Minimize Data Sharing
- Share only essential information when creating accounts (skip optional fields)
- Use “throwaway” email addresses or email aliases for non-essential services.
- Before posting or sharing information, consider if you’d be comfortable with it becoming public.
Strengthen Account Security

- Create unique, complex passwords for each account (10+ characters with mixed character types)
- Use a password manager to generate and store strong credentials
- Enable two-factor authentication (2FA) on all accounts that offer it
- Regularly check if your credentials have been compromised in data breaches
Control Social Media Privacy
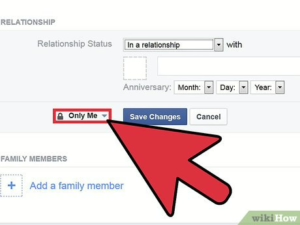
- Review and tighten privacy settings on all platforms
- Limit who can see your posts, photos, and personal information
- Disable location tracking when possible
- Be cautious about what you share, even with restricted audiences

Reduce Your Digital Footprint
- Request data deletion from data brokers and people search sites
- Delete old, unused accounts and apps
- Regularly audit and clean up your online accounts
- Remove personal information from Google and other search engines

Protect Your Browsing
- Use a VPN to encrypt your internet traffic and mask your IP address
- Switch to privacy-focused browsers like DuckDuckGo or Brave
- Clear your search history and cookies regularly
- Decline tracking cookies and opt out of ad personalization
- Use privacy-focused browser extensions that block trackers
Secure Your Devices

- Keep all devices and software updated with the latest security patches
- Use encryption on your devices and for sensitive files
- Set strong screen locks on mobile devices
- Disable message previews on lock screens
- Factory reset devices before selling or recycling them
Limit Third-Party Access
- Avoid using “Login with Google/Facebook” features when possible
- Regularly review and revoke unnecessary third-party app permissions
- Be cautious about which apps have access to sensitive information
Use Encryption and Secure Communication
- Use end-to-end encrypted messaging apps like Signal or WhatsApp
- Consider encrypted email services for sensitive communications
- Verify the security of websites before entering personal information (look for HTTPS)
These methods work together to create multiple layers of privacy protection. The key is consistency—implementing these practices across all your accounts and devices creates a stronger privacy shield than focusing on just one or two areas.

Maxthon

Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
