I’d be happy to help with this article about Chief Justice Sundaresh Menon’s speech to newly admitted non-practising lawyers in Singapore. Based on the article covers a few key points:
- Chief Justice Menon emphasised that all lawyers, including non-practising ones, play a crucial role in upholding the rule of law.
- Singapore has implemented a new framework that allows greater career flexibility for law graduates:
- Previously, Law graduates had to pass the Bar exam AND complete 6 months of practice training before admission
- Now: Graduates can be admitted as non-practising lawyers after passing the Bar exam without practice training
- Only those seeking to become practising lawyers need a practice training period (now extended to 1 year)
- The changes resulted from recommendations made by a committee formed in 2016 to review professional training for young lawyers.
- Key statistics mentioned:
- In-house counsel in Singapore: approximately 4,800 (as of April 2024)
- Lawyers in private practice: 6,348 (in 2024)
- Chief Justice Menon emphasised the ethical responsibilities of non-practising lawyers through two cautionary examples from other countries:
- The British post office IT scandal, where faulty systems led to wrongful convictions
- Australia’s Robodebt scheme, which produced inaccurate results and didn’t comply with regulations
Analysis of Singapore’s Bar Framework Changes and Implications for Non-Practising Lawyers
Based on the article, I can analyse the changes to Singapore’s legal profession entry framework and their implications for those seeking in-house counsel or other non-practising roles.
Changes to the Bar Examination Framework
From the article, the changes include:
- Separation of Bar admission from practice training:
- Previously, Law graduates had to pass the Bar exam AND complete 6 months of practice training to be admitted
- Now, Law graduates can be admitted as non-practising lawyers immediately after passing the Bar exam
- Raised standards of the Bar exam:
- The Chief Justice specifically mentioned “raising the standard and stringency of the Bar exam” as one of the recommendations implemented
- Unfortunately, the article doesn’t provide specific details about how the exam has been made more stringent
- Extended practice training period:
- For those wishing to become practising lawyers, the training period has doubled from 6 months to 1 year
- This only applies to those seeking to practice law in traditional settings (e.g., appearing in court)
Implications for Lawyers Seeking In-House or Non-Practising Roles
This new framework offers several advantages for those seeking less stressful counsel roles:
- Accelerated Career Timeline:
- Graduates can now enter non-practising legal roles immediately after passing the Bar exam
- No need to spend 6 months in a potentially high-pressure practice training environment if their career goals lie elsewhere
- Greater Career Flexibility:
- The Chief Justice explicitly stated this was designed to provide “greater flexibility over career paths”
- Graduates can take different pathways, such as becoming in-house counsel or entering academia without delay
- Recognition of Non-Practising Legal Roles:
- The new framework acknowledges the importance and distinct nature of in-house counsel roles
- The statistics (4,800 in-house counsel vs. 6,348 practising lawyers) show that this is nearly half the legal profession
- Maintained Professional Standards:
- While the path is more flexible, the Chief Justice emphasised that non-practising lawyers remain “officers of the court” with ethical duties
- This preserves the professional standing of in-house counsel while acknowledging their different career trajectory
- Potential Stress Reduction:
- By eliminating the mandatory practice training requirement for those who don’t intend to practice traditionally, this may reduce burnout for those who know they want in-house roles
- However, the increased stringency of the Bar exam may offset some of this stress reduction
The Chief Justice’s emphasis on the ethical responsibilities of in-house counsel suggests that while the pathway may be less stressful in terms of traditional practice requirements, non-practising lawyers still bear significant responsibilities that impact “not only their companies, but also society at large.”
This reformed framework appears to be responding to the reality that many law graduates seek careers outside traditional practice while still maintaining professional standards across all segments of the legal profession.
Impact of AI on Singapore’s Legal Framework Changes
Based on the article provided, there’s no direct mention of AI’s influence on these legal framework changes. However, I can analyze potential ways AI may impact this new system for non-practising lawyers seeking in-house counsel roles:
Potential AI Impacts on the New Legal Framework
1. Changing Nature of In-House Counsel Work
- Legal Research and Due Diligence:
- AI tools like large language models and legal research platforms can dramatically reduce time spent on legal research
- In-house counsel may increasingly supervise AI that handles first-pass document review, potentially changing skill requirements
- Contract Analysis and Management:
- AI contract review tools can analyze agreements faster than humans
- Non-practicing lawyers may need to develop skills in prompt engineering and AI output verification rather than manual contract review
2. Implications for Legal Education and Bar Exams
- Updated Bar Exam Content:
- The “raised standards and stringency” mentioned may need to include testing on AI literacy and understanding technology’s limitations
- New lawyers may need to demonstrate competence in legal tech and AI oversight
