The Electoral Boundaries Review Committee (EBRC) report was released on March 11, 2025, which typically signals an approaching election. Political parties are now awaiting the Writ of Election, which will officially start the election process.
Key steps in Singapore’s election process:
Writ of Election
A formal written order issued by the President (on the Prime Minister’s advice)
Specifies Nomination Day details
Names the returning officer who oversees the election
The time between EBRC report and Writ varies (from just 1 day in 2001 to over 3 months in 2020)
Nomination Day
Parties reveal final candidate lineups
Candidates submit nomination papers in person between 11 a.m. and noon.
Election deposit required (approximately $13,500 in the last election)
Deposit refunded if candidate gets at least 12.5% of valid votes
Afternoon: Candidates have 30 minutes to scrutinize others’ applications
Contests or walkovers declared after validation
Campaigning Period
Begins after Nomination Day and ends before Cooling-off Day
Polling Day must be 10-56 days after Nomination Day (typically 9 days plus a Cooling-off Day)
Rallies require police permits with fixed venues
Other campaign methods: house visits, pamphlets, posters, online ads
Cooling-off Day
The day before Polling Day
No campaigning allowed for 24 hours
Gives voters time to reflect on campaign issues
Introduced in 2010, first used in 2011
Polling Day
A public holiday
Voting from 8am to 8pm
Ballot boxes are sealed and transported to counting stations
Sample counts are released first; final results typically come after midnight
The article was published on April 12, 2025. Singapore is currently in the pre-writ phase of the election, and political parties have already increased their activities in anticipation of the announcement.
Singapore GE2025 Electoral Timeline in Detail
Pre-Election Period
- Electoral Boundaries Review Committee (EBRC) Report
- Released on March 11, 2025
- Marks the first official indication of approaching elections
- Parties began intensifying ground activities after this report
- Pre-Writ Activities
- Political parties increase engagement in the heartland
- Potential candidates begin walkabouts and community events
- Parties finalize candidate selections and constituency strategies
- The time between EBRC report and Writ varies (historically from 1 day to over 3 months)
Official Election Period
- Writ of Election
- Issued by the President on the Prime Minister’s advice
- Formally dissolves Parliament
- Specifies the date for Nomination Day
- Names the returning officer (RO) who will oversee the election
- Election deposit amount confirmed (previously $13,500)
- Pre-Nomination Preparations
- Election deposit payment period opens
- Candidates can pay via electronic means, bank draft, or cheque
- Candidates prepare nomination papers, certificates, and other required documents
- Nomination Day must be 5 days to 1 month after the Writ (excluding Sundays and public holidays)
- Nomination Day
- Candidates submit nomination papers at designated centers between 11am-12pm
- Must be accompanied by proposers, seconders, and at least 4 assenters
- 12pm-12:30pm: Period for scrutinizing other candidates’ applications and raising objections
- RO validates all applications and addresses objections
- RO declares contests or walkovers in each constituency
- Candidates make thank-you speeches (televised and online)
- Campaigning officially begins immediately afterward
- Campaign Period
- Duration: From Nomination Day until Cooling-off Day (typically 9 days)
- Rally permit applications submitted to the commissioner of police
- Multiple applications for the same time slot resolved through balloting
- Candidates conduct house visits, distribute materials, and display posters/banners
- Political advertisements run online and in traditional media
- Political broadcasts aired on national television
- Polling Day must be scheduled between 10-56 days after Nomination Day
- Cooling-off Day
- The day immediately before Polling Day
- All active campaigning is prohibited for 24 hours
- Existing materials can remain, but no new campaigning is allowed
- Voters given time to reflect on issues without new campaign influence
- Candidates prepare for polling day logistics
- Polling Day
- Declared a public holiday
- Polling stations open from 8am to 8pm
- Candidates may inspect polling stations
- Voters cast ballots at assigned polling stations
- 8pm: Polls close and vote counting begins
- Seal ballot boxes and transport them to counting centers
- Sample counts released to give an early indication of results
- Final results are typically announced after midnight
- Post-Election
- Winning candidates receive a certificate of election
- Parliament must convene within 3 months of the general election
- New government formed based on election results
- Elected MPs sworn in during the first Parliament sitting
- Non-constituency MP (NCMP) seats allocated if applicable
This timeline follows the statutory requirements under Singapore’s Parliamentary Elections Act. The exact dates will be determined once the Writ of Election is issued.
