KEY CHALLENGES FACING SINGAPORE FSIs
1. Digital Transformation Pressure & Competitive Disruption
Challenge Depth:
- Digital banks are establishing new industry standards with real-time transactions and instantaneous service delivery.
- Traditional FSIs face the “innovator’s dilemma” – they must digitise rapidly without compromising existing operations.
- Legacy systems create technical debt that slows transformation efforts
- Customer expectations have fundamentally shifted toward digital-first experiences
- AI integration is becoming critical for competitive advantage, but requires a robust digital infrastructure
Business Impact:
- Loss of market share to digital-native competitors
- Decreased customer satisfaction and loyalty
- Reduced operational efficiency
- Higher costs of maintaining dual (legacy + digital) systems
2. Expanding Attack Surface & Threat Landscape
Challenge Depth: The article reveals that Singapore FSIs face multiple sophisticated threats:
- Phishing Attacks: Singapore’s FSI industry was the leading target in 2022
- Ransomware: Described as the most formidable threat, now enhanced by AI and ransomware-as-a-service models
- DDoS Attacks: 22% year-over-year increase in attacks on FSIs
- Insider Threats: High rates of insider data breaches due to complex corporate structures
- AI-Enhanced Attacks: Cybercriminals leveraging AI to create more sophisticated attack vectors
Threat Evolution:
- Hybrid cloud environments create multiple entry points
- Mobile banking apps expand the attack surface
- API vulnerabilities in digital services
- Supply chain attacks through third-party integrations
3. Identity Security & Access Management Crisis
Challenge Depth:
- Exponential growth in digital identities across hybrid environments
- Manual processes for tracking data access and user identities lead to inaccuracies
- Complex provisioning processes (the article mentions one bank taking over 10 days for workload access)
- Lack of unified identity management across on-premise and cloud systems
- Difficulty in managing privileged access across diverse technology stacks
Operational Impact:
- 91% of identity security decision-makers identified budgetary constraints as the primary obstacle
- 77% pointed to”limited executive sponsorship or focus”
- Resource drain on IT teams for manual identity management tasks
4. Regulatory Compliance Complexity
Challenge Depth: Singapore FSIs must navigate multiple regulatory frameworks:
- MAS Technology Risk Management (TRM) guidelines
- Cybersecurity Act amendments passed in May 2024, CsaReedsmith
- Critical Information Infrastructure (CII) requirements
- Cross-border data protection requirements
- Emerging AI governance requirements
Compliance Burden:
- Cyber hygiene practices became mandatory from May 10, 2024, Singapore MAS Cybersecurity Compliance | ImmuniWeb
- Need for continuous monitoring and reporting
- Requirements for incident response and business continuity planning
5. Resource & Skills Constraints
Challenge Depth:
- Cybersecurity talent shortage in Singapore
- Competition for skilled professionals with digital banks and tech companies
- Need specialised skills in cloud security, AI security, and identity management
- Training the existing workforce on new technologies while maintaining operations
COMPREHENSIVE SOLUTIONS
1. Modern Identity Security Architecture
Technical Solutions:
- Implement Zero Trust Architecture with continuous verification
- Deploy AI-driven risk assessment and automated access certification
- Unified identity platforms that manage both on-premise and cloud identities
- Privileged Access Management (PAM) solutions with just-in-time access
Business Benefits: The article provides concrete examples:
- One financial services firm reduced frontline manager time on user access certifications by 80% through AI-driven automation
- A regional bank streamlined access provisioning from over 10 days to less than 24 hours, saving over US$1.5 million annually
2. Integrated Threat Intelligence & Response
Strategic Approach:
- Deploy Security Information and Event Management (SIEM) with AI/ML capabilities
- Implement threat hunting capabilities with behavioural analytics
- Establish real-time threat intelligence sharing within the financial ecosystem
- Deploy endpoint detection and response (EDR) across all devices
3. Cloud-First Security Architecture
Implementation Strategy:
- Adopt Cloud Security Posture Management (CSPM) tools
- Implement container security for microservices architectures
- Deploy API security gateways with rate limiting and authentication
- Use Infrastructure as Code (IaC) with security scanning