- Training Requirements:
- The separation of Bar admission from practice training creates space to incorporate AI-specific skills training
- In-house counsel may need different AI training than traditional practitioners
3. Oversight and Ethical Considerations
- AI Governance Role:
- Non-practising lawyers in companies may increasingly serve as ethical AI implementers
- Chief Justice Menon’s emphasis on in-house counsel’s impact “on society at large” becomes especially relevant with AI deployment
- New Ethical Challenges:
- The cautionary examples given (British post office IT scandal and Australian Robodebt) highlight how technological systems can create legal and ethical failures
- AI systems present similar or greater risks that in-house counsel must be equipped to identify and manage
4. Market Shifts
- Changing Value Proposition:
- As AI handles routine legal tasks, in-house counsel roles may shift toward strategic advisory work
- This could actually increase the attractiveness of non-practising paths as they evolve to focus on higher-value work
- New Career Specialisations:
- The flexibility in the new framework could allow for specialisation in AI legal issues
- Hybrid roles combining legal and technical expertise may emerge, particularly in in-house settings
Conclusion
While AI wasn’t explicitly mentioned in relation to Singapore’s legal framework changes, these reforms coincide with a technological shift that’s transforming legal practice. The separation of Bar admission from practice training creates a system potentially more adaptable to technological change, allowing non-practising lawyers to develop specialised skills relevant to AI governance and oversight.
The Chief Justice’s emphasis on maintaining high ethical standards and public trust becomes even more critical as in-house counsel increasingly oversee AI systems that, like the examples he cited, could create systemic problems if not properly governed. The framework changes may have unintentionally created a more AI-ready legal profession in Singapore.
. This is concerning information about fraudsters impersonating lawyers and creating fake law firms to deceive people.
Based on the article from May 2021, here are the key points:
- Scammers were creating bogus law firms, impersonating lawyers, and using phishing attacks to trick people into giving them money.
- The Law Society of Singapore reported seven cases of scams related to law firms or lawyers over three years.
- One example involved a fake “Goh Keng Law Firm” that:
- Used photos of real lawyers
- Copied client reviews from legitimate firms
- Required “commitment fees” before taking cases
- Another case involved scammers creating a website that mimicked a Singapore law firm but changed references to Singapore with a Chinese city name.
- In one instance, scammers attempted to redirect mortgage loan payments to foreign bank accounts.
- The Law Society recommended that people:
- Check the official public directory of lawyers and law firms
- Review examples of scams on the Law Society’s website
- Verify any payment instructions with their lawyers directly
- Be cautious about instructions that deviate from previous communications
These types of scams seem to be growing more sophisticated as more people conduct business online. It’s a good reminder to verify the identity of legal representatives through official channels before making any payments.
Analysis of Fake Lawyer Scams in Singapore
Based on the article, I can provide an analysis of fake lawyer scams in Singapore and prevention strategies:
Types of Scams
- Bogus Law Firms: Creating entirely fake law firms with professional-looking websites
- Example: “Goh Keng Law Firm” with stolen photos of real lawyers
- Use of copied client reviews to appear legitimate
- Lawyer Impersonation: Scammers pretending to be actual lawyers
- Phishing Attacks: Fraudulent emails claiming to be from legitimate law firms
- Example: Requesting changes to payment instructions for mortgage loans
- Attempting to redirect funds to foreign bank accounts
- Website Cloning: Duplicating legitimate law firm websites with minor modifications
- Example: Adding a Chinese city name to a Singapore law firm’s identity
- Replicating lawyer profiles and firm content
Trends and Contributing Factors
- Increasing Frequency: Seven reported cases over three years (as of May 2021)
- Growing Sophistication: Scammers are employing more advanced techniques
- Digital Shift: More Singaporeans are conducting legal transactions online, creating opportunities for scammers
Prevention Strategies in Singapore
- Official Verification:
- Check the Legal Services Regulatory Authority’s public directory of lawyers and law firms
- The directory includes even inactive law practices for reference
- Payment Verification:
- Confirm directly with your lawyer before making any payments
- Be suspicious of unexpected changes to payment instructions
- Verify any fund transfer instructions that differ from previous communications
- Public Awareness:
- The Law Society maintains examples of online scams on their website
- Public education on recognizing red flags
- Takedown Notices:
- Legal action to remove fraudulent websites
- Though noted in the article that international enforcement can be challenging
- Due Diligence:
- Be wary of law firms requiring upfront “commitment fees”
- Verify law firm credentials through multiple official channels
These scams highlight the importance of verifying through official channels and taking extra precautions when making payments related to legal services. Their evolving nature suggests that prevention strategies must also continue to adapt.
Applying to Singapore Courts for Relief Against Fake Lawyer Scams

