Analysis of Bank Account Hacking Prevention in the Singapore Banking Context
Understanding Bank Account Hacking Prevention
Based on the document provided, bank account hacking prevention encompasses multiple layers of security measures implemented by both individuals and financial institutions. While the original document covers general prevention approaches, applying these to Singapore’s banking context requires understanding the unique regulatory environment supervised by the Monetary Authority of Singapore (MAS).
Core Prevention Strategies
- Authentication Security:
- Strong password implementation using complex combinations of characters
- Two-factor authentication (2fa), which is now mandatory for digital banking in Singapore
- Biometric verification is becoming increasingly standard in Singaporean mobile banking apps
- Account Monitoring:
- Regular review of transaction history
- Automated alert systems for unusual activities, which Singapore banks have widely implemented
- Real-time notification systems for transactions
- Safe Digital Practices:
- Secure browsing habits and avoid suspicious links
- Using official banking applications only
- Avoiding public Wi-Fi for banking transactions
- Regular software updates
- Personal Information Protection:
- Safeguarding sensitive data like NRIC numbers and account details
- Being vigilant against social engineering attempts
- Proper document disposal practices
Impact on Singapore Banks
Regulatory Compliance and Costs
Singapore banks face significant compliance requirements under MAS regulations, including:
- Technology Risk Management Guidelines:
- Singapore banks must adhere to MAS’s Technology Risk Management Guidelines
- Implementation costs for robust cybersecurity systems are substantial
- Regular security assessments and audits are mandatory
- Digital Banking Security Infrastructure:
- Significant investment in security technology and personnel
- Development of proprietary security solutions
- Integration of AI and machine learning for fraud detection
- Customer Service Implications:
- Increased resources devoted to security-related customer support
- Need for balance between security measures and user experience
- Educational initiatives to inform customers about security best practices
Reputational Considerations
- Trust as a Competitive Factor:
- Security reputation directly impacts customer acquisition and retention
- Public perception of a bank’s security measures influences market position
- Recovery from security incidents can be particularly challenging in Singapore’s reputation-sensitive market
- Cross-Border Banking Implications:
- Singapore’s position as a financial hub means security breaches can have international ripple effects
- Foreign banks operating in Singapore must meet or exceed local security standards
- Security reputation affects correspondent banking relationships
Role of MAS in Bank Account Hacking Prevention
Regulatory Framework
- MAS Notice 655 on Cyber Hygiene:
- Establishes minimum standards for cybersecurity
- Requires implementation of specific security controls
- Mandates regular security testing and assessment
- MAS Technology Risk Management Guidelines:
- Comprehensive framework for identifying and mitigating technology risks
- Detailed requirements for access control, system security, and data protection
- Guidelines for incident response and recovery
- Payment Services Act:
- Regulations specific to digital payment services
- Requirements for the security of payment transactions
- Customer protection provisions
MAS Initiatives and Response
- Collaborative Defence:
- Establishment of the Financial Sector Security Operations Centre (FS-SOC)
- Industry-wide threat intelligence sharing
- Regular cybersecurity exercises involving financial institutions
- Public Education:
- MAS-supported campaigns to educate consumers about digital banking safety
- Collaboration with banks on customer awareness programs
- Resources for identifying and reporting scams
- Incident Response Framework:
- Clear guidelines for banks on breach reporting
- Coordinated response protocols for system-wide threats
- Post-incident review requirements
Future Developments in Singapore Banking Security
- Technological Advancements:
- Increased adoption of AI for anomaly detection
- Expansion of biometric authentication methods
- Blockchain applications for transaction security and verification
- Regulatory Evolution:
- Continuous updates to MAS guidelines reflecting emerging threats
- Potential expansion of mandatory security measures
- Enhanced requirements for third-party service providers and partners
- Consumer Protection Enhancements:
- Development of improved fraud reimbursement frameworks
- Standardization of security protocols across institutions
- Greater emphasis on customer education as a preventive measure
Conclusion
Bank account hacking prevention in Singapore operates within a highly regulated environment where MAS plays a central role in establishing and enforcing security standards. Singapore banks face significant pressure to maintain robust security measures while balancing user experience and operational efficiency. The impact of these measures extends beyond direct costs to include reputational considerations and competitive positioning in Singapore’s sophisticated financial marketplace.
