The Current Landscape of Password Security Threats
Primary Vulnerabilities
- Credential Stuffing: Hackers use login details stolen from one breach to attempt access across multiple platforms, exploiting password reuse.
- Social Engineering: Personal information shared on social media provides attackers with data to guess passwords or answer security questions.
- Brute Force Attacks: Automated systems attempt millions of password combinations, easily cracking short or simple passwords.
- Phishing Campaigns: Sophisticated fake websites and emails trick users into voluntarily providing their banking credentials.
- Data Breaches: Third-party services with weak security can expose your passwords, especially if they’re stored improperly.
Common Password Security Mistakes
- Password Reuse: Using identical passwords across multiple platforms creates a single point of failure.
- Personal Information in Passwords: Including birthdates, pet names, or other discoverable personal information weakens security.
- Short or Simple Passwords: Anything under 12 characters with predictable patterns is increasingly vulnerable.
- Infrequent Password Updates: Keeping the same password for years increases exposure risk.
- Insecure Storage: Saving passwords in plain text in notes apps, email drafts, or spreadsheets.
- Bypassing Multi-Factor Authentication: Relying solely on passwords without secondary verification.
Comprehensive Solutions
Immediate Actions
- Password Manager Implementation
- LastPass, 1Password, Bitwarden, or built-in options like Google Password Manager
- Benefits: Generates and stores unique complex passwords for each account
- Features to look for: Encryption, cross-platform support, breach monitoring
- Enable Two-Factor Authentication (2FA)
- SMS verification (basic protection)
- Authentication apps (Google Authenticator, Microsoft Authenticator)
- Hardware security keys (YubiKey, Google Titan)
- Biometric verification, where available
- Password Strength Enhancement
- Length: Minimum 12-16 characters
- Complexity: Mix of uppercase, lowercase, numbers, and special characters
- Passphrases: Several unrelated words strung together (easier to remember, harder to crack)
- Regular Security Audits
- Schedule quarterly password updates for critical accounts
- Use tools like Have I Been Pwned to check for compromised credentials
- Review saved passwords and delete unused accounts
Advanced Protection Strategies
- Consider Passkeys
- Next-generation authentication that eliminates passwords entirely
- Uses biometric verification and cryptographic keys
- Supported by major platforms like Google, Apple, and Microsoft
- Security Keys for Banking
- Physical USB/NFC hardware keys provide the strongest protection
- Cannot be phished as they verify the authentic website
- FIDO2/WebAuthn compliant devices offer cross-platform compatibility
- Dedicated Banking Device
- Consider having a separate device solely for financial transactions
- Reduces risk of malware or keyloggers capturing credentials
- Can be as simple as a separate browser profile or as thorough as a different device
- Network Security Enhancements
- Use VPNS when accessing banking on public networks
- Implement DNS-level protection like Pi-hole to block malicious domains
- Consider browser extensions that warn about phishing attempts (e.g., uBlock Origin)
- Email Security for Account Recovery
- Create a dedicated email address solely for financial accounts
- Enable strict security measures on this email
- Use plus addressing for account-specific emails (e.g., [email protected])
Organizational and Behavioral Changes
- Create a Password Updating Schedule
- Calendar reminders for rotating critical passwords
- Prioritise financial accounts for more frequent updates
- Use a password manager’s built-in password expiration features
- Develop Personal Security Protocols
- Never log into banking from links in emails or messages
- Verify caller identities before providing any information
- Check for HTTPS and valid certificates before entering credentials
- Emergency Access Planning
- Create secure methods for trusted family members to access accounts in emergencies.
- Document recovery procedures without exposing actual credentials
- Consider legal instruments like digital asset directives
- Continuous Education
- Stay informed about emerging threats and security practices
- Follow security experts and trusted sources
- Treat security as an ongoing process, not a one-time setup
Implementation Strategy
- Start with a Password Audit
- Identify your most critical accounts (banking, email, etc.)