Based on the information in the article, here’s guidance on how victims of fake lawyer scams might seek relief through Singapore’s courts:
Legal Remedies Available
- Civil Proceedings:
- File a civil suit against perpetrators (if identified) for fraud, misrepresentation, or damages
- Seek monetary compensation for financial losses
- Injunctive Relief:
- Apply for court orders to immediately take down fraudulent websites
- Request cease and desist orders against impersonators
- Police Reports:
- File a police report, which may lead to criminal proceedings
- Criminal cases would then be prosecuted by the state if sufficient evidence exists
Application Process
- Engage a Legitimate Lawyer:
- Verify their credentials through the Legal Services Regulatory Authority’s directory
- Seek representation from a lawyer experienced in fraud cases
- Document Collection:
- Gather all communications with the fraudulent entity
- Compile evidence of payments made
- Document attempts to verify the legitimacy of the “law firm”
- Preserve screenshots of fraudulent websites or communications
- File Originating Claims/Summons:
- Submit formal legal claims through Singapore’s courts
- State Courts for claims below S$250,000
- High Court for claims above S$250,000
- Interim Orders:
- Request urgent interim orders to freeze assets or remove online content
- Can be done through applications for urgent hearings
Collaborative Approaches
- Work with Law Society:
- Report the scam to the Law Society of Singapore
- The Society may assist in takedown efforts, as demonstrated by their engagement of Ghows law firm in the article
- Engage Regulatory Bodies:
- Report to the Monetary Authority of Singapore for financial fraud aspects
- File complaints with the Infocomm Media Development Authority for online scams
- International Cooperation:
- For scams with international elements, courts may need to issue orders with cross-border effect.
- Singapore courts can sometimes request assistance from foreign jurisdictions.
This approach combines preventive measures with legal remedies available through Singapore’s court system to address fake lawyer scams comprehensively.
Anti-Scam Protection Infrastructure in Singapore
Singapore has developed one of the most comprehensive anti-scam ecosystems in the region:
ScamShield System
- ScamShield App: A government-developed mobile application that:
- Filters and blocks potential scam calls and messages
- Allows users to verify suspicious contacts and websites
- Provides real-time scam alerts and updates
- ScamShield Helpline (1799): A dedicated hotline for scam verification and reporting.
- ScamShield Website: An Educational resource with updated information on current scam tactics.
Banking Security Measures
- Transaction Limits: Singapore banks implement customizable transaction limits for online banking.
- Multi-Factor Authentication: Required for significant banking transactions.
- Rapid Response Protocols: Banks have specialized teams to freeze accounts and attempt fund recovery when scams are reported quickly.
Coordinated Response Framework
- Anti-Scam Centre: Established by the Singapore Police Force to coordinate investigations and recovery efforts.
- Inter-Ministry Committee on Scams: Facilitates collaboration between government agencies.
- Project FRONTIER: A partnership between police, banks, and telecommunications companies to share intelligence and block scam operations.
Public Education Campaigns
The “ACT Against Scams” framework (Add, Check, Tell) represents Singapore’s public education approach, focusing on:
- Proactive security measures
- Verification through official channels
- Community information sharing
Effectiveness and Challenges
Despite these measures, the S$9.6 million in losses from this scam variant alone suggests significant challenges:
- Cross-Border Enforcement: Many scammers operate outside Singapore’s jurisdiction.
- Evolving Tactics: Scammers continuously adapt to circumvent security measures.
- Psychological Manipulation: Even well-educated individuals fall victim when under pressure or emotional manipulation.
The Singapore authorities are continuously refining their approach, with the ScamShield ecosystem representing one of the most innovative government responses to digital scams globally.
Anti-Scam Centre (ASC) Assistance in Singapore
How the Anti-Scam Centre Can Help
The Anti-Scam Centre (ASC) in Singapore offers several key services to scam victims and the broader public:
For Scam Victims
- Immediate Assistance:
- Report scams through the Police Hotline (1800-255-0000)
- Use the online I-Witness reporting portal (www.police.gov.sg/i-witness)
- In urgent cases requiring immediate intervention, dial 999
- Fund Recovery Assistance:
- ASC coordinates with banks to freeze suspicious accounts
- Works to recover transferred funds when possible
- The speed of reporting is critical—immediate reporting increases recovery chances
- Case Investigation:
- Documents scam incidents and collects evidence
- Tracks patterns to identify scam networks
- Builds cases for prosecution when perpetrators can be identified
For the General Public
- Scam Prevention Resources:
- Educational materials about current scam types
- Verification services for suspicious contacts
- Access to the ScamShield app and other protective tools
- Awareness Programs:
- Community outreach sessions
- Targeted education for vulnerable populations
- Regular updates on emerging scam tactics
How to Access ASC Services
- Reporting Channels:
- Police Hotline: 1800-255-0000
- Online: www.police.gov.sg/i-witness
- ScamShield Helpline: 1799 (for verification of suspicious contacts)
- What Information to Provide:
- Details of all communications with scammers
- Transaction records and receipts
- Screenshots of conversations and websites
- Phone numbers and account details used by scammers
- Follow-up Process:
- Cases are assigned a reference number
- Investigation officers may contact victims for additional information
- Recovery progress updates are provided when available
ASC’s Operational Approach
The ASC operates with a “time is of the essence” philosophy, focusing on:
- Speed: Rapid intervention to freeze accounts before funds are dissipated
- Coordination: Direct lines of communication with financial institutions
- Intelligence: Data analytics to identify scam patterns and networks
- Prevention: Using case insights to strengthen public awareness efforts
The ASC has recovered millions of dollars for scam victims since its establishment, though recovery becomes significantly more challenging after the first 24 hours following a scam.
Singapore’s Anti-Scam Centre (ASC) Measures
Based on the information available, here’s an analysis of the Anti-Scam Centre’s approach and measures:
Core Functions and Capabilities
- Rapid Response System
- The ASC is mentioned in the article as an entity that scammers impersonate
- Works with banks to trace and freeze accounts linked to scam proceeds
- Collaborates with telecommunication companies to terminate phone lines used in scams
- Coordination Role
- Partners with Commercial Affairs Department’s Anti-Scam Command (ASCom)
- Facilitates multi-agency operations like the recent islandwide blitz
- Serves as a centralized hub for scam prevention and intervention

