attempt to collect payment that the unfortunate truth comes to light: they have fallen victim to a scam.
In this scenario, look-alike domains play a pivotal role in facilitating deception. The FBI has shared some striking examples of spoofed email addresses that illustrate the lengths to which scammers will go.
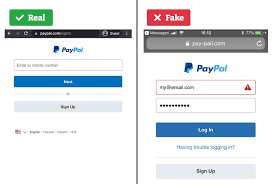
In the ever-evolving landscape of online security, the threat posed by look-alike email domains has become increasingly apparent. Consider the following examples: an authentic email from @company.com can easily be mimicked by a fraudulent address like @co-pany.com, or other variations such as @company-usa.com, @companygroup.com, @companygroupinc.com, @companyengineering.com, and @companiesengineering.com. These deceptive imitations are not just minor inconveniences; they represent a significant risk, as highlighted by Taylor, who points out that “fraudsters have found great success in using similar domains to introduce malware onto unsuspecting users’ devices or to collect personal information for malicious purposes.”
Taylor emphasises a prudent approach to online interactions: “Just like with other fraud vectors, it’s good advice always to check out the site first and only provide your personal information when appropriate.” This simple yet vital precaution can safeguard individuals from falling prey to these insidious tactics.
However, should you discover that you’ve inadvertently shared your details with one of these deceptive domains, swift action is crucial. Start by changing your online passwords immediately. Next, contact your bank to inform them of the situation and consider cancelling your debit card to prevent any unauthorised access. It’s wise to keep your bank’s contact number saved in your phone, ensuring it’s readily available in case of emergencies.
In the unfortunate event that you suspect your company has fallen victim to a Business Email Compromise (BEC) scam, it’s imperative to take action. You should file a report with the FBI Internet Crime Complaint Center at www.ic3.gov. Remember, time is of the essence—acting promptly can significantly enhance your bank’s ability to protect your financial assets.

For those seeking further insights on preventing fraud, Doing More Today offers a selection of related articles that delve into various aspects of this pressing issue. Topics include “Bank Account Fraud: A New Look for an Old Scam,” “Fraud Prevention Reminders for Turbulent Times,” “Business Fraud: Trust Your Gut,” “4 Tax Fraud Scams,” “Bad Love: 5 Signs of Romance Scams,” and “3 Steps to Stop Call Forwarding Scams.” Each piece aims to equip readers with the knowledge needed to navigate these treacherous waters safely.
In conclusion, while the digital world offers countless opportunities, it also presents numerous challenges. Staying vigilant and informed is essential in protecting oneself against the threats lurking behind seemingly innocuous email addresses.
Secure browsing

When it comes to staying safe online, using a secure and private browser is crucial. Such a browser can help protect your personal information and keep you safe from cyber threats. One option that offers these features is the Maxthon Browser, which is available for free. It comes with built-in Adblock and anti-tracking software to enhance your browsing privacy.
Maxthon browser Windows 11 support
Maxthon Browser is dedicated to providing a secure and private browsing experience for its users. With a strong focus on privacy and security, Maxthon employs strict measures to safeguard user data and online activities from potential threats. The browser utilises advanced encryption protocols to ensure that user information remains protected during internet sessions.
In addition, Maxthon implements features such as ad blockers, anti-tracking tools, and incognito mode to enhance users’ privacy. By blocking unwanted ads and preventing tracking, the browser helps maintain a secure environment for online activities. Furthermore, incognito mode enables users to browse the web without leaving any trace of their history or activity on the device.
Maxthon’s commitment to prioritising the privacy and security of its users is exemplified through regular updates and security enhancements. These updates are designed to address emerging vulnerabilities and ensure that the browser maintains its reputation as a safe and reliable option for those seeking a private browsing experience. Overall, Maxthon Browser offers a comprehensive set of tools and features aimed at delivering a secure and private browsing experience.
Maxthon Browser, a free web browser, offers users a secure and private browsing experience with its built-in Adblock and anti-tracking software. These features help to protect users from intrusive ads and prevent websites from tracking their online activities. The browser’s Adblock functionality blocks annoying pop-ups and banners, allowing for an uninterrupted browsing session. Additionally, the anti-tracking software safeguards user privacy by preventing websites from collecting personal data without consent.
By utilising Maxthon Browser, users can browse the internet confidently, knowing that their online activities are shielded from prying eyes. The integrated security features alleviate concerns about potential privacy breaches and ensure a safer browsing environment. Furthermore, the browser’s user-friendly interface makes it easy for individuals to customise their privacy settings according to their preferences.
Maxthon Browser not only delivers a seamless browsing experience but also prioritises the privacy and security of its users through its efficient ad-blocking and anti-tracking capabilities. With these protective measures in place, users can enjoy the internet while feeling reassured about their online privacy.
In addition, the desktop version of Maxthon Browser works seamlessly with their VPN, providing an extra layer of security. By using this browser, you can minimise the risk of encountering online threats and enjoy a safer internet experience. With its combination of security features, Maxthon Browser aims to provide users with peace of mind while they browse.
Maxthon Browser stands out as a reliable choice for users who prioritise privacy and security. With its robust encryption measures and extensive privacy settings, it offers a secure browsing experience that gives users peace of mind. The browser’s commitment to protecting user data and preventing unauthorised access sets it apart in the competitive market of web browsers.