- Check for password reuse and weak credentials
- Prioritize fixing the most vulnerable and important accounts first
- Gradual Migration to Password Manager
- Begin with financial and critical accounts
- Set up secure generation and storage
- Gradually update all accounts as you use them
- Layer in Additional Security
- Enable 2fa wherever available
- Add hardware keys for critical accounts
- Implement network protection measures
- Maintain Regular Security Habits
- Schedule quarterly security reviews
- Update passwords on a rotating schedule
- Stay alert to security news and breach notifications
By implementing these layered security measures, you can significantly reduce the risk of unauthorised access to your online banking and other critical accounts, protecting your financial well-being in an increasingly complex threat landscape.
At nearly every cybersecurity meeting, seminar, and discussion group, one question looms large: Is your password strong enough?
Research has revealed a troubling truth: many passwords fail to protect our digital lives. Think of passwords as the keys to your kingdom; they guard your identity, sensitive data, and personal information. A single phrase or word can grant access to everything you hold dear.

Once a fraudster identifies your username—often just your email address—their next target is your password. A quick scan of your social media accounts can provide them with vital clues. Your pet’s name, your mother’s maiden name, or even your favourite vacation spot may be public knowledge, and if any of these are tied to your passwords or security questions, you become an easy target.
Fraudsters are patient hunters, willing to invest time and effort if they believe the reward is worth it. The simpler your password, the quicker they can unlock the door to your virtual world. In an age where our lives are increasingly online, ensuring that your passwords are robust is no longer optional; it’s essential for safeguarding everything you cherish.
In 2019, a startling revelation emerged from CNN research: the five most common passwords were shockingly simplistic. They were as follows:
1. 123456
2. 123456789
3. Qwerty
4. Password
5. 111111
These passwords may seem harmless, but they are anything but secure. In fact, using any of these is like leaving your front door wide open, inviting trouble.
Creating strong passwords is essential to safeguarding not just your accounts but also the sensitive information of your friends and contacts. When it comes to cybersecurity, the responsibility extends beyond oneself; it encompasses the safety of those within your digital circle.

Fraudsters often exploit this vulnerability. Once they gain access to your contact list, they can unleash a barrage of phishing emails or malware-laden messages. Imagine the chaos that could ensue if one of your friends clicks on a link and unknowingly compromises their data.
So, how can you fortify your defences? A strong password is key, comprising a mix of uppercase and lowercase letters, numbers, and symbols. Remember, the longer and more complex your password, the harder it becomes for attackers to crack it. Prioritise security—your peace of mind and the safety of your contacts depend on it.
In today’s digital age, where our lives are intertwined with technology, safeguarding our online accounts has never been more crucial. Consumer Reports offers some valuable insights to help you fortify your digital presence.

First and foremost, consider crafting a longer, more intricate password. Instead of the standard combinations of letters and numbers, think about a memorable phrase that holds personal significance. For instance, something whimsical like “Mydogdigs4rubberbones!” not only adds complexity but also makes it easier for you to recall.
Next, resist the temptation to recycle passwords across different platforms. Using the same password for multiple accounts can create serious vulnerabilities; if one account is compromised, all others become at risk. A password manager app can be a lifesaver here, securely storing unique passwords for each of your accounts.
Implementing two-factor authentication (2fa) is another decisive step in securing your accounts. This method requires you to enter a code sent to your smartphone, adding an extra layer of protection that makes unauthorised access much more difficult.
Lastly, exercise caution regarding what you share on social media. Oversharing personal information can inadvertently provide clues to potential hackers. Limit your posts to a trusted circle, ensuring that your online presence remains safe and secure. By following these tips, you can navigate the digital landscape with greater confidence and peace of mind.
In an age where digital security is paramount, a new trend is emerging: the use of “passphrases” instead of traditional passwords. Imagine a phrase formed from a random assortment of four or more short words that only you can decipher. For instance, think of “piano-blueberry-sunshine-rocket.” While it may sound whimsical, it serves as a formidable barrier against cyber intruders.
The beauty of passphrases lies in their randomness. Unlike conventional passwords, which can often be guessed or cracked with relative ease, these word combinations are much more complex to predict. They don’t follow a logical sentence structure and are unique to each user, making them significantly more secure.