Intervention Strategies
- Disrupting Financial Networks
- Freezing accounts to prevent scammers from accessing funds
- Seizing suspected proceeds (nearly $1M in the recent operation)
- Targeting money mules who provide banking infrastructure
- Technical Countermeasures
- Working with telecoms to terminate scam-linked phone lines (700+ in the recent operation)
- Likely monitors digital communications channels for scam patterns
- Public Education
- Issues reminders about legitimate government communications:
- Government officials never request money transfers
- Official entities don’t ask for banking, SingPass, or CPF information over the phone
- Issues reminders about legitimate government communications:

Results and Impact
The recent operation demonstrates the ASC’s effectiveness:
- Over 30 arrests
- 240+ bank accounts frozen
- Nearly $1M in proceeds seized
- 700+ phone lines terminated
Strategic Approach
The ASC appears to employ a three-pronged strategy:
- Preventive measures – Public education and awareness campaigns
- Detective measures – Identifying and tracking scam operations
- Reactive measures – Freezing accounts, making arrests, and recovering proceeds
Challenges
Despite these efforts, the high volume of cases (1,504 reported government impersonation scams in 2024) and significant losses ($151.3M) suggest ongoing challenges in:
- Keeping pace with evolving scam techniques
- Reaching vulnerable populations before they become victims
- Addressing cross-border aspects of scam operations
General Scam Prevention Tips
- Trust your instincts
- If an offer seems too good to be true, it probably is
- Keep personal and financial information confidential
- Stay informed about the latest scam techniques
- Report suspicious activities to authorities
- Educate family members, especially older relatives
- Use secure, updated technology
- Maintain a healthy level of skepticism online