Based on the information provided in the article, there’s no specific anticipated Polling Day mentioned for Singapore’s GE2025.
The article only outlines the electoral process and indicates that Polling Day should occur:
- No earlier than the 10th day after Nomination Day
- No later than the 56th day after Nomination Day
- Typically, the period between Nomination Day and Polling Day has lasted the minimum period of 9 days plus a Cooling-off Day
Since the Writ of Election hasn’t been issued yet (as of the April 12, 2025, article date), Nomination Day hasn’t been announced, which means Polling Day also remains undetermined.
The article notes that the time between the EBRC report (released on March 11, 2025) and the issuance of the Writ has historically varied considerably:
- In 2020: Over three months
- In 2015: Just over a month
- In 2001: Just one day
Without additional information beyond what’s in the article, it’s not possible to specify an anticipated voting day for GE2025.
- Toppan Next Tech (TNT), a printing vendor, suffered a ransomware attack on April 1, 2025
- TNT has been engaged to print poll cards and ballot papers for Singapore’s upcoming general election
- The ELD states that election operations have not been affected by this attack.
- The ELD has not yet provided voter data to TNT for GE2025
- TNT’s attack affected two banking clients (DBS Bank and Bank of China Singapore), compromising data of over 11,000 customers
- TNT was also a printing vendor for the 2023 Presidential Election
- In 2023, there was an incident where some households received duplicate poll cards due to a printing error
This appears to be a developing cybersecurity situation in Singapore related to their upcoming general election. The ELD is monitoring the situation closely and working with TNT to enhance security processes.
Analysis of the Ransomware Attack and Electoral Implications
The Ransomware Attack: Technical Analysis
Based on the limited information available, this appears to be a targeted ransomware attack against Toppan Next Tech (TNT), a printing vendor that handles sensitive electoral and banking materials. Here’s what we can analyze:
Attack
Attack Vectors and Timeline:
- The article doesn’t specify the ransomware variant or initial access method (common vectors include phishing emails, exploited vulnerabilities, or compromised credentials)
- The reporting timeline is concerning: the attack occurred on April 1 but was only reported to the Personal Data Protection Commission on April 6 (a 5-day delay)
- This delay in reporting could indicate either detection challenges or internal process issues.
Impact on Election Security
The Elections Department claims operations remain unaffected, but several risk factors stand out:
Positive Security Factors:
- ELD had not yet shared voter data with TNT when the attack occurred
- ELD reports that preliminary investigations show no election-related data was compromised
- The department is implementing enhanced processes with TNT to minimize risks
Concerning Security Factors:
- TNT’s security posture appears questionable given the successful compromise of banking data
- The vendor has previously demonstrated operational issues (the 2023 duplicate poll card incident)
- The close timing to an election creates a window of vulnerability as election materials must still be produced
- Trust in election processes could be undermined regardless of actual impact
Political Implications
This incident could have several political ramifications:
Public Perception:
- It may create voter uncertainty about the integrity of the upcoming election
- Could fuel speculation about potential foreign interference, even if evidence doesn’t support this
- The government’s handling of this situation will face scrutiny from opposition parties
Election Administration:
- ELD may face pressure to find an alternative vendor despite limited time before GE2025
- Contingency planning and additional verification steps will likely be implemented, potentially impacting logistics
- Requires balancing transparency about the incident with preventing unnecessary alarm
Data Protection Governance:
- Highlights the challenge of securing extended supply chains involved in election administration
- May accelerate review of cybersecurity requirements for vendors handling sensitive government data
- Could lead to regulatory changes in how critical election infrastructure vendors are vetted
Anti-Scam Guidance for Voters
In light of this incident, voters should be vigilant about potential follow-up scams:
- Verify Communication Sources:
- Official election communications will come directly from ELD through established channels
- Be suspicious of unsolicited calls, emails, or messages claiming to be from election authorities
- Protect Personal Information:
- Do not provide personal details to anyone claiming to “verify voter information” due to the breach
- Remember that legitimate election officials won’t ask for sensitive information through unsecured channels
- Watch for Election-Related Phishing:
- Be wary of links or attachments in emails claiming to contain updated polling information
- Access electoral information directly through official government websites
- Report Suspicious Activity:
- Report unusual communications about the election to ELD and relevant authorities
- Forward suspicious messages to Singapore’s anti-scam hotline (1-800-722-6688) or report via the ScamShield app
- Monitor Personal Accounts:
- While voter data may not be affected, increased vigilance for unusual account activity is advisable
- Set up alerts for financial accounts as a precautionary measure
This incident underscores the evolving cybersecurity challenges facing electoral systems globally. Third-party vendor compromises can potentially impact voter confidence even when core election infrastructure remains secure.
