In-Depth Analysis of Online Privacy Protection Methods
1. Strong and Unique Passwords
Strong passwords are your first line of defence against unauthorised access. An effective password strategy includes:
- Length and complexity: Aim for at least 12-16 characters with a mix of uppercase and lowercase letters, numbers, and special characters.
- Password uniqueness: Using different passwords for each account prevents credential stuffing attacks, where hackers use breached credentials to access multiple accounts.
- Password managers, such as LastPass, Bitwarden, or 1Password, generate and securely store complex passwords. They encrypt your password database with a master password that only you know, allowing you to maintain unique passwords without needing to memorise them all.
- Passphrase approach: Consider using memorable phrases with substitutions and modifications, which can be both secure and easier to remember than random characters.
2. Two-Factor Authentication (2fa)
2fa adds a crucial second verification layer that significantly improves security:
- Types of 2fa: Authentication can be something you know (password), something you have (device), or something you are (biometric).
- Authentication apps: Google Authenticator, Authy, or Microsoft Authenticator generate time-based one-time passwords (TOTPS) that change every 30 seconds.
- SMS vs. app-based 2fa: While SMS is standard, it’s vulnerable to SIM swapping attacks. App-based authenticators are generally more secure.
- Hardware keys: Physical security keys, such as YubiKey, provide the strongest protection, requiring physical possession of the key to access accounts.
- Recovery options: Always set up recovery methods, such as backup codes or alternative email addresses, in case you lose access to your authentication device.
3. Public Wi-Fi Security
Public networks present significant risks that require protective measures:
- VPN functionality: Virtual Private Networks create an encrypted tunnel for your data, preventing eavesdropping on public networks. They mask your IP address and encrypt your connection to servers.
- HTTPS verification: Always ensure websites display the padlock icon and use HTTPS protocol, especially when entering sensitive information.
- Wi-Fi settings: Disable auto-connect features for public networks and turn off file sharing when on public Wi-Fi.
- Network validation: Verify network names before connecting, as attackers often create fake networks with similar names.
- Cellular alternative: Consider using your phone’s mobile hotspot instead of public Wi-Fi for sensitive transactions.
4. Social Media Privacy Settings
Social platforms collect extensive personal data, requiring careful configuration:
- Profile visibility: Limit who can view your posts, photos, and personal information (including birthdate, location, and contact details).
- Friend/Follower Approval: Enable manual approval for connection requests instead of automatic acceptance.
- Data Permissions: Review the information that apps connected to your social accounts can access.
- Location sharing: Disable automatic location tagging on posts and photos to prevent creating a map of your movements.
- Search visibility: Adjust settings to prevent search engines from indexing your profile.
- Regular privacy checkups: Many platforms offer privacy checkup tools to review all settings periodically.

5. Software and Device Updates
Keeping systems updated closes security vulnerabilities:
- Update mechanisms: Set automatic updates for operating systems, browsers, and applications when possible.
- End-of-life software: Replace software no longer receiving security updates, as these become increasingly vulnerable.
- Firmware updates: Don’t forget to update router firmware and Iot device software, which are often overlooked.
- Update verification: Download updates only from official sources to avoid malware disguised as updates.
- Update scheduling: Configure updates to install during low-usage periods to minimise disruption.
6. Phishing Protection
Defending against social engineering requires vigilance:
- Email verification: Check sender addresses carefully for subtle misspellings or domain variations.
- Link inspection: Hover over links to preview destinations before clicking; verify URLS match official domains.
- Attachment caution: Scan attachments before opening and be suspicious of unexpected files.
- Security indicators: Look for HTTPS and website security certificates when entering sensitive information.
- Context awareness: Be cautious of messages that create urgency or fear to prompt immediate action.
- Direct verification: Contact organisations directly through official channels when you receive suspicious communications.
- Email filtering: Use spam filters and security tools that can detect and flag potentially malicious messages.
7. Privacy-Focused Browsing
Browser choice and configuration significantly impact data collection:
- Privacy browsers, such as Firefox, Brave, and Tor Browser, offer enhanced privacy features compared to mainstream browsers.
- Search engines such as DuckDuckGo, Startpage, and Searx don’t track search history or build user profiles.
- Browser extensions, such as Privacy Badger, uBlock Origin, and HTTPS Everywhere, block trackers and enhance security.
