- Browse in Anonymous Mode – While not providing complete privacy, incognito/private browsing helps block cookies and reduce tracking.
- Use Privacy-Focused Search Engines – Alternatives like DuckDuckGo, Qwant, and Startpage don’t collect and sell user data like mainstream search engines do.
- Use End-to-End Encrypted Messaging Apps – Services like WhatsApp, Signal, and Telegram provide better message security than apps with only transit encryption.
- Use a VPN – Virtual Private Networks encrypt your connection and protect your browsing data from internet service providers.
- Use Security Browser Extensions – Tools like HTTPS Everywhere, Ghostery, and AdBlock enhance privacy and security.
- Don’t Store Private Information in Public Storage – Avoid keeping sensitive documents in services like Google Docs or Dropbox without encryption.
- Be Cautious on Wi-Fi Networks – Public Wi-Fi lacks encryption, making your data vulnerable. Use a VPN for additional protection.
- Use Secure Passwords – Create complex, unique passwords (12+ characters) using a mix of uppercase, lowercase, numbers, and special characters.
- Manage Cookie Settings – Control website cookie permissions to limit tracking and profiling.
- Adjust Social Media Privacy Settings – Customize privacy options instead of using default settings that often share extensive personal data.

Understanding Privacy Controls in Detail

Privacy controls are the settings and tools that allow you to manage how your personal data is collected, used, and shared online. Here’s a comprehensive breakdown of the most critical privacy controls you should understand:
Browser Privacy Controls
Cookie Management
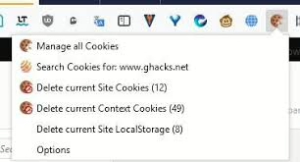
- First-party cookies: Created by the website you’re visiting; manage these in browser settings
- Third-party cookies: Created by other domains (typically advertisers); can be blocked entirely
- Cookie preferences: Most browsers allow you to:
- Accept all cookies
- Block third-party cookies
- Block all cookies
- Create exceptions for specific websites
Tracking Prevention
- Do Not Track (DNT) signals: A browser setting that requests websites not track you (though compliance is voluntary)
- Enhanced Tracking Protection: Features in browsers like Firefox that block known trackers
- Fingerprinting protection: Prevents sites from identifying you through your browser’s unique characteristics

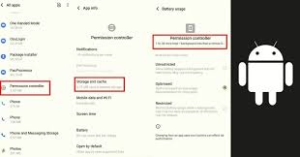
Permission Controls
- Location access: Toggle whether websites can access your physical location
- Camera/microphone access: Manage which sites can use these devices
- Notification permissions: Control which sites can send you alerts
- Download permissions: Set rules for automatic downloads
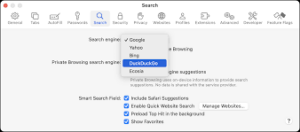
Search Engine Privacy
- Search history: Options to pause or delete your search history
- Personalization controls: Turn off personalized search results
- Private search engines: Services like DuckDuckGo that don’t store search data
- Anonymous search options: Using tools like Startpage that retrieve Google results anonymously
Social Media Privacy Settings

Profile Visibility

- Public vs. private accounts: Control who can see your content
- Post audience selectors: Choose who sees individual posts (public, friends, custom groups)
- Profile information visibility: Control who sees your personal details, photos, and friends list
Data Collection Controls
- Ad preferences: Manage how your data is used for advertising
- Off-platform activity: Control whether the platform tracks your activity on other websites
- Face recognition settings: Toggle features that automatically identify you in photos

Connection Controls
- Friend/follower management: Control who can connect with you
- Blocking/muting options: Restrict specific users from interacting with you
- Tagging permissions: Control who can tag you in posts or photos
Device Privacy Settings
App Permissions
- Location services: Control which apps access your location and when (consistently, while using, never)
- Contact access: Manage which apps can read your contacts list
- Media access: Control which apps can access photos, videos, and audio files
- Background activity: Limit what apps can do when not actively in use
System-level Controls
- Advertising ID: Reset or limit tracking across apps
- Analytics sharing: Control whether your device usage data is shared
- Diagnostic data: Manage what system information is sent to manufacturers
Network Privacy Tools
VPN Settings
- Kill switch: Disconnects internet if VPN connection drops
- Split tunnelling: Choose which apps use the VPN connection
- DNS leak protection: Prevents DNS requests from bypassing the VPN
- Protocol selection: Different encryption protocols offer varying levels of security/speed
Router Settings
- Guest networks: Separate network for visitors that limits access to your devices
- DNS settings: Custom DNS servers can block tracking (e.g., Pi-hole, NextDNS)
- WPA3 encryption: Latest security standard for Wi-Fi networks

Account Privacy Features
Two-factor authentication (2FA)
- SMS verification: Codes sent via text message
- Authenticator apps: Generate time-based codes on your device
- Physical security keys: Hardware devices that verify your identity
Login Activity Monitoring
- Active sessions: View and terminate current logins across devices
- Login alerts: Notifications about new sign-ins
- Login history: Review past account access
Data Access and Control
Data Download Options
- Data export tools: Download copies of your personal data from services
- Activity logs: Review your actions and interactions within platforms
- Content archives: Access historical content you’ve shared or created
Deletion Controls

- Individual item deletion: Remove specific pieces of content
- Bulk deletion tools: Remove multiple items based on date or type
- Account deletion: Completely remove your account and associated data
Effective Privacy Management Strategies

- Regular privacy checkups: Schedule periodic reviews of your privacy settings
- Default to restrictive settings: Start with the most private options and loosen only as needed
- Compartmentalization: Use different browsers/accounts for different purposes
- Privacy-focused alternatives: Consider services designed with privacy as a primary feature
Understanding and properly configuring these controls gives you significant power over your digital privacy, though it requires ongoing attention as services frequently update their privacy features and policies.
Maxthon

Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
