Introduction
Financial technology has revolutionized how we conduct transactions, manage investments, and access banking services. However, this digital transformation has created new vulnerabilities that fraudsters eagerly exploit. As financial systems become more interconnected and complex, fraud detection must evolve from reactive to proactive approaches.
For fintech businesses, fraud represents more than just financial loss—it undermines customer trust, damages brand reputation, and can trigger regulatory penalties. This is why implementing robust fraud detection strategies is not optional but essential for survival in today’s digital financial ecosystem.
Understanding the Fraud Landscape in Fintech
Fraud in fintech takes many forms, each requiring specific detection mechanisms:
Account Takeover (ATO) occurs when criminals gain unauthorized access to user accounts, often through stolen credentials. Once inside, they can drain funds, change account information, or use the compromised account for money laundering.
Synthetic Identity Fraud involves criminals creating fictitious identities by combining real and fabricated information. These synthetic identities can pass initial verification checks and may operate normally before executing larger fraudulent transactions.

Transaction Fraud encompasses unauthorized transactions, ranging from simple credit card theft to sophisticated schemes involving money mules and layered transactions designed to obscure the money trail.
Application Fraud happens when fraudsters use stolen or fabricated information to open new financial accounts, often with the intent to max out credit lines or exploit promotional offers before disappearing.
Essential Fraud Detection Strategies
1. Multi-layered Authentication Systems
Modern authentication must go beyond passwords. A robust system should incorporate:
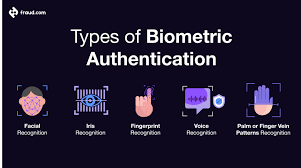
Biometric Verification using fingerprints, facial recognition, or voice authentication adds a physical dimension to security that’s difficult to replicate.
Device Intelligence examines the devices used to access accounts, flagging suspicious logins from unfamiliar devices or locations.
Behavioral Biometrics analyzes patterns in how users interact with devices—how they type, swipe, or navigate—creating a behavioral fingerprint that’s hard for fraudsters to mimic.
2. Machine Learning and AI Detection Systems
Artificial intelligence has transformed fraud detection from rules-based systems to sophisticated pattern recognition:

Anomaly Detection algorithms establish baseline behaviours for users and flag deviations from standard patterns. For example, if a user who typically makes small, local purchases suddenly attempts large international transactions, the system can automatically flag this for review.
Predictive Analytics examines historical fraud patterns to forecast potential vulnerabilities. These systems become increasingly accurate over time as they process more data and fraud scenarios.
Adaptive Authentication dynamically adjusts security requirements based on risk assessment. Low-risk transactions might proceed with minimal friction, while high-risk activities trigger additional verification steps.
3. Real-time Transaction Monitoring
Modern fraud detection must operate at the speed of digital transactions:
Velocity Checks look for suspicious patterns in the frequency of activities, such as multiple account creation attempts or rapid-fire transactions.
Network Analysis examines connections between accounts, identifying clusters of potentially fraudulent activity that might indicate organized fraud rings.

Geolocation Verification checks whether transaction locations make logical sense given a user’s history and profile.
4. Data Integration and Cross-channel Analysis
Effective fraud detection requires a holistic view across all channels and touchpoints:
Unified Customer Profiles combine data from various sources—mobile apps, websites, call centres, and physical locations—to create a comprehensive view of customer behaviour.
Cross-channel Pattern Recognition identifies suspicious activities that might appear normal when viewed in isolation but reveal fraud patterns when examined across channels.
Third-party Data Enrichment augments internal data with external information such as device reputation databases, known fraud networks, and compromised credential lists.
5. Advanced Analytics Tools: Implementation Examples
Let’s look at how these strategies might be implemented in practice with code examples:
This code example demonstrates several key concepts in fraud detection:

- Feature Engineering: The system calculates derived features that are strong fraud indicators, such as distance from home location, unusual transaction amounts compared to user history, and temporal patterns.
- Risk-based Decision Making: Rather than a binary approve/decline decision, the system implements a spectrum of responses based on both the risk score and transaction context.
- Machine Learning Implementation: The Random Forest model can capture complex, non-linear relationships between features and fraud likelihood, making it effective for detecting sophisticated fraud patterns.
- Explainability: The system analyzes feature importance, providing insight into which factors most strongly indicate fraud—crucial for improving the system and explaining decisions to customers and regulators.
6. Behavioral Analytics