- Cookie management: Regularly clear cookies or use browser settings to automatically delete them when you close the browser.
- Fingerprinting protection: Enable features that prevent websites from identifying your browser through its unique characteristics.
- Private browsing: Use incognito or private modes for sensitive searches, although these provide limited privacy benefits.
8. App Data Permissions
Controlling what information apps can access is crucial:
- Permission review: Regularly audit app permissions through your device settings.
- Minimal access: Grant only permissions necessary for core functionality; deny location access for apps that don’t need it.
- Alternative apps: Consider privacy-focused alternatives to data-hungry applications.
- Background activity: Disable background data access for non-essential apps.
- Periodic cleanup: Uninstall unused apps that may continue collecting data.
- Privacy Policies: Review the app’s privacy policies before installation to understand its data collection practices.
9. Online Presence Monitoring
Maintaining awareness of your digital footprint:
- Self-searching: Regularly search your name, email, and phone number across search engines.
- Data Broker Removal: Request the removal of your information from people-search sites, such as Spokeo, BeenVerified, and WhitePages.
- Breach notifications: Use services like Have I Been Pwned to monitor if your email appears in data breaches.
- Credit monitoring: Watch for unauthorised accounts or activity that could indicate identity theft.
- Social media audit: Review old posts and photos that might contain sensitive information.
- Digital reputation tools: Consider services that monitor your online presence and alert you to potential privacy issues.
10. Privacy Education
Staying informed about evolving threats and protections:
- Trusted resources: Follow privacy-focused organizations like Electronic Frontier Foundation (EFF) and Privacy Tools.
- Stay updated on major breaches and emerging threats by following cybersecurity news sources.
- Training resources: Take advantage of free online courses about digital privacy and security.
- Community forums: Participate in privacy-focused communities to learn from others’ experiences.
- Policy Awareness: Understand privacy regulations, such as GDPR or CCPA, that may provide you with legal rights.
- Regular reassessment: Privacy best practices evolve—regularly review and update your approach.
Implementing these in-depth strategies creates multiple layers of protection for your digital life, significantly reducing the risk of privacy breaches and unauthorised access to your personal information.

Privacy Notices and Policies
Privacy notices serve as the foundational communication between organisations and users regarding data practices. However, their effectiveness varies significantly:
- Transparency Level: While privacy policies disclose information collection practices, they often use complex legal language that obfuscates actual data usage. Many users accept terms without reading or understanding them.
- Implementation Gap: There’s frequently a gap between stated policies and actual data handling practices. Organisations might collect more data than necessary or use it in ways not clearly communicated to users.
- Enforcement Challenges: Without regulatory oversight, privacy policies can function as legal shields rather than user protections.
Regulatory Frameworks
The document mentions several key privacy regulations:
GDPR (European Union)
- Provides comprehensive rights including access, deletion, and portability
- Requires explicit consent for data processing
- Enforces significant penalties for non-compliance (up to 4% of global annual revenue)
- Sets global standards that affect companies worldwide
CCPA (California)
- Provides California residents right to know what data is collected
- Allows consumers to opt out of data sales
- Creates financial incentives for businesses to implement stronger privacy protections
- Has influenced similar legislation in other states
Electronic Communications Privacy Act
- Originally designed for telephone communications, but extended to electronic data
- Limits government access to private communications
- Has been criticised for outdated provisions that don’t address modern technology
Technical Privacy Protection Methods
Password Management
- Strong Passwords: The recommendation for unique passwords for each account is critical but often overlooked. Password complexity requirements should include:
- Minimum 12-16 characters
- Mix of uppercase, lowercase, numbers, and symbols
- Avoidance of dictionary words and personal information
- Password Managers: These tools store and generate complex passwords, reducing the vulnerability to password reuse. They typically employ end-to-end encryption to secure the password vault.
Multi-Factor Authentication (MFA)
- Types: The document mentions two-factor authentication, but this can be expanded to:
- Something you know (password)
- Something you have (phone, security key)
- Something you are (biometrics)
- Location-based verification
- Security Improvement: According to Microsoft research, MFA can prevent 99.9% of automated attacks, making it one of the most effective security measures.