Singapore-Specific Anti-Scam Guidance Following the TNT Ransomware Attack

In light of the ransomware attack on Toppan Next Tech (TNT) ahead of Singapore’s GE2025, here are specific anti-scam measures tailored to the Singapore context:
Know Singapore’s Official Channels
- The Elections Department (ELD) communicates through official government websites (*.gov.sg domains) and verified social media accounts.
- Official election notices in Singapore are typically sent through registered mail with clear government markings.
- Legitimate SMS notifications from government agencies in Singapore will come from sender IDs like “GOVSG” and won’t contain clickable links.
Singapore-Specific Reporting Mechanisms
- Report scams to the Singapore Police Force via the Anti-Scam Hotline at 1-800-722-6688
- To report and block scam messages, you can use the ScamShield app, developed by the National Crime Prevention Council (NCPC) and the Singapore Police Force.
- Submit scam reports through the Singapore Police Force’s I-Witness portal (www.police.gov.sg/i-witness)
- Contact the Cyber Security Agency of Singapore (CSA) at 6323 5052 for cybersecurity incidents.
Common Singapore Election Scams to Watch For
- Fake poll card replacement services claiming your card was affected by the breach
- Impersonation of ELD officials requesting NRIC verification “due to data issues”
- Phishing sites mimicking the ELD voter services portal
- WhatsApp messages with false information about polling station changes
- Fake surveys offering compensation for “election feedback” that steal personal information
Singapore-Specific Identity Protection
- Safeguard your NRIC number and protect your SingPass credentials – legitimate election processes won’t require you to share these online.
- ELD will never ask for your SingPass login information for election verification
- Be cautious with physical poll cards – don’t share photos of them on social media, as they contain personal information.
- Verify polling information via the official ELD website or call 1800-225-5353 if in doubt.
Banking Protections (Given That TNT’s Banking Clients Were Affected)
- Enable Bank SMS/app alerts for all transactions through your Singapore bank’s security settings.
- Utilize two-factor authentication features offered by Singapore banks
- Contact DBS (1800-111-1111) or Bank of China Singapore (6532-6678) directly if you believe you might be affected
- Be especially vigilant for banking-related scams in the coming weeks, as scammers may try to exploit news of the breach
Stay Informed Through Official Sources
- Follow official ELD announcements via gov.sg, the Elections Department website, or official government social media
- Check news updates from reliable Singapore media sources like The Straits Times, CNA, or TODAY.
- Use the ScamAlert.sg website maintained by the National Crime Prevention Council for updates on active scams.
- Consider signing up for Scam Alert notifications from the Singapore Police Force.
Remember that Singapore has strong institutional safeguards for election integrity, and voters should remain calm while exercising appropriate caution regarding their personal information.