As digital banking continues to evolve, the collaboration between MAS and financial institutions will remain critical in addressing emerging threats and maintaining Singapore’s reputation as a secure financial hub.
Detailed Analysis of Bank Account Hacking Prevention and the Role of Anti-Scam Centres
Comprehensive Prevention Strategies Against Bank Account Hacking
Strong Authentication Protocols
Password Security
- Creation of Robust Passwords
- Implement passwords with a minimum of 12-16 characters
- Combine uppercase letters, lowercase letters, numbers, and special characters.
- Avoid sequential numbers, dictionary words, or personal information
- Create unique passwords for each financial account
- Password Management
- Utilize reputable password managers to generate and store complex passwords.s
- Change financial passwords quarterly
- Never reuse passwords across multiple financial platforms
- Avoid storing passwords in plain text or unsecured notes
Multi-Factor Authentication
- Implementation Across All Services
- Enable 2fa/MFA on all banking platforms and related financial services
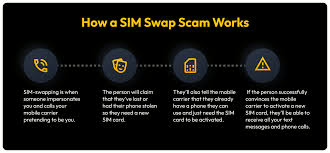
- Utilise app-based authenticators rather than SMS, where possible (more secure against SIM swapping)
- Register multiple authentication methods as backups
- Regularly verify registered contact information for authentication
- Biometric Authentication
- Enable fingerprint or facial recognition on banking apps
- Use biometrics in combination with another factor for higher security
- Ensure biometric templates are securely stored and encrypted
- Regularly update biometric data when prompted
Device and Network Security
- Device Protection
- Install reputable antivirus and anti-malware software with real-time scanning.
- Keep operating systems and applications updated with security patches
- Enable automatic updates for critical security software
- Use secure boot and disk encryption on devices used for banking
- Secure Connection Practices
- Avoid conducting banking activities on public or unsecured Wi-Fi networks
- Use a VPN with banking-grade encryption when accessing accounts outside home networks
- Verify HTTPS connections (padlock icon) before entering banking credentials
- Consider using a dedicated device exclusively for banking transactions
- Mobile Device Security
- Use only official banking applications downloaded from authorized app stores.
- Review app permissions carefully before granting access
- Enable remote wiping capabilities for lost or stolen devices
- Disable automatic connection to public Wi-Fi networks
- Install banking apps on personal devices only, not on shared or public devices
Transaction Monitoring and Alerts
- Account Surveillance
- Review account statements weekly or more frequently
- Set up real-time transaction notifications for all account activities
- Establish low-threshold alerts for unusual transactions
- Monitor credit reports quarterly for unauthorized accounts or inquiries
- Transaction Verification
- Enable confirmation requirements for new payees or large transactions
- Verify transaction details through a secondary channel
- Implement cooling-off periods for large transfers or new recipients
- Use transaction signing for confirmation of payment details
Social Engineering Defence
- Phishing Awareness
- Verify sender emails carefully, checking for subtle misspellings
- Never click links in unexpected financial emails or messages
- Access banking websites directly through bookmarks or by typing the URL
- Contact banks through official numbers when in doubt about communications
- Be suspicious of urgent requests or threats in communications
- Information Sharing Practices
- Never share OTPS, PINS, or passwords with anyone, including bank staff
- Limit the personal information shared on social media that could be used in social engineering
- Shred financial documents before disposal
- Use privacy settings on all social accounts to limit information exposure
- Call Verification
- Hang up and call back using official numbers for any calls claiming to be from banks.