Consider this: protecting your personal information is just as crucial as locking your front door every night. By creating hurdles for potential fraudsters, you increase the chances they will seek easier targets elsewhere.
Knowledge and awareness act as powerful shields in the ongoing battle against cybercrime. To fortify your defences further, explore Regions’ Fraud Prevention Resources for practical tips and insights. Your digital safety is worth the effort—arm yourself with the right strategies today.
In an age where digital security is paramount, a new trend is emerging: the use of “passphrases” instead of traditional passwords. Imagine a phrase formed from a random assortment of four or more short words that only you can decipher. For instance, think of “piano-blueberry-sunshine-rocket.” While it may sound whimsical, it serves as a formidable barrier against cyber intruders.
The beauty of passphrases lies in their randomness. Unlike conventional passwords, which can often be guessed or cracked with relative ease, these word combinations are much more complex to predict. They don’t follow a logical sentence structure and are unique to each user, making them significantly more secure.

Consider this: protecting your personal information is just as crucial as locking your front door every night. By creating hurdles for potential fraudsters, you increase the chances they will seek easier targets elsewhere.
Authentication Alternatives: Beyond Traditional Passwords
As password vulnerabilities continue to pose security risks, the authentication landscape is evolving rapidly with alternatives that offer improved security and user experience. Here’s a comprehensive overview of the major authentication alternatives available today:
Biometric Authentication
Fingerprint Recognition
- How it works: Uses unique ridges and patterns in fingerprints
- Applications: Mobile banking apps, physical access to devices
- Advantages: Quick, convenient, difficult to replicate
- Limitations: Can be affected by cuts, dryness; specialized sensors required
Facial Recognition
- How it works: Maps facial features mathematically
- Applications: Mobile device unlock, banking apps, passport control
- Advantages: Contactless, fast verification
- Limitations: Can be affected by lighting, aging, or facial coverings
Iris/Retinal Scanning
- How it works: Maps unique patterns in the eye
- Applications: High-security facilities, some smartphones
- Advantages: Extremely unique and difficult to forge
- Limitations: Specialized hardware, can be intrusive
Voice Recognition
- How it works: Analyzes vocal patterns and speech characteristics
- Applications: Phone banking, voice assistants
- Advantages: Works remotely via standard hardware
- Limitations: Background noise interference, voice changes due to illness
Hardware-Based Solutions
Security Keys (FIDO/FIDO2)
- How it works: Physical USB, NFC, or Bluetooth devices that generate cryptographic signatures
- Examples: YubiKey, Google Titan, Thetis
- Advantages: Highly resistant to phishing, malware; no secrets transmitted
- Limitations: Physical device that can be lost; additional cost
Smart Cards
- How it works: Physical cards with embedded chips containing authentication credentials
- Applications: Corporate access, government ID, banking
- Advantages: Physical possession requirement; can include additional security features
- Limitations: Requires specialized readers; can be lost
Cryptographic Solutions
Passkeys
- How it works: Uses public-key cryptography to replace passwords entirely
- Applications: Increasingly adopted by Google, Apple, Microsoft, major websites
- Advantages: Phishing-resistant, simpler user experience, no shared secrets
- Limitations: Still being rolled out; platform-specific implementation details
Digital Certificates
- How it works: Uses public key infrastructure to verify identity
- Applications: Enterprise systems, secure email, device authentication
- Advantages: Strong cryptographic security, centrally manageable
- Limitations: Complex setup, certificate management overhead
Knowledge-Based Alternatives
Pattern Recognition
- How it works: User draws a pattern on a grid
- Applications: Mobile device unlock
- Advantages: Easier to remember than complex passwords
- Limitations: Observable, limited complexity
Cognitive Authentication
- How it works: Based on personal knowledge or experiences
- Examples: Personal questions, image recognition, behavior-based
- Advantages: Can be difficult for others to guess
- Limitations: Can sometimes be researched (especially public information)

Behavioral Biometrics
Keystroke Dynamics
- How it works: Analyzes typing rhythm, pressure, and pattern
- Applications: Continuous authentication while using systems