4. AI-Powered Security Operations
Technology Integration:
- Machine learning for anomaly detection in transaction patterns
- Automated incident response workflows
- Predictive threat modelling
- Natural language processing for security alert analysis
HOW CSA CAN HELP SINGAPORE FSIs
1. Regulatory Guidance & Frameworks
Current Initiatives: The
- CybeThe rsecurity Act provides a framework for protecting critical infrastructure. Cybersecurity Act | Cyber Security Agency of Singapore
- Expanded Cyber Essentials and Cyber Trust certification marks to include cloud security, AI security, and operational technology securityCSA’ss Cyber Essentials and Cyber Trust Marks expanded to include Cloud Security, Artificial Intelligence and Operational Technology | Cyber Security Agency of Singapore
- Safe App Standard 2.0 provides comprehensive guidance for mobile application security. Safe App Standard 2.0 | Cyber Security Agency of Singapore
FSI-Specific Support:
- Internet hygiene rating system for Singapore-based digital financial platform..s Financial Platforms – June 6 2025 | Cyber Security Agency of Singapore
- Sector-specific cybersecurity guidelines tailored to FSI risks
- Regular updates on emerging threats targeting financial services
2. Threat Intelligence & Information Sharing
Collaborative Initiatives:
- Strategic collaboration with FS-ISAC for information sharing and cyber exercises within financial services. FS-ISAC and CSA Extend Strategic Collaboration to Bolster Singapore’s Cybersecurity
- Real-time threat intelligence feeds specific to FSI attack patterns
- Industry-wide incident reporting and analysis
- Early warning systems for emerging threats
3. Capacity Building & Skills Development
Training Programs:
- Cybersecurity certification programs for FSI professionals
- Executive awareness programs for C-suite decision makers
- Technical training on emerging technologies (AI security, cloud security)
- Incident response simulation exercises
4. Technology Standards & Best Practices
Standards Development:
- AI cybersecurity guidance addressing risks and best practices.. AI Cybersecurity Guidance Summary – NYDFS and Singapore CSA
- Cloud security implementation guidelines
- Identity management standards for financial services
- API security best practices
5. Incident Response & Recovery Support
Emergency Response:
- 24/7 cyber incident response coordination
- Forensic analysis support for major incidents
- Business continuity guidance during cyber crises
- Cross-agency coordination for systemic threats
6. Research & Innovation
Forward-Looking Initiatives:
- Operational Technology Cybersecurity Masterplan 2024 Singapore’s Operational Technology Cybersecurity Masterplan 2024 | Cyber Security Agency of Singapore
- Research partnerships with local universities and FSIs
- Pilot programs for emerging security technologies
- Sandbox environments for testing new security solutions
STRATEGIC RECOMMENDATIONS
For FSIs:
- Prioritise Identity Security: Treat identity as the new security perimeter
- Invest in AI-Driven Security: Leverage automation to scale security operations
- Adopt Zero Trust Architecture: Assume breach and verify continuously
- Build Security into Digital Transformation: Security by design, not as an afterthought
For CSA:
- Enhance Public-Private Partnerships: Deepen collaboration with the FSI sector
- Develop FSI-Specific Threat Intelligence: Create dedicated intelligence sharing for financial services
- Accelerate Skills Development: Address the cybersecurity talent gap through targeted programs
- Promote Regional Cooperation: Lead ASEAN-wide FSI cybersecurity initiatives
The convergence of digital transformation pressures, sophisticated cyber threats, and regulatory requirements creates a complex challenge landscape for Singapore’s financial institutions (financial institutions (FSIs. Success requires a coordinated approach that combines modern technology solutions, regulatory compliance, and strong public-private collaboration, facilitated by CSA’s leadership.
Comprehensive Analysis: Challenges Facing Singapore FSIs and Government Solutions
Executive SummarySingapore’s
Singapore’s Financial Services Institutions (FSIs) are navigating an unprecedented convergence of digital transformation imperatives, sophisticated cyber threats, and evolving regulatory landscapes. This examines the multifaceted challenges facing the Singapore financial services industry (INES MUL). It provides an in-depth assessment of solutions from key government agencies, including the Monetary Authority of Singapore (MAS), Cyber Security Agency of Singapore (CSA), and broader government initiatives.