- Never provide authentication information to incoming callers
- Be wary of callers creating urgency or fear to prompt immediate action
- Use dedicated fraud hotlines provided by banks to verify suspicious calls
Advanced Security Measures
- Account Segregation
- Maintain separate accounts for daily transactions and savings
- Consider using different banks for significant savings and routine transactions
- Use virtual cards for online purchases
- Set up transaction limits on accounts used for routine expenses
- Banking Platform Security
- Register for electronic statements to reduce mail fraud risk
- Set maximum daily transaction limits
- Enable location-based transaction verification where available
- Regularly update contact information for security notifications
- Digital Footprint Management
- Regularly review and delete stored payment information from websites
- Use privacy-focused search engines and browsers for financial research
- Clear cookies and browsing history after banking sessions
- Consider using ad blockers to prevent malvertising attacks
The Role of Anti-Scam Centres in Prevention and Response
Preventive Functions
- Public Education and Awareness
- Conduct targeted awareness campaigns about emerging scam techniques
- Provide educational resources on recognizing social engineering attempts
- Offer simulation training for identifying phishing and vishing attempts
- Maintain updated repositories of known scam patterns and methodologies
- Real-time Intelligence
- Monitor scam trends and provide early warning to financial institutions
- Issue timely alerts about new scam methodologies
- Maintain databases of known scam phone numbers, websites, and accounts
- Coordinate intelligence sharing between banks, telcos, and law enforcement
- Proactive Intervention
- Work with telecommunications companies to block known scam numbers
- Collaborate with internet service providers to take down phishing websites
- Support banks in implementing enhanced verification for suspicious transactions
- Help identify vulnerable demographic groups for targeted education
Response Capabilities
- Immediate Intervention
- Provide 24/7 hotlines for scam reporting and immediate response
- Coordinate with banks for rapid account freezing when fraud is detected
- Assist victims in documenting incidents properly for investigation
- Facilitate communication between multiple financial institutions when needed
- Fund Recovery Efforts
- Trace fund transfers to identify recipient accounts
- Coordinate with banks to freeze fraudulent accounts quickly
- Facilitate cross-border cooperation for international transfers
- Provide guidance on legal recourse options
- Post-Incident Support
- Offer counselling services for victims experiencing financial trauma
- Provide step-by-step guidance for account recovery and security restoration
- Assist with credit bureau notifications and fraud alerts
- Maintain communication throughoutthe investigation and recovery processes
Technological Capabilities
- Analytical Tools
- Deploy AI systems to identify unusual transaction patterns
- Use data analytics to connect seemingly unrelated scam reports
- Maintain behavioural analysis capabilities to identify evolving fraud techniques
- Employ network analysis to map scam operations and relationships
- Coordination Platforms
- Provide secure channels for information sharing between stakeholders
- Maintain centralised databases of scam reports accessible to relevant parties
- Offer digital platforms for case management and tracking
- Support standardised reporting protocols across financial institutions
Singapore’s Anti-Scam Centre: A Model Example
- Rapid Response Protocol
- Singapore’s ASC has streamlined processes, allowing for fund freezing within hour.s
- Maintains direct lines with major banks and payment platforms
- Employspecialiseded teams for different scam categories (investment, romance, job)
- Reports demonstrate success in recovering significant portions of scammed funds
- Public-Private Partnership
- Collaborates closely with telecom companies to block scam calls and messages
- Works with social media platforms to remove fraudulent advertisements
- Partners with banks on joint education initiatives
- Engages community organizations to reach vulnerable populations
- Legal Framework Support
- Provides evidence collection for the prosecution of scammers
- Supports the development of anti-scam legislation
- Works with international counterparts on cross-border cases
- Assists in standardizing scam reporting and response protocols
Integration of Prevention Strategies and Anti-Scam Centre Support
Creating a Comprehensive Defence System
- Layered Protection Approach
- Individual preventive measures form the first line of defence
- Banking security systems provide the second layer
- Anti-Scam Centres act as the third layer for prevention and rapid response
- Regulatory frameworks establish minimum security standards across all layers
- Continuous Improvement Cycle
- Anti-Scam Centres analyze successful attacks to identify prevention gaps
- Findings inform updates to individual and institutional security recommendations
- Regular drills and simulations test the effectiveness of prevention measures
- Feedback loops ensure lessons from each incident improve overall security
- Balancing Security and Accessibility
- Implement enhanced security without creating excessive friction
- Develop simplified reporting procedures for suspected fraud
- Ensure security measures accommodate users with varying technical abilities
- Provide alternative verification methods for users with accessibility needs
Conclusion
Effective bank account hacking prevention requires a comprehensive approach combining individual security practices, institutional safeguards, and the specialized capabilities of Anti-Scam Centres. The most successful prevention frameworks integrate these elements into a cohesive system that adapts continuously to evolving threats.
In particular, Anti-Scam Centres provide critical support through education, rapid response, and coordination capabilities that extend beyond what individuals or single institutions can achieve alone. Their ability to analyze patterns across multiple incidents enables more effective prevention strategies and faster recovery when breaches occur.
As digital banking continues to evolve, the partnership between individuals, financial institutions, and Anti-Scam Centres will remain essential to maintaining secure financial ecosystems in an increasingly sophisticated threat landscape.