- Advantages: Passive authentication, difficult to replicate
- Limitations: Can vary based on user conditions (injury, fatigue)
Gait Analysis
- How it works: Measures unique walking patterns
- Applications: Mobile continuous authentication
- Advantages: Passive, difficult to mimic
- Limitations: Requires motion sensors, can change with injuries
Mouse/Touch Dynamics
- How it works: Analyzes how users interact with pointing devices or touchscreens
- Applications: Continuous authentication in desktop/mobile environments
- Advantages: Passive, constantly verifying identity
- Limitations: Requires substantial behavior data to establish patterns
Multi-Factor Integration
Adaptive Authentication
- How it works: Dynamically adjusts security requirements based on risk factors
- Applications: Banking, enterprise access
- Advantages: Balances security and convenience; applies stronger authentication only when needed
- Limitations: Complex to implement; requires sophisticated risk analysis
Single Sign-On (SSO)
- How it works: Authenticate once to access multiple services
- Applications: Enterprise environments, web services
- Advantages: Reduced authentication fatigue, centralized security control
- Limitations: Single point of failure risk
OAuth and OpenID Connect
- How it works: Delegates authentication to trusted providers
- Applications: “Login with Google/Apple/Facebook” systems
- Advantages: Leverages stronger security of major providers
- Limitations: Privacy concerns, dependency on third parties
Emerging Technologies
Zero-Knowledge Proofs
- How it works: Cryptographically proves identity without revealing actual credentials
- Applications: Cryptocurrency wallets, emerging identity systems
- Advantages: Privacy-preserving, mathematically secure
- Limitations: Computational complexity, early adoption phase
Blockchain-Based Identity
- How it works: Uses distributed ledgers to verify identity claims
- Applications: Self-sovereign identity systems, decentralized authentication
- Advantages: User control, tamper-resistant
- Limitations: Emerging technology, standardization challenges
Continuous Authentication
- How it works: Constantly verifies user identity through multiple passive factors
- Applications: High-security environments, financial services
- Advantages: Security beyond point-of-login, adapts to threat levels
- Limitations: Privacy considerations, battery/resource usage on mobile devices
Implementation Considerations
For Organizations
- Risk Assessment: Match authentication strength to the value of protected assets
- User Experience: Balance security with convenience
- Inclusivity: Ensure authentication methods work for all users including those with disabilities
- Backup Methods: Provide secure fallback options for when primary methods fail
- Standard Compliance: Align with industry standards like FIDO2, WebAuthn
For Individuals
- Ecosystem Integration: Choose solutions that work across your devices
- Privacy Implications: Understand how biometric data is stored and used
- Recovery Options: Ensure you can regain access if primary methods are unavailable
- Security Updates: Keep authentication systems and devices updated
- Layered Approach: Use multiple authentication methods for critical accounts
By implementing appropriate authentication alternatives based on your specific needs and risk profile, you can significantly enhance security while potentially improving the user experience beyond traditional password-based systems.
Authentication, whether conducted online or in person, plays a crucial role in safeguarding accounts and devices from unauthorised access. The landscape of authentication methods is continually evolving, providing stronger defences against fraud. This advancement comes at a time when fraudsters are also becoming increasingly sophisticated in their tactics.
Organisations tailor their authentication strategies based on various factors, including their risk tolerance, the types of transactions they facilitate, and the overall customer experience they aim to provide. The challenge lies in balancing security with user convenience, ensuring that legitimate users can access their accounts without undue hassle.
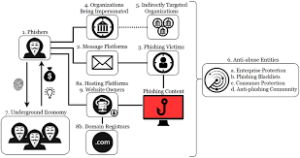
Organisations have three key opportunities centred around authentication to combat fraud effectively. First, addressing fraud at the point of account login is critical. Traditional static login credentials—like usernames and passwords—are often susceptible to theft and manipulation.
Many companies are adopting multi-factor authentication (MFA) to enhance security. This approach adds a layer of protection by requiring users to provide something they possess, such as a one-time passcode sent to their mobile device or a biometric identifier like a fingerprint.