Analysis of Malware Scams with a Focus on Singapore
Current Malware Scam Landscape in Singapore
Based on the article you shared, Singapore is experiencing a significant malware scam problem:
- Recent variant involves fake ads on Facebook and TikTok for travel and cleaning services
- At least 82 cases have been reported since December 2024, with $625,000 in losses
- The first half of 2024 saw overall scam losses of $385.6 million from 26,587 cases
- APK-based malware targeting Android devices is a common attack vector
How These Malware Scams Work
- Initial Contact: Scammers advertise fake services on social media platforms
- Building Trust: Communication moves to WhatsApp, creating a more personal connection
- Small Initial Payment: Requesting only $5 creates a low-risk perception for victims
- Technical Barrier: Payment “issues” create a problem the victim wants resolved
- Malware Installation: Victims are guided to download malicious APK files
- Security Bypass: Victims may be instructed to disable protective features like Google Play Protect
- Device Compromise: Malware enables remote access and theft of sensitive data, including OTPs
- Financial Loss: Unauthorized transactions are conducted using stolen credentials
Prevention Methods
Technical Safeguards
- App Installation Restrictions:
- Only download apps from official stores (Google Play Store, Apple App Store)
- Never disable Google Play Protect or similar security features
- Enable “Block installation from unknown sources” on Android devices
- Device Security:
- Keep operating systems and apps updated
- Use reputable mobile security software
- Enable biometric authentication for banking apps
- Use app locks for financial and messaging applications
- Payment Security:
- Enable two-factor authentication (2FA) for all financial accounts
- Use physical security keys or authenticator apps instead of SMS-based 2FA where possible
- Set up transaction alerts and spending limits

Behavioral Safeguards
- Verification Practices:
- Verify company legitimacy through official channels before engaging
- Contact businesses through their official websites/numbers, not links provided in ads
- Be skeptical of unusually low prices or membership fees
- Link Hygiene:
- Never enter financial information through links sent via WhatsApp or other messaging apps
- Verify website URLs carefully before entering credentials
- Use bookmarks for financial sites rather than following links
- Payment Red Flags:
- Be suspicious when asked to download apps to “fix” payment issues
- Legitimate businesses have established payment processes that don’t require unique apps
- Never share OTPs with anyone, even those claiming to be customer service
Singapore-Specific Application
- Use Local Safeguards:
- ScamShield app (developed by the Singapore government)
- National Crime Prevention Council’s X (formerly Twitter) scam alerts
- Singapore Police Force’s anti-scam resources
- Financial Protection Measures:
- Use PayNow’s transaction limit features
- Set up OCBC’s “kill switch” or similar features offered by DBS, UOB and other local banks
- Register for bank SMS alerts for all transactions
- Reporting Channels:
- Singapore Police Force’s Anti-Scam Centre: 1-800-255-0000
- Report scams at www.police.gov.sg/iwitness
- Use Scam Alert website (www.scamalert.sg)
- Cultural Context Awareness:
- Be especially cautious during cultural festivals when scammers may leverage seasonal services
- Watch for scams targeting specific communities (e.g., domestic helpers, international students)
- Be aware that scammers may exploit the “kiasu” (fear of missing out) mentality with limited-time offers
Recommended Action Plan for Singaporeans
- Immediate Steps:
- Check devices for unknown apps and remove them
- Update financial passwords and enable additional security features
- Review recent bank transactions for unauthorized activity
- Medium-Term Habits:
- Follow the Singapore Police Force’s “ACT” framework (Add security, Check for signs, Tell others)
- Create separate email addresses for financial services and social media
- Regularly check the Scam Alert website for new scam patterns
- Long-Term Protection:
- Participate in digital literacy programs offered by community centers
- Consider cyber insurance coverage
- Create family protocols for verifying unusual financial requests
Implementing these prevention methods, with specific attention to Singapore’s context, can significantly reduce residents’ risk of falling victim to malware scams.

Anti-Scam Centre Assistance in Singapore
Singapore Police Force Anti-Scam Centre (ASC)
The Anti-Scam Centre (ASC) was established by the Singapore Police Force in 2019 as a specialized unit to combat scams. Here’s how they can assist victims and the public:

Services Provided
- Immediate Response for Victims:
- Hotline: 1-800-255-0000 (24/7 Police Hotline)
- Online reporting: www.police.gov.sg/iwitness
- Walk-in assistance at Neighbourhood Police Centres
- Fund Recovery Assistance:
- Works with local banks to freeze suspicious accounts
- Coordinates with financial institutions to trace and recover funds
- Faster response time through direct partnerships with banks
- Evidence Collection:
- Helps preserve digital evidence
- Provides guidance on documenting communications with scammers
- Assists in securing compromised devices
- Case Management:
- Assigns specialized officers to handle scam cases
- Provides case progress updates
- Coordinates with other law enforcement agencies when scams cross borders

What to Prepare When Seeking Help
- Essential Information:
- Screenshots of all communications with scammers
- Transaction details and receipts
- Bank account numbers involved
- Contact information used by scammers
- Timeline of events
- Device Information:
- If malware was involved, preserve the device in its current state
- Note any apps installed at the scammer’s request
- Document changes made to device settings
- Financial Records:
- Bank statements showing suspicious transactions
- Credit/debit card statements
- Digital payment service records (PayNow, PayLah!, etc.)