The Role of Anti-Scam Centres in Combating Bank Account Hacking
Overview of Anti-Scam Centres
Anti-scam centres are specialized units dedicated to preventing, detecting, and responding to various forms of financial fraud, including bank account hacking. These centres operate at the intersection of law enforcement, financial institutions, telecommunications companies, and cybersecurity experts, creating a coordinated response system that addresses the complex nature of modern banking scams.
Key Functions in Bank Hacking Prevention and Response
Early Detection and Warning Systems
Anti-Scam Centres employ sophisticated monitoring systems to detect potential bank account hacking attempts before they succeed:
- Pattern Recognition
- Track emerging hacking techniques across multiple institutions
- Identify common indicators of compromise before they become widespread
- Monitor dark web forums for leaked credentials or new attack methodologies
- Real-Time Alert Networks
- Issue immediate alerts to financial institutions about new threats
- Warn the public about emerging scams through various communication channels
- Provide timely intelligence to banks for the prevention of similar attacks
- Vulnerability Assessment
- Analyze successful hacking incidents to identify security gaps
- Test banking platforms for potential vulnerabilities
- Recommend specific security enhancements based on threat intelligence
Rapid Response Capabilities
When bank account hacking is detected, Anti-Scam Centres activate rapid response protocols:
- Fund Freezing and Recovery
- Coordinate with banks to freeze compromised accounts immediately
- Work with receiving banks to halt fraudulent transfers
- Trace and recover funds transferred to mule accounts
- Singapore’s Anti-Scam Centre has demonstrated success in recovering funds by acting within the critical first few hours
- Evidence Preservation
- Secure digital evidence before it can be destroyed
- Document transaction trails for legal proceedings
- Preserve communication records related to social engineering aspects
- Cross-institutional Coordination
- Facilitate communication between multiple banks involved in fund transfers
- Coordinate with telecommunications companies to block related phone numbers
- Engage internet service providers to take down phishing websites and infrastructure
Victim Support Services
Anti-Scam Centres provide crucial support to victims of bank hacking:
- Immediate Guidance
- Operate 24/7 hotlines for immediate reporting and assistance
- Provide step-by-step instructions to secure remaining assets
- Guide victims through the immediate documentation process
- Case Management
- Assign dedicated case officers to complex hacking incidents
- Track investigation progress and keep victims informed
- Coordinate with multiple agencies on behalf of victims
- Recovery Assistance
- Help victims navigate bank claim procedures
- Provide documentation for insurance claims
- Offer guidance on identity theft remediation if personal information was compromised.
Public Education and Awareness
Anti-Scam Centres play a pivotal role in preventing future incidents through education:
- Targeted Information Campaigns
- Develop educational materials about specific hacking techniques
- Create customized awareness programs for vulnerable demographics
- Produce easily shareable content about emerging threats
- Bank Security Practices Education
- Conduct workshops on secure digital banking practices
- Demonstrate how to verify legitimate bank communications
- Provide practical guides for securing accounts with available bank features
- Red Flag Recognition Training
- Train the public to identify warning signs of phishing attempts
- Educate users about social engineering tactics used in vishing (voice phishing)
- Create simulation tools to test and improve the recognition of scam attempts
Singapore’s Anti-Scam Centre: A Case Study in Excellence
Singapore’s Anti-Scam Centre (ASC) has emerged as a particularly compelling model in combating bank account hacking:
- Institutional Structure
- Established under the Singapore Police Force in 2019
- Works in close partnership with major financial institutions
- Maintains direct channels with telecommunication companies and internet service providers
- Operational Efficiency
- Streamlined processes allow for fund freezing within hours, not days
- Integrated systems connect directly with bank fraud departments
- Employs specialized teams for different types of scams, including those targeting bank accounts
- Success Metrics
- Has successfully recovered significant portions of scammed funds
- Reduced response time between scam reporting and account freezing
- Improved public awareness of standard bank hacking methods
Technological Tools Employed by Anti-Scam Centres
Modern Anti-Scam Centres leverage advanced technology to combat bank hacking:
- Artificial Intelligence and Machine Learning
- Algorithmic detection of unusual transaction patterns
- Natural language processing to identify phishing content
- Predictive modelling to anticipate new attack vectors
- Centralized Database Systems
- Repositories of known scam methodologies and perpetrators
- Shared intelligence on compromised credentials