Part I: Critical Challenges Facing Singapore FSIs
1. Digital Transformation & Competitive Disruption
1.1 Market Pressure from Digital Banks
- Challenge Magnitude: Digital banks are redefining industry standards, personalised transactions, instantaneous access, and AI-powered personalised services
- Competitive Disadvantaged traditional FSIs face the”innovator’s dilemma ” – they must digitise rapidly without disrupting existing operations serving millions of customers.
- Legacy System Burden: Decades-old core banking systems create technical debt, with some institutions running on COBOL-based mainframes that resist modern integration
- Customer Expectation Shift: Post-COVID customers demand digital-first experiences, with 78% of banking interactions now expected to be digital
1.2 AI Integration Imperatives
- Competitive Gap: Failure to implement AI will leave incumbents significantly behind digital-native competitors
- Infrastructure Requirements: AI demands robust cloud infrastructure, high-quality data pipelines, and advanced security frameworks
- Talent Scarcity: Competition for AI talent with global tech companies and digital banks
- Regulatory Uncertainty: Balancing AI innovation with regulatory compliance in an evolving framework
2. Expanding Cyber Threat Landscape
2.1 Singapore-Specific Threat Profile
- Phishing Dominance: Singapore’s FSI industry was the leading target of phishing attacks in 2022, indicating a sophisticated threat actor focus
- Ransomware Evolution: Described as a formidable threat,o now enhanced by ransomware-as-a-service models and AI capabilities
- DDoS Surge: 22% year-over-year increase in DDoS attacks specifically targeting FSIs
- Insider Threats: High rates of insider data breaches are exacerbated by complex corporate structures and manual access management
2.2 Attack Surface Expansion
- Hybrid Cloud Vulnerabilities: Migration to hybrid models creates multiple entry points and complex security boundaries
- Mobile Banking Risks: Surge in mobile adoption increases endpoint vulnerabilities and man-in-the-middle attack opportunities
- API Proliferation: Open banking initiatives and digital service integrations create numerous API endpoints requiring security
- Third-Party Risks: Increasing reliance on fintech partnerships and cloud services expands supply chain attack vectors
2.3 Advanced Persistent Threats (APTs)
- Nation-State Actors: Singapore’s role as a financial hub attracts sophisticated state-sponsored attacks
- Business Email Compromise (BEC): Highly targeted attacks leveraging social engineering and insider knowledge
- Zero-Day Exploits: Increasing use of previously unknown vulnerabilities in critical financial software
3. Identity Security & Access Management Crisis
3.1 Scale of Identity Challenge
- Digital Identity Explosion: Exponential growth in machine-to-machine identities, service accounts, and human identities across hybrid environments
- Complex Access Patterns: Cloud migrations create intricate access requirements across on-premise, cloud, and hybrid systems
- Privileged Access Sprawl: Difficulty tracking and managing administrative privileges across diverse technology stacks
3.2 Operational Inefficiencies
- Manual Processes: Reliance on manual ticket systems for access provisioning leads to delays and errors
- Compliance Gaps: 91% of identity security decision-makers identify budgetary constraints as the primary obstacle
- Executive Misalignment: 77% cite” limited executive sponsorship,” indicating a C-suite understanding gap
3.3 Business Impact
- Provisioning Delays: Some banks require over 10 days for simple workload access provisioning
- Resource Drain: IT teams are spending disproportionate time on manual identity management tasks
- Security Vulnerabilities: Inconsistent access controls create potential breach points
4. Regulatory Compliance Complexity
4.1 Multi-Layered Regulatory Environment
- MAS Requirements: Technology Risk Management (TRM) guidelines mandate comprehensive cybersecurity frameworks
- CSA Mandates: Cybersecurity Act amendments requiring specific cyber hygiene practices
- Cross-Border Compliance: International regulatory requirements for global FSI operations
- Emerging AI Regulations: Anticipated governance frameworks for AI deployment in financial services
4.2 Implementation Challenges
- Resource Allocation: Compliance requirements consuming significant IT and legal resources
- Technical Integration: Difficulty integrating compliance monitoring across diverse technology platforms
- Reporting Burden: Multiple reporting requirements to different agencies create administrative overhead