Prevention Support
The ASC also provides preventive assistance:
- Educational Resources:
- ScamAlert.sg website with updated information on scam types
- Public awareness campaigns
- Educational materials in multiple languages
- Early Warning System:
- Alerts about emerging scam trends
- SMS alerts for potential victims
- Social media advisories
- Verification Services:
- The police hotline can verify if calls claiming to be from government agencies are legitimate.
- Bank account checking services to verify suspicious accounts.

How to Maximize ASC Assistance
- Report Promptly:
- Time is critical in fund recovery – report within 24 hours
- Don’t wait to gather all evidence before making initial contact
- Follow up with additional information as it becomes available
- Follow Instructions Precisely:
- ASC officers will provide specific steps to secure accounts
- Complete all recommended actions to prevent further losses
- Maintain communication with assigned officers
- Spread Awareness:
- Share case details (without personal information) with family and friends
- Report scam messages to relevant platforms (Facebook, WhatsApp, etc).
- Support community awareness initiatives.

Recent Enhancements
Since its establishment, the ASC has continuously improved its capabilities:
- Faster Response Times:
- Streamlined processes for quicker fund freezing
- Enhanced coordination with financial institutions
- Expanded Partnerships:
- Works with telecommunications companies to block scam calls
- Collaborates with social media platforms to remove scam advertisements
- International cooperation with foreign law enforcement agencies
- Technology Adoption:
- Improved data analytics to identify scam patterns
- Enhanced capabilities to track digital money flows
By promptly and thoroughly utilizing the resources of Singapore’s Anti-Scam Centre, victims can maximize their chances of recovering funds and preventing further losses while contributing to broader efforts to combat scams nationwide.
Infostealer Malware
Infostealer malware has emerged as one of the most significant cybersecurity threats in recent times, casting a wide net over unsuspecting users. This type of malware comes in various forms, each with its distinct name and functionality. Alarmingly, some of these malicious tools are available as subscription-based services, allowing cybercriminals to pay monthly fees for access—much like a Netflix subscription.
The economy surrounding infostealer malware is thriving. A recent report from Kaspersky revealed that a staggering 25 million users were targeted between the beginning of 2023 and the end of 2024. This surge highlights the growing sophistication and prevalence of these attacks.
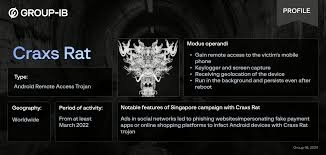
Infostealers are particularly insidious, explicitly designed to capture valuable personal information. They can extract bank card details, login credentials, and even sensitive media files, leaving victims vulnerable to financial loss and identity theft.
As this threat continues to evolve, it becomes increasingly crucial for individuals to stay informed and vigilant. Protect yourself by signing up for resources like Kurt’s The CyberGuy Report, which offers security alerts and expert tech tips tailored to keep you safe in the digital world. Awareness is your first line of defence against these lurking dangers.
A newly published report from Kaspersky Digital Footprint Intelligence paints a grim picture of the cybersecurity landscape for 2023 and 2024. Alarmingly, nearly 26 million devices fell victim to infostealer malware during this period. Among the casualties, more than 2 million unique bank card details were leaked, underscoring the extensive reach of cyber criminals.
Perhaps the most shocking revelation is that one in every 14 infections resulted in stolen bank card data. The implications of such breaches extend beyond mere financial loss; passwords, second-factor authentication cookies, and other sensitive credentials were also compromised, leaving users vulnerable to further attacks.
Kaspersky analysts highlighted a significant uptick in infections in 2024, primarily driven by specific strains of malware. RisePro, which accounted for only 1.4% of infections in 2023, skyrocketed to an alarming 22.45% in 2024. Meanwhile, Stealc—a newer threat first identified in 2023—also gained momentum, increasing its share from 2.65% to 13.33%.
Despite the emergence of these new threats, Redline maintained its notorious status as the most widespread infostealer, responsible for a staggering 34.36% of all infections. As the digital landscape evolves, the need for robust cybersecurity measures has never been more critical.

By August 2024, researchers unveiled a staggering statistic: an estimated 15.9 million devices had fallen victim to infostealer malware throughout the previous year. This alarming trend painted a bleak picture of the cybersecurity landscape, indicating that malicious actors were becoming increasingly sophisticated.
However, as the calendar turned to March 2025, the situation worsened. The number of infected devices surged to 16.49 million, surpassing earlier predictions by a striking 3.69%. This unexpected rise left many experts scrambling to reassess their forecasts and strategies.