- Cross-referencing capabilities to connect seemingly unrelated incidents
- Digital Forensics Capabilities
- Advanced tools for tracing cryptocurrency transfers
- IP tracking and geolocation services
- Device fingerprinting technologies
How Individuals Can Effectively Engage with Anti-Scam Centres
To maximise the benefits offered by Anti-Scam Centres in bank hacking situations:
- Before an Incident
- Save the Anti-Scam Centre’s contact information in advance
- Familiarise yourself with reporting procedures
- Participate in education programs offered by the centre
- During a Suspected Hack
- Contact the Anti-Scam Centre immediately, alongside your bank
- Provide comprehensive information about the incident
- Follow guidance precisely regarding account security steps
- After Reporting
- Maintain regular communication with assigned case officers
- Document all subsequent suspicious activities
- Participate in feedback processes to improve services
Challenges and Future Directions
Anti-Scam Centres face several challenges in addressing bank account hacking:
- Cross-Border Jurisdiction Issues
- Many hacking operations cross international boundaries
- Varying legal frameworks complicate fund recovery
- Coordination with international counterparts requires diplomatic efforts
- Technological Arms Race
- Hackers continually evolve their techniques
- New payment methods create novel vulnerabilities
- Increasing sophistication of social engineering attacks
- Future Development Areas
- Enhanced integration with bank security systems for real-time prevention
- Development of predictive capabilities to anticipate emerging threats
- Greater harmonization of international response protocols
- Expanded use of AI for both detection and prevention
Conclusion
Anti-scam centres represent a critical component in the fight against bank account hacking, offering specialized expertise and coordinated response capabilities that individual institutions cannot achieve alone. Their multifaceted approach—combining technological tools, rapid response protocols, victim support, and public education—creates a comprehensive defence system against increasingly sophisticated attacks.
For individuals, understanding how to effectively engage with these centres can significantly improve outcomes when facing potential bank account compromise. The continued evolution of Anti-Scam Centres, particularly their technological capabilities and international cooperation frameworks, will be essential in maintaining adequate protection against the ever-changing landscape of bank account hacking threats.
As digital banking continues to expand, the role of Anti-Scam Centres will likely become even more central to maintaining public confidence in financial systems and ensuring that technological advancements in banking remain accessible without exposing users to undue risk.
Comprehensive Guide to Bank Account Hacking Prevention
Introduction
The digital transformation of banking has created unprecedented convenience but also new security challenges. Bank account hacking has evolved from simple password theft to sophisticated multi-vector attacks employing social engineering, malware, and exploiting system vulnerabilities. This guide explores the most effective preventive measures at the individual, technological, and institutional levels.
Individual Security Measures
Authentication Best Practices
Password Security
- Complex Passphrase Implementation: Create passwords with 16+ characters combining random words with numbers and symbols (e.g., “Umbrella7$RainbowTractor!9”)
- Password Rotation Protocol: Change financial passwords quarterly without patterns
- Unique Password Policy: Use different passwords for each financial service
- Password Manager Adoption: Employ reputable password managers with encryption
Multi-Factor Authentication (MFA)
- Universal Implementation: Enable MFA on all financial accounts and related services
- Authenticator App Preference: Use authenticator apps instead of SMS-based verification
- Hardware Security Keys: Consider YubiKeys or similar FIDO-compliant devices for critical accounts
- Biometric Authentication: Enable fingerprint/facial recognition, but understand their limitations
Digital Hygiene Practices
Device Security
- Dedicated Device Usage: Consider using a separate device exclusively for banking
- Operating System Integrity: Keep systems updated with automatic security patches
- Anti-Malware Protection: Install reputable security software with real-time scanning
- Browser Security: Use browsers with robust security features and minimal extensions
- Regular Security Scans: Schedule weekly complete system scans
Network Security
- Secure Connection Requirements: Never conduct banking on public Wi-Fi networks
- VPN Usage: Employ banking-grade encrypted VPN services when necessary
- Home Router Security: Change default credentials and keep firmware updated
- Network Monitoring: Install intrusion detection systems for home networks
- Connection Verification: Check for HTTPS and valid certificates before proceeding
Behavioural Security Practices
Awareness and Education
- Social Engineering Recognition: Learn to identify manipulation tactics