Beyond transaction details, modern fraud systems analyze how users behave:
Session Analysis examines user interaction patterns during a session, such as navigation paths, interaction speed, and hesitation points. Fraudsters often exhibit different behaviours than legitimate users when navigating financial interfaces.
Typing Patterns can reveal when a different person is using familiar credentials. Legitimate users develop consistent typing rhythms and patterns that are difficult to replicate.
Usage Consistency looks at whether behaviour matches patterns. For example, a user who constantly carefully reviews transaction details before confirming might raise flags if they suddenly rush through multiple high-value transactions.
carefully reviews transaction details before confirming might raise flags if they suddenly rush through multiple high-value transactions.
7. Collaborative Security Approaches
Fraud detection is strengthened through industry cooperation:
Consortium Data Sharing allows financial institutions to pool anonymized fraud data, creating a more comprehensive picture of emerging threats while preserving customer privacy.
Regulatory Cooperation enables institutions to work with government agencies to identify large-scale fraud operations and money laundering networks.
Vendor Integration leverages specialized third-party security services that focus exclusively on specific types of fraud detection, adding another layer of protection.
Implementation Challenges and Solutions
Implementing fraud detection systems comes with significant challenges:
False Positives create friction for legitimate customers and can damage trust. Solutions include:
- Implementing risk-based authentication that adds friction only when necessary
- Using ensemble models that combine multiple detection approaches for greater accuracy
- Continuously tuning systems based on customer feedback and false positive analysis
Data Privacy Regulations such as GDPR and CCPA restrict how customer data can be used. Consider:
- Implementing privacy-by-design principles in fraud systems
- Using anonymization and pseudonymization techniques
- Creating clear data governance frameworks with documented legitimate interest in fraud prevention

Integration Complexity across legacy and modern systems can impede effectiveness. Address this by:
- Using API-first approaches for system integration
- Implementing data transformation layers to normalize inputs from different systems
- Creating real-time event streams for fraud data rather than batch processing
Building a Fraud Prevention Culture
Technical solutions are only part of effective fraud prevention:
Employee Training should ensure that all staff understand their role in preventing fraud, recognizing warning signs, and following security protocols.

Customer Education helps users protect themselves by recognizing phishing attempts, using strong authentication methods, and understanding how to report suspicious activities.
Regular Testing through penetration testing, red team exercises, and fraud simulations helps identify vulnerabilities before criminals can exploit them.
Measuring and Improving Your Fraud Detection System
Continuous improvement requires careful measurement:
Key Performance Indicators should include:
- False positive rate: Legitimate transactions incorrectly flagged
- False negative rate: Fraudulent transactions missed
- Detection speed: Time from fraud attempt to detection
- Customer impact metrics: Authentication success rates and friction points
A/B Testing allows you to compare different detection approaches and fine-tune systems based on real-world results rather than theoretical models.
Post-incident analysis should thoroughly examine confirmed fraud cases to identify how detection could have happened earlier or more efficiently.
Conclusion

As fintech continues to transform the financial landscape, fraud detection must remain a top priority for businesses. By implementing multi-layered approaches that combine advanced technologies with human expertise, fintech companies can protect both their customers and their bottom line.
Remember that effective fraud prevention is not a static solution but an ongoing process that must continuously evolve to address new threats. By staying vigilant and investing in robust detection systems, your business can build customer trust while minimizing losses in an increasingly digital financial world.
Secure browsing

When it comes to staying safe online, using a secure and private browser is crucial. Such a browser can help protect your personal information and keep you safe from cyber threats. One option that offers these features is the Maxthon Browser, which is available for free. It comes with built-in Adblock and anti-tracking software to enhance your browsing privacy.
By utilising Maxthon Browser, users can browse the internet confidently, knowing that their online activities are shielded from prying eyes. The integrated security features alleviate concerns about potential privacy breaches and ensure a safer browsing environment. Furthermore, the browser’s user-friendly interface makes it easy for individuals to customise their privacy settings according to their preferences.
Maxthon Browser not only delivers a seamless browsing experience but also prioritises the privacy and security of its users through its efficient ad-blocking and anti-tracking capabilities. With these protective measures in place, users can enjoy the internet while feeling reassured about their online privacy.
In addition, the desktop version of Maxthon Browser works seamlessly with their VPN, providing an extra layer of security. By using this browser, you can minimise the risk of encountering online threats and enjoy a safer internet experience. With its combination of security features, Maxthon Browser aims to provide users with peace of mind while they browse.
Maxthon Browser is a reliable choice for users who prioritise privacy and security. With its robust encryption measures and extensive privacy settings, it offers a secure browsing experience that gives users peace of mind. The browser’s commitment to protecting user data and preventing unauthorised access sets it apart in the competitive web browser market.