Data Encryption
The document references encryption briefly, but this deserves deeper analysis:
- Transport Layer Security (TLS): Secures data in transit between user browsers and websites
- End-to-End Encryption: Protects communication content from being accessed by service providers
- Disk Encryption: Protects stored data if devices are physically compromised
- Zero-Knowledge Encryption: Service providers can’t access user data even with court orders
Virtual Private Networks (VPNS)
The document mentions VPNS but doesn’t fully explore their capabilities and limitations:
- Traffic Encryption: VPNS encrypt internet traffic between your device and the VPN server
- IP Masking: Hides your actual IP address and location
- Trust Issues: VPN providers themselves can potentially log user activity
- Jurisdiction Concerns: VPN providers in certain countries may be required to share data with authorities
Browser Privacy Settings and Extensions
The document briefly mentions browser settings but doesn’t detail specific tools:
- Privacy-Focused Browsers: Browsers like Firefox, Brave, and Tor prioritise privacy
- Content Blockers: Extensions that block trackers, ads, and fingerprinting attempts
- Global Privacy Control (GPC): Mentioned in the document, this emerging standard allows users to signal privacy preferences to websites
- HTTPS Everywhere: Forces encrypted connections when available
- Cookie Management: Tools to automatically delete cookies or isolate them from tracking
Personal Information Monitoring
Credit Monitoring
The document recommends checking credit reports regularly:
- Provides early detection of identity theft
- Allows for timely credit freezes in case of compromise
- Some services offer real-time alerts for new accounts or inquiries
Data Broker Removal
The document mentions data brokers but doesn’t detail how to address them:
- Many data brokers offer opt-out processes (though often deliberately complex)
- Privacy services can automate removal requests across multiple brokers
- Periodic checks are necessary as information can be re-collected
Digital Footprint Assessment
- Regular searches for your personal information online
- Setting up alerts for when your name or email appears in new contexts
- Auditing social media privacy settings and historical posts
Emerging Privacy Methods Not Mentioned
Privacy-Preserving Computation
- Homomorphic encryption allowing computation on encrypted data
- Secure multi-party computation for collaborative analysis without revealing inputs
- These technologies enable data use without privacy compromises
Decentralized Identity
- Self-sovereign identity systems giving users control over credentials
- Blockchain-based verification without centralized identity providers
- Reduces unnecessary disclosure of personal information
Differential Privacy
- Mathematical framework for sharing aggregate information without revealing individual data
- Used by major tech companies and census bureaus
- Allows for beneficial data analysis while protecting individual privacy
Holistic Privacy Strategy
Effective online privacy requires combining multiple methods:
- Prevention: Using tools like VPNs, privacy browsers, and strong authentication
- Monitoring: Regular checks of financial accounts, data breach notifications
- Mitigation: Plans for responding to privacy breaches when they occur
- Advocacy: Supporting privacy-enhancing legislation and corporate policies
The most effective approach recognizes that perfect privacy is unattainable in our connected world, but meaningful improvements are possible through layered protection strategies and informed digital choices.
Authentication Methods: A Comprehensive Analysis
Authentication serves as the frontline defense in digital security, verifying that users are who they claim to be. Let’s explore the major authentication methods, their strengths, weaknesses, and emerging trends.