- Phishing Awareness Training: Regularly test your ability to spot fraudulent communications
- Security News Monitoring: Stay informed about the latest banking threats
- Regular Security Audits: Conduct personal security reviews quarterly
Transaction Habits
- Regular Account Monitoring: Review accounts daily for unauthorized transactions
- Transaction Verification: Confirm details through secondary channels for large transfers
- Low Transfer Limits: Set default daily transaction limits
- Payee Verification Period: Implement a personal waiting period before transferring to new recipients
Technological Security Measures
Advanced Authentication Technologies
Adaptive Authentication
- Behavioural Biometrics: Systems that analyze typing patterns, mouse movements
- Contextual Authentication: Verification based on location, device, and behaviour patterns
- Continuous Authentication: Ongoing session monitoring rather than a one-time login
- Risk-Based Authentication: Varying security requirements based on transaction risk assessment
Encryption and Communication Security
- End-to-End Encryption: Ensure all banking communications use strong encryption
- Secure Socket Layer Verification: Confirm SSL/TLS protocol usage (HTTPS)
- Certificate Validation: Verify digital certificates of banking websites
- Encrypted Storage: Use encrypted containers for financial documents
Account Monitoring and Controls
Transaction Monitoring
- Real-Time Alerts: Set up notifications for all account activities
- Threshold Alerts: Create custom alerts for transactions exceeding specific amounts
- Location-Based Alerts: Receive notifications for transactions from unusual locations
- New Device Notifications: Get alerts when accounts are accessed from new devices
Account Controls
- Account Segregation: Maintain separate accounts for different purposes (daily transactions vs. savings)
- View-Only Access: Use read-only access for routine balance checking
- Whitelisted Payees: Restrict transfers to pre-approved recipients
- Geographic Restrictions: Limit account access to specific countries
Specialized Security Tools
Privacy Protection
- Virtual Card Services: Use one-time or merchant-specific card numbers
- Privacy-Focused Browsers: Use browsers with tracking protection for financial activities
- Data Minimisation Tools: Limit personal information exposure online
- Digital Footprint Management: Regularly remove banking information from devices
Anti-Fraud Tools
- Credit Freezes/Locks: Implement security freezes at credit bureaus
- Account Activity Monitoring Services: Subscribe to services that track financial activity
- Dark Web Monitoring: Use services that alert if your information appears on dark web marketplaces
- Fraud Alert Systems: Place fraud alerts on credit files
Institutional Security Measures
Bank-Provided Security Features
Enhanced Verification Systems
- Out-of-Band Authentication: Verification through separate communication channels
- Transaction Signing: Cryptographic verification of transaction details
- Dedicated Security Devices: Hardware tokens provided by financial institutions
- Callback Verification: Bank confirmation calls for unusual transactions
Account Protection Services
- Account Lockdown Options: Ability to instantly freeze accounts via mobile app
- Limited Access Profiles: Restricted account access for specific purposes
- Temporary Access Controls: Time-limited access for specific functions
- Secure Communication Channels: Encrypted messaging systems within banking apps
Banking Policy Considerations
Service Selection Criteria
- Security Feature Evaluation: Assess banks based on available security measures
- Security History Assessment: Research the bank’s track record of handling security incidents
- Insurance and Liability Policies: Understand fraud coverage and customer protections
- Response Time Guarantees: Consider banks with rapid fraud response protocols
Account Structure Optimization
- Tiered Account System: Limited funds in accessible accounts, bulk in high-security accounts
- Multiple Bank Strategy: Distribute assets across different financial institutions
- Account Purpose Separation: Dedicated accounts for specific activities (online shopping, bill payments)
- Limited Connection Architecture: Minimize automatic transfers between accounts
Response Preparedness
Incident Response Planning
Documentation Preparation
- Account Information Inventory: Maintain secure records of account numbers and contact information
- Transaction Records: Keep independent records of the foremost transactions
- Communication Logs: Document all communications with financial institutions
- Authentication Recovery Options: Secure backup of recovery codes and authentication methods
Contact Protocol Development
- Emergency Contact Hierarchy: Predetermined sequence of notifications
- Anti-Scam Centre Information: Ready access to relevant authorities’ contact details
- Legal Support Identification: Pre-identified legal resources for serious incidents
- Communication Templates: Prepared messages for rapid reporting
Recovery Systems
Backup Financial Access
- Emergency Fund Accessibility: Maintain funds outside the primary banking system
- Alternate Payment Methods: Have multiple payment options available