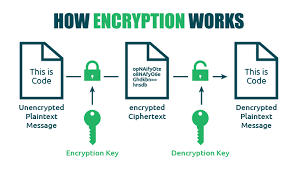
How Encryption Works

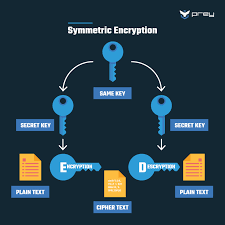
Encryption utilises mathematical algorithms to transform plaintext (readable data) into ciphertext (encrypted data). Only those with the decryption key can convert the ciphertext back into usable information. There are two main types:
- Symmetric Encryption: Uses the same key for encryption and decryption. It’s efficient but requires a secure key exchange.
- AsymmetEncryptiontion uses a pair of keys—a public key for encryption and a private key for decryption—to allow secure communication without prior key exchange.
Key Encryption Applications for Privacy
Device Encryption
- Full-disk encryption: Protects all data on your computer or smartphone (BitLocker for Windows, FileVault for Mac, builtEncryptiontion for iOS and Android)
- File-leEncryptiontion: Protects individual files and folders

Communication Encryption
- HTTPS: Secures website connections (look for the padlock icon in your browser)
- End-to-Encryption: Used in messaging apps like Signal, WhatsApp, and others to ensure only you and your recipient can read messages
- Email encryption: Options include PGP (Pretty Good Privacy), S/MIME, or encrypted email services
Network Encryption
- VPNs: Create an encrypted tunnel for all your internet traffic
- Wi-Fi encryption: WPA3 is the current most substantial standard for wireless networks
Cloud Storage Encryption
- At-rEncryptiontion: Protects stored data
- Zero-knowledge encryption: The provider has no access to your encryption keys
- Client-sEncryptiontion: Data is encrypted before leaving your device

Implementing Encryption in Your Digital Life
- Enable device encryption on all your computers and mobile devices
- Use encrypted messaging apps for sensitive communications
- Verify HTTPS connections when sharing personal or financial information
- Consider encrypted email for sensitive communications
- Choose cloud services with strong encryption policies
- Use a VPN when connecting to public Wi-Fi networks
- Password-protect and encrypt sensitive files and backups
Limitations to Consider
- Encryption can’t protect against malware already on your device
- Weak passwords can undermine even the strongEncryptiontion
- Encryption doesn’t hide metadata (who you’re communicating with, when, how often)
- Some countries have laws limiting encryption use or requiring backdoors

Encryption is a fundamental aspect of digital privacy that works best as part of a comprehensive security strategy. By understanding and implementing appropriate encryption methods, you can significantly enhance your online privacy protection.
.
Identity Theft
Identity theft is a pervasive form of fraud that can have devastating consequences for victims. In this crime, the perpetrator steals an individual’s personal information to assume their identity. This stolen information can often be gathered from discarded documents such as bank statements, utility bills, or even phishing scams.
Once armed with this data, the criminal may choose to open accounts in the victim’s name, a process known as application fraud. They might apply for credit cards, loans, or utility services under pretences, leaving the unsuspecting victim to deal with the aftermath.
The emotional toll of identity theft can be immense. Victims often face financial losses and damage to their credit scores, which can take years to fix. In today’s digital age, account takeovers have become a prevalent threat to unsuspecting victims. Criminals typically employ tactics such as phishing, vishing, or smishing to manipulate individuals into revealing their personal information.