Adding to the concern, new log files from 2023 continued to emerge on dark web platforms. This influx of data hinted at the possibility that the actual number of infections could be even higher than initially believed.
As researchers delved deeper, they found that over 9 million infections had already been tracked for 2024 alone. With this figure still climbing, it became clear that the final tally for the year would likely exceed the previous year’s numbers, though not by a substantial margin.
The relentless spread of info stealer malware served as a stark reminder of the ongoing battle between cybercriminals and those dedicated to safeguarding digital spaces.
In today’s digital landscape, where infostealer malware infections are surging at an alarming rate, and cybercriminals are becoming increasingly cunning, it is more important than ever to take steps to safeguard your sensitive data. The threat to your bank cards and passwords is very real, but there are several effective strategies you can adopt to fortify your defences. Here are six thoughtful approaches that can help you protect your financial information.
First and foremost, investing in robust antivirus software is a fundamental step. Picture this: you install a powerful antivirus program on all of your devices, ensuring they are shielded from the ever-evolving threats lurking online. It’s not just about installation; keeping the software updated regularly is essential. This vigilant protector scans for potential threats, identifying and eliminating them before they can wreak havoc on your system. Imagine the peace of mind that comes with knowing your devices are equipped to combat malicious links that might attempt to infiltrate your private information. Furthermore, a good antivirus solution will alert you to phishing attempts and ransomware threats, acting as a digital guardian for your data and assets. If you’re curious about which antivirus software stands out in 2025, I have some recommendations that cater to Windows, Mac, Android, and iOS platforms.
Next, consider the innovative option of using virtual cards for online transactions. Instead of exposing your actual bank card details, you can generate temporary virtual cards through your bank or services like Privacy.com. These disposable cards serve as a protective layer, minimising the risk of your information being compromised in the event of a data breach. This simple yet effective strategy can significantly limit the fallout from any security incidents.
Additionally, it is crucial to take charge of your finances. By enabling transaction alerts and setting daily spending limits on your cards, you place yourself in a proactive position. Imagine receiving instant notifications for every transaction made with your card; this immediacy allows you to detect unauthorised activities right away. With daily spending limits in place, you can further control your finances and mitigate potential losses.
By embracing these measures and incorporating them into your daily routine, you can create a formidable barrier against the threats posed by infostealer malware and cybercriminals. Your sensitive information deserves protection, and with these strategies at your disposal, you can navigate the digital world with confidence and security.
Navigating the Digital Landscape: A Cautionary Tale
In the vast expanse of the digital world, where convenience often dances hand-in-hand with risk, a wise traveller must tread carefully. One of the most perilous missteps is the act of storing card information within web browsers. With a cunning nature, info stealers lay in wait, targeting the autofill data that resides in popular browsers like Chrome, Edge, and Firefox. Imagine a pop-up appearing before you, innocuously asking if you’d like to save your payment information. It may seem harmless, but resist the temptation! Instead, opt for the safety of a robust password manager. Moreover, consider fortifying your defences with supplementary security measures such as two-factor authentication. As technology evolves, innovative methods like Face ID and Touch ID are beginning to supplant traditional passwords, offering a new layer of protection for your sensitive financial details.
As our digital journey continues, we encounter another pivotal aspect: passwords. The importance of maintaining strong passwords cannot be overstated. While adhering to all recommended password practices might not guarantee immunity from cyber breaches, it certainly helps bolster your defences. Since the exact desires of thieves remain shrouded in mystery, employing strong, frequently updated passwords is a prudent strategy. To simplify this task, I wholeheartedly recommend utilising a password manager—an invaluable tool that can generate and securely store complex passwords for you. For those seeking guidance on the best password managers available in 2025, further insights await.
Yet, the quest for security does not end there. Another layer of protection can be found in personal data removal services. While no service can promise to erase every trace of your existence from the internet, engaging with such a service offers a proactive approach to monitoring and managing your online footprint. These services can automate the often tedious process of eliminating your information from numerous websites over extended periods. If you’re curious about which data removal services stand out in this ever-evolving landscape, my curated recommendations are just a click away.
As we navigate this complex digital terrain, it’s crucial to remain vigilant against the threats posed by info stealers—malicious actors lurking in the shadows of our online lives. These threats are alarmingly prevalent, often masquerading as trustworthy applications or employing clever social engineering tactics to ensnare even the most discerning users. No one is entirely immune; even the most cautious among us can find ourselves ensnared by a meticulously crafted scheme.