- Credit Availability: Maintain clean credit for emergency needs
- International Access Planning: Ensure financial access when travelling
Identity Protection
- Credit Monitoring Services: Subscribe to services that track credit file changes
- Identity Theft Insurance: Consider coverage for major breaches
- Document Recovery System: Plan for replacing compromised identification
- Digital Identity Management: Strategy for Addressing Compromised Online Credentials
Emerging Technologies and Future Considerations
Advanced Security Technologies
Blockchain and Distributed Ledger
- Blockchain Verification: Immutable transaction records
- Smart Contract Enforcement: Automated security rule enforcement
- Decentralized Identity Management: Self-sovereign identity solutions
- Cryptographic Advancements: Zero-knowledge proofs for privacy-preserving verification
Artificial Intelligence
- Behavioural Analysis: AI systems detecting unusual patterns
- Predictive Threat Detection: Anticipating attacks before execution
- Automated Response Systems: Immediate countermeasures to detected threats
- Continuous Learning Systems: Security that adapts to new attack vectors
Regulatory and Industry Developments
Security Standards Evolution
- Regulatory Requirements: Stay informed about changing compliance standards
- Industry Consortiums: Security initiatives across financial institutions
- International Coordination: Cross-border security frameworks
- Consumer Protection Legislation: Emerging laws affecting security responsibilities
Privacy and Security Balance
- Data Minimisation Principles: Reducing unnecessary data collection
- Privacy-Enhancing Technologies: Tools preserving privacy while maintaining security
- Consent Management: Granular control over information sharing
- Right to be Forgotten Implementation: Data deletion after service termination
Conclusion
Bank account hacking prevention requires a multi-layered approach combining individual vigilance, technological safeguards, and institutional protections. The most effective security strategies employ defence-in-depth principles, recognizing that no single measure provides complete protection. By implementing comprehensive security across all levels—from passwords and authentication to account structures and monitoring systems—individuals can significantly reduce their vulnerability to increasingly sophisticated attacks.
As banking continues its digital evolution, security measures must similarly advance. Staying informed about emerging threats and new protective technologies represents an ongoing responsibility for anyone seeking to maintain financial security in the digital age.
Maxthon
In an age where the digital world is in constant flux and our interactions online are ever-evolving, the importance of prioritising individuals as they navigate the expansive internet cannot be overstated. The myriad of elements that shape our online experiences calls for a thoughtful approach to selecting web browsers—one that places a premium on security and user privacy. Amidst the multitude of browsers vying for users’ loyalty, Maxthon emerges as a standout choice, providing a trustworthy solution to these pressing concerns, all without any cost to the user.

Maxthon, with its advanced features, boasts a comprehensive suite of built-in tools designed to enhance your online privacy. Among these tools are a highly effective ad blocker and a range of anti-tracking mechanisms, each meticulously crafted to fortify your digital sanctuary. This browser has carved out a niche for itself, particularly with its seamless compatibility with Windows 11, further solidifying its reputation in an increasingly competitive market.
In a crowded landscape of web browsers, Maxthon has forged a distinct identity through its unwavering dedication to offering a secure and private browsing experience. Fully aware of the myriad threats lurking in the vast expanse of cyberspace, Maxthon works tirelessly to safeguard your personal information. Utilising state-of-the-art encryption technology, it ensures that your sensitive data remains protected and confidential throughout your online adventures.
What truly sets Maxthon apart is its commitment to enhancing user privacy during every moment spent online. Each feature of this browser has been meticulously designed with the user’s privacy in mind. Its powerful ad-blocking capabilities work diligently to eliminate unwanted advertisements, while its comprehensive anti-tracking measures effectively reduce the presence of invasive scripts that could disrupt your browsing enjoyment. As a result, users can traverse the web with newfound confidence and safety.
Moreover, Maxthon’s incognito mode provides an extra layer of security, granting users enhanced anonymity while engaging in their online pursuits. This specialised mode not only conceals your browsing habits but also ensures that your digital footprint remains minimal, allowing for an unobtrusive and liberating internet experience. With Maxthon as your ally in the digital realm, you can explore the vastness of the internet with peace of mind, knowing that your privacy is being prioritised every step of the way.