Phishing often involves deceptive emails that appear to come from legitimate sources. These emails may prompt the victim to click on malicious links or provide sensitive details under the guise of verifying their identity.
Vishing, or voice phishing, involves phone calls in which scammers impersonate bank representatives or trusted entities to extract confidential information directly from the victim. Similarly, smishing involves text messages that lure individuals into divulging critical data.
Once armed with this personal information, the criminal can easily convince a bank to change the account holder’s address. This deception allows them full access to the victim’s financial accounts and resources.

Additionally, some criminals are skilled enough to bypass bank interaction altogether. They can use the obtained credentials to log into online accounts directly, executing unauthorized transactions without needing any further verification.
The consequences for victims can be devastating, leading not only to financial loss but also to emotional distress as they recover their stolen identities and secure their accounts. Consequently, individuals must remain vigilant and understand these risks to protect themselves against potential account takeovers for repair. Additionally, they may find themselves tangled in legal disputes as they try to prove their innocence.

Recovering from such a violation requires diligence and time, making it crucial for individuals to safeguard their personal information vigilantly. Implementing measures like shredding sensitive documents and monitoring credit reports can help prevent these types of crimes before they occur.t to Emerging challenges incorporate regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
Analysis of Scam Types and Prevention in Singapore

Based on the document, here’s an analysis of the scam types prevalent in Singapore and the prevention strategies being implemented:
Main Scam Types
- Self-Effecting Transfer Scams
- Most common type where victims willingly transfer money to scammers
- Psychological tactics target emotions like desire for companionship, respect for authority, and greed
- Victims often refuse to believe they’re being scammed

- Malware and Phishing Attacks
- Target bank accounts and online credentials
- Often involve sophisticated technical deception
- Phone/SIM-Based Scams
- Scammers using local phone numbers to make calls and send SMS
- Creates a false sense of legitimacy
- Cryptocurrency Scams
- Fake crypto trading interfaces that simulate profits
- Malware/phishing to drain crypto wallets
- Requesting victims convert money to cryptocurrency to evade banking safeguards
- Social Media and Messaging App Scams
- 60% of scams occur through these platforms
- Telegram specifically mentioned as a platform of concern (scam reports doubled in 2024)

Prevention Strategies
Government Regulatory Measures

- Protection from Scam Bills (January 2025)
- Empowering police to temporarily restrict banking transactions as a last resort
- Target cases where victims refuse to believe they’re being scammed
- SIM Card Regulations
- Limits on post-paid SIM card ownership
- Criminalization of SIM card misuse and transfer
- Penalties for SIM card abuse in scams
- Online Criminal Harms Act
- Requires online services to implement anti-scam measures
- Encourages robust user verification against government-issued IDs
- Potential for additional legislative action against platforms like Telegram
Banking/Financial Protection

- Enhanced Authentication
- FIDO-compliant hardware tokens being studied
- Requires physical proximity for transaction authentication
- Transaction Safeguards
- Cooling-off periods for high-risk transactions
- Enhanced fraud analytics
- Information sharing on money mule accounts
- Cryptocurrency Protection
- Working with MAS-licensed digital payment token providers
- Strengthening operational links with law enforcement

Public Education and Empowerment
- ScamShield Suite
- Launched September 2024
- Allows the public to check, report, and stay updated on scams
- ScamShield hotline (1799) for assistance
- Targeted Awareness Campaigns
- Monthly media campaigns
- Tailored to vulnerable population segments for specific scam types

Key Challenges and Trends
- Rising Financial Impact
- Total losses reached $1.1 billion in 2024 (a 70% increase from 2023)
- Evolving Tactics
- Scammers pivoting to local phone numbers
- Increased use of cryptocurrency to evade banking safeguards
- Exploitation of anonymity on messaging platforms
- Cross-Platform Nature
- Requires collaboration between government, tech companies, and financial institutions
- International dimension (implied by sophisticated criminal syndicates)

The Singapore approach appears multifaceted. It combines regulatory powers, technological solutions, industry collaboration, and public education to create a comprehensive anti-scam ecosystem. The emphasis on both preventive measures and empowering individuals to recognize scams suggests a balanced strategy to address this growing threat.
Maxthon

Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorized access attempts from intruders.
Maxthon private browser for online. This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to protecting its users. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, knowing that their information is continuously safeguarded against emerging threats in cyberspace.