These methods not only help fortify the initial login process but also serve as a deterrent against potential fraud attempts. As the battle between security measures and fraudulent activities continues, the importance of robust authentication cannot be overstated. It remains a vital component in protecting both organisations and their customers from the ever-evolving threats in the digital landscape.
Mitigating fraudulent transactions is a critical challenge faced by organisations today. Criminals have become increasingly adept at bypassing security measures to authenticate and access accounts without authorisation. In response, many organisations deploy sophisticated tools designed to monitor account navigation, track account activity, and analyse transactions for any signs of fraud.
When suspicious transactions are detected, the organisation often acts swiftly. They may implement additional layers of authentication to ensure the legitimacy of the activity. This could involve prompting the user to verify their identity through a different method, such as a one-time password sent to their registered mobile number or email.

In some cases, organisations may choose to contact the customer directly using previously established communication channels. This personal touch not only helps confirm the authenticity of the transaction but also reassures the customer that their security is a top priority.
The combination of proactive monitoring and responsive verification measures creates a robust defence against fraud. By staying vigilant and adapting to emerging threats, organisations can better protect their customers and maintain trust in their services.
In an era marked by rapid technological advancements, the intersection of technology and education has become increasingly significant, particularly in the realm of payment security. Innovations such as machine learning and artificial intelligence are transforming how we approach authentication, offering sophisticated methods to enhance user safety. One promising development is passwordless authentication, which leverages unique biometric indicators like typing patterns, swipe gestures, and even finger pressure to verify identity.

These cutting-edge technologies streamline the payment process and create a more secure environment for users. By analysing how people interact with their devices, organisations can develop systems that are more resistant to fraud and unauthorised access. The implications are profound; with each interaction, these systems learn and adapt, making them increasingly effective at recognising legitimate users while thwarting potential threats.
However, the technical prowess of these systems is only part of the equation. Education plays a vital role in empowering customers to understand the risks associated with authentication. Organisations have a responsibility to inform their clients about potential vulnerabilities and the importance of robust security measures. By guiding best practices and the various options available for mitigating risks, businesses can foster a culture of awareness and vigilance.
Ultimately, the synergy between technological innovation and customer education holds the key to a safer digital landscape. As we embrace these advancements, it is essential to ensure that users are equipped with the knowledge they need to navigate this evolving terrain securely. Together, we can build a future where payment security is not just an afterthought but a foundational principle of our digital interactions.
Maxthon
Maxthon stands at the forefront of transforming the realm of cloud gaming, introducing a groundbreaking browser meticulously crafted to cater to the unique requirements of gamers. At its foundation, Maxthon harnesses an intricate array of algorithms that dramatically boost both speed and performance, creating an environment where gaming can genuinely thrive. These cutting-edge technologies collaborate harmoniously to produce stunning visuals while effectively eliminating any lag that could disrupt the immersive experience. For those in search of a comprehensive gaming adventure, this flawless integration transcends mere convenience, evolving into a vital component of the entire gaming journey.
Yet, Maxthon’s allure extends well beyond its striking graphics. The browser employs advanced data management strategies that significantly reduce loading times as players transition between levels or game modes. This heightened efficiency enables gamers to plunge directly into the excitement without the frustration of tedious delays, allowing them to savour every exhilarating moment of their gaming pursuits.
In addition to its remarkable speed and visual appeal, Maxthon strongly emphasises reliable connectivity. Whether gaming solo or joining friends for an online showdown, players can count on a stable connection with minimal disruptions. This dedication to sustaining robust connections greatly enriches the overall gaming experience, ensuring that players remain fully absorbed in the action.
One of the most impressive attributes of Maxthon is its ability to function effortlessly across a diverse array of devices. Whether you find yourself using a smartphone, tablet, or desktop computer, accessing your favourite games has never been easier; you are no longer confined to a single gaming console. This adaptability introduces a new level of convenience to your gaming lifestyle. Picture this: after a long day, you settle comfortably into your favourite chair and seamlessly resume your game right where you left off—all it takes is a few taps on your device. Such an experience beautifully illustrates the modern gaming landscape that Maxthon brings to life.