Thus, the key to safeguarding oneself lies in exercising vigilance while exploring the web, downloading applications, or conducting financial transactions online. By leveraging tools like password managers and reliable antivirus software, we not only enhance our security but also streamline our digital experiences. In this grand narrative of our online existence, let us choose to be proactive heroes rather than unwitting victims, armed with knowledge and ready to face whatever challenges may arise in the realm of cyberspace.
In this age of digital connectivity, where our lives are interwoven with countless online accounts, many ponder a question: Have you embraced the convenience of a password manager, or do you find yourself still relying on the fragile faculties of memory or perhaps jotting down your passwords on scraps of paper?
Imagine a character in this narrative—let’s call her Clara. Each day, as she navigates the vast expanse of the internet, she faces the daunting task of keeping track of a multitude of passwords. With each new account she creates, a flicker of anxiety dances in her mind. Will she remember this one? Should she trust her memory, which can sometimes feel like a sieve? Or should she resort to scribbling those precious strings of characters on a notepad, leaving them vulnerable to prying eyes?
Clara often finds herself at a crossroads, contemplating the merits of modern solutions versus the age-old methods of recall and notation. In her heart, she knows there must be a better way—one that could alleviate the burden of remembering complex combinations and safeguard her online identity. Yet, as she sits at her computer, fingers poised over the keyboard, she wonders: Is it time to leap into the world of password managers, or will she continue to tread the familiar path of memorisation and note-taking?

Thus unfolds her journey—a tale not just about passwords but also about the choices we make in our digital landscape.
Secure browsing
When it comes to staying safe online, using a secure and private browser is crucial. Such a browser can help protect your personal information and keep you safe from cyber threats. One option that offers these features is the Maxthon Browser, which is available for free. It comes with built-in Adblock and anti-tracking software to enhance your browsing privacy.

Maxthon Browser is dedicated to providing a secure and private browsing experience for its users. With a strong focus on privacy and security, Maxthon employs strict measures to safeguard user data and online activities from potential threats. The browser utilises advanced encryption protocols to ensure that user information remains protected during internet sessions.
In addition, Maxthon implements features such as ad blockers, anti-tracking tools, and incognito mode to enhance users’ privacy. By blocking unwanted ads and preventing tracking, the browser helps maintain a secure environment for online activities. Furthermore, incognito mode enables users to browse the web without leaving any trace of their history or activity on the device.
Maxthon’s commitment to prioritising the privacy and security of its users is exemplified through regular updates and security enhancements. These updates are designed to address emerging vulnerabilities and ensure that the browser maintains its reputation as a safe and reliable option for those seeking a private browsing experience. Overall, Maxthon Browser offers a comprehensive set of tools and features aimed at delivering a secure and private browsing experience.
Maxthon Browser, a free web browser, offers users a secure and private browsing experience with its built-in Adblock and anti-tracking software. These features help to protect users from intrusive ads and prevent websites from tracking their online activities. The browser’s Adblock functionality blocks annoying pop-ups and banners, allowing for an uninterrupted browsing session. Additionally, the anti-tracking software safeguards user privacy by preventing websites from collecting personal data without consent.
By utilising the Maxthon Browser, users can browse the internet confidently, knowing that their online activities are shielded from prying eyes. The integrated security features alleviate concerns about potential privacy breaches and ensure a safer browsing environment. Furthermore, the browser’s user-friendly interface makes it easy for individuals to customise their privacy settings according to their preferences.
Maxthon Browser not only delivers a seamless browsing experience but also prioritises the privacy and security of its users through its efficient ad-blocking and anti-tracking capabilities. With these protective measures in place, users can enjoy the internet while feeling reassured about their online privacy.
In addition, the desktop version of Maxthon Browser works seamlessly with their VPN, providing an extra layer of security. By using this browser, you can minimise the risk of encountering online threats and enjoy a safer internet experience. With its combination of security features, Maxthon Browser aims to provide users with peace of mind while they browse.
Maxthon Browser stands out as a reliable choice for users who prioritise privacy and security. With its robust encryption measures and extensive privacy settings, it offers a secure browsing experience that gives users peace of mind. The browser’s commitment to protecting user data and preventing unauthorised access sets it apart in the competitive web browser market.