Knowledge-Based Authentication (KBA)
Passwords
Passwords remain the most common authentication method despite well-documented limitations:
- Strengths: Familiar to users, easy to implement, and zero additional hardware requirements
- Weaknesses: Vulnerable to brute force attacks, credential stuffing, phishing, and poor user practices (reuse, simple patterns)
- Security improvements: Password managers, complexity requirements, and breach detection services
- User experience trade-offs: More secure passwords are typically more complex to remember
Security Questions
Often used as a secondary authentication or account recovery method:
- Strengths: Easy to implement and understand
- Weaknesses: Answers may be publicly available through social media or data breaches
- Evolution: Moving from factual questions (“mother’s maiden name”) to opinion-based questions (“favorite teacher”) that are harder to research
Possession-Based Authentication
SMS/Email One-Time Passwords (OTPs)
Temporary codes sent to a registered device or email:
- Strengths: Adds a second verification layer, familiar to users
- Weaknesses: Vulnerable to SIM swapping attacks, SMS interception, and email account compromises
- Use cases: Widely used for multi-factor authentication in banking and critical services
Hardware Tokens
Physical devices that generate authentication codes:
- Types: Time-based (TOTP), challenge-response, and cryptographic USB keys (FIDO2/WebAuthn)
- Strengths: Resistant to remote attacks, phishing-resistant (especially FIDO2)
- Weaknesses: Can be lost, damaged, or stolen; additional cost; user friction
- Notable implementations: YubiKey, Google Titan Security Key

Mobile Authentication Apps
Smartphone applications that generate verification codes:
- Strengths: More secure than SMS, convenient for users with smartphones
- Weaknesses: Device theft, malware on phones, backup/recovery challenges
- Popular options: Google Authenticator, Microsoft Authenticator, Authy
Biometric Authentication
Fingerprint Recognition
- Strengths: Convenient, difficult to forge, widely available on smartphones
- Weaknesses: Cannot be changed if compromised, accuracy affected by injuries or ageing
- Security considerations: Typically stores a mathematical model rather than an actual fingerprint image
Facial Recognition
- Strengths: Contactless, increasingly accurate with AI advancements
- Weaknesses: Affected by lighting, aging, masks; potential for presentation attacks (photos)
- Advanced implementations: Depth mapping, liveness detection, infrared scanning (e.g., Apple Face ID)
Iris/Retinal Scanning
- Strengths: Highly unique and stable throughout life
- Weaknesses: Specialised hardware requirements, user discomfort
- Use cases: High-security environments, border control
Voice Recognition
- Strengths: Natural, can work over phone calls
- Weaknesses: Affected by background noise, health conditions, ageing
- Security features: Liveness detection to prevent replay attacks
Behavioral Biometrics
Typing Patterns
- Implementation: Analyzes keystroke dynamics (speed, rhythm, pressure)
- Advantage: Continuous authentication without user action
Mouse/Touch Movement Analysis
- Implementation: Tracks unique patterns in how users navigate interfaces
- Use cases: Typically used as a secondary signal in risk-based authentication
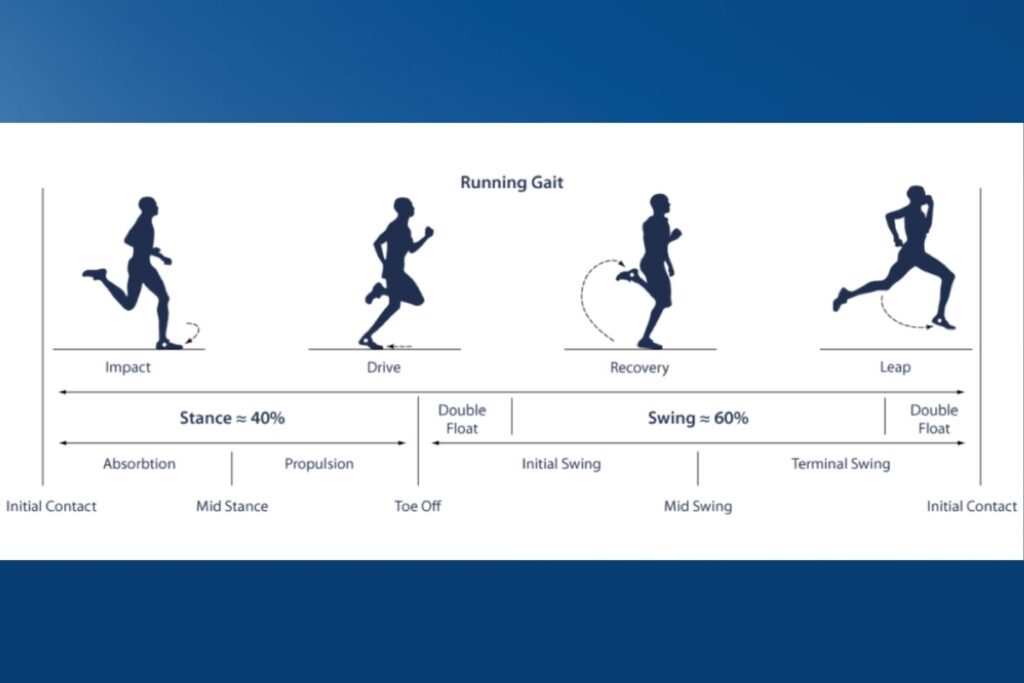
Gait Analysis
- Implementation: Identifies users by their walking pattern using smartphone sensors
- Applications: Emerging area for continuous authentication on mobile devices
Contextual and Adaptive Authentication
Location-Based Authentication
- Implementation: Verifies that access attempts come from expected locations
- Challenges: Privacy concerns, legitimate travel scenarios
- Refinements: Geofencing, velocity checks (impossible travel detection)
Device Recognition
- Implementation: Identifies trusted devices through fingerprinting
- Factors considered: Browser configuration, installed fonts, hardware identifiers
- Privacy balance: Need to identify devices without excessive tracking
Risk-Based Authentication
- Implementation: Dynamically adjusts authentication requirements based on risk factors
- Factors assessed: Location anomalies, device changes, behaviour patterns, time of access
- User experience: More friction for suspicious logins, less for routine access
Passwordless Authentication
Magic Links/Email Authentication
- Implementation: One-click login links sent to verified email addresses
- Strengths: Eliminates password management, reduces phishing vulnerability
- Weaknesses: Email account security becomes the single point of failure

WebAuthn/FIDO2 Standards
- Implementation: Uses public key cryptography with biometric or PIN verification
- Strengths: Phishing-resistant, protects against credential database breaches
- Adoption challenges: Implementation complexity, user education
Multi-Factor Authentication (MFA)
Factor Categories
- Something you know: Password, PIN, pattern
- Something you have: Phone, security key, smart card
- Something you are: Biometric characteristics
- Somewhere you are: Geolocation
- Something you do: Behavioural patterns
Implementation Approaches
- Required MFA: Mandates multiple factors for all logins
- Adaptive MFA: Triggers additional factors based on risk assessment
- Progressive MFA: Increases authentication requirements with sensitivity of resources accessed
Authentication Vulnerabilities and Mitigation

Man-in-the-Middle Attacks
- Vulnerability: Interception of authentication credentials
- Mitigation: TLS/SSL encryption, certificate validation
Replay Attacks
- Vulnerability: Capture and reuse of authentication traffic
- Mitigation: One-time codes, timestamps, nonces (numbers used once)
Social Engineering
- Vulnerability: Manipulation of users to reveal credentials
- Mitigation: Security awareness training, phishing-resistant authentication methods
Account Recovery Vulnerabilities
- Vulnerability: Weak recovery processes can bypass strong authentication
- Mitigation: Equally strong authentication for account recovery, multiple verification points
Future Trends in Authentication
Continuous Authentication
- Concept: Ongoing verification throughout a session rather than point-in-time
- Implementation: Combines behavioral biometrics with contextual signals
- Advantage: Can detect account takeovers during active sessions
Decentralized Identity
- Concept: User-controlled digital identities verified through blockchain or similar technology
- Potential: Reduces reliance on central identity providers, enhances privacy
- Standards development: Decentralized Identifiers (DIDs), Verifiable Credentials

Zero-Knowledge Proofs
- Concept: Proving identity without revealing underlying credentials
- Privacy benefit: Minimizes data exposure during authentication
- Applications: Age verification without revealing birthdate, credit worthiness without financial details
Quantum-Resistant Authentication
- Challenge: Quantum computing threatens current cryptographic methods
- Development: Post-quantum cryptographic algorithms for authentication
- Timeline: Proactive implementation before quantum threats materialise
Implementation Best Practices
Balancing Security and Usability
- Higher security typically increases friction
- Authentication fatigue leads to workarounds
- Contextual authentication can optimise this balance
Inclusive Design Considerations
- Accessibility requirements for biometric methods
- Alternative authentication paths for users with disabilities
- Cultural and demographic factors in authentication choice
Enterprise vs. Consumer Approaches
- Enterprise: Standardized, policy-driven, integration with identity management
- Consumer: Emphasis on convenience, adoption incentives, recovery options

The optimal authentication strategy typically involves layering multiple methods based on risk assessment, user needs, and the sensitivity of resources. As technology evolves, the trend is shifting toward stronger authentication that requires less active user participation, utilising passive and contextual signals.
Maxthon
Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—whether it involves sharing passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to protecting its users. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, knowing that their information is continuously safeguarded against emerging threats in cyberspace.