5. Operational Technology (OT) & Infrastructure Security
5.1 Critical Infrastructure Vulnerabilities
- Legacy OT Systems: Ageing operational technology systems with limited security capabilities
- Convergence Risks: IT/OT convergence creates new attack vectors
- Physical Security Integration: Need to secure both digital and physical infrastructure components
5.2 Business Continuity Threats
- Single Points of Failure: Critical systems lacking adequate redundancy
- Disaster Recovery Gaps: Insufficient testing of recovery procedures for cyber incidents
- Vendor Dependencies: Heavy reliance on third-party infrastructure providers
6. Talent & Skills Crisis
6.1 Cybersecurity Skills Shortage
- Regional Competition: Competition with tech companiesspecialisedagenciesser FSIs for a limited talent pool
- Specialised Skills Gap: Particular shortage in cloud security, AI security, and identity management specialists
- Training Lag: Time required to upskill the existing workforce while maintaining operations
6.2 Executive Understanding Gap
- C-Suite Awareness: Limited understanding of cybersecurity implications at the board level
- Investment Justification: Difficulty articulating ROI for cybersecurity investments
- Strategic Alignment: Disconnect between business strategy and cybersecurity priorities
Part II: MAS (Monetary Authority of Singapore) Solutions & Initiatives
1. Technology Risk Management (TRM) Framework
1.1 Updated TRM Guidelines (2021)
- Comprehensive Coverage: Enhanced guidelines addressing technology risk management principles and best practices
- Cyber Intelligence Requirements: Mandate for FSIs to procure cyber intelligence monitoring services
- Incident Response Standards: Establishment of comprehensive cyber incident response and management plans
- Regular Assessment Requirements: Periodic review and updating of risk management processes
1.2 Key TRM Components
- Governance Structure: Board-level oversight requirements for technology risk
- Risk Assessment Framework: Systematic approach to identifying and evaluating technology risks
- Security Controls: Implementation of appropriate security measures across all technology layers
- Vendor Management: Enhanced oversight of third-party technology service providers
2. Digital Banking Framework
2.1 Digital Bank Licensing
- Regulatory Parity: Ensuring digital banks meet the same security standards as traditional banks
- Innovation Support: Providing regulatory clarity to encourage responsible innovation
- Competitive Balance: Creating a level playing field between traditional and digital FSIs
2.2 Open Banking Security Standards
- APauthorizationquirements: Mandating robust authentication and authorisation for open banking APIs
- Data Protection Standards: Ensuring consumer data protection in the open banking ecosystem
- Liability Framework: Clear allocation of responsibilities for security breaches
3. Supervisory Technology (SupTech) Initiatives
3.1 Automated Monitoring
- Real-Time Surveillance: Implementation of continuous monitoring systems for systemic risks
- Data Analytics: Advanced analytics for pattern recognition and anomaly detection
- Regulatory Reporting Automation: Streamlined reporting processes, reducing compliance burden
3.2 RegTech Adoption Support
- Regulatory Sandbox: Providing a safe environment for testing innovative compliance solutions
- Industry Collaboration: Facilitating knowledge sharing on regulatory technology solutions
- Standards Development: Creating common standards for regulatory technology implementation
4. Cross-Border Payment Security
4.1 Project Nexus Integration
- Global Payment Connectivity: Enabling instant cross-border payments through multilateral linkages
- Security Framework: Ensuring robust security harmonisations for international payment flows
- Regulatory Harmonisation Working with international partners on consistent security standards
4.2 Central Bank Digital Currency (CBDC) Preparation
- Infrastructure Security: Developing secure infrastructure for potential digital currency implementation
- Privacy Protection: Balancing transparency requirements with privacy protection
- Interoperability Standards: Ensuring compatibility with international CBDC initiatives
5. Fintech Regulatory Support
5.1 Regulatory Sandbox Enhancement
- Security Testing Environment: Providing secure environments for fintech innovation testing
- Regulatory Clarity: Clear guidance on security requirements for emerging technologies
- Industry Mentorship: Connecting fintech startups with established FSIs for knowledge transfer
5.2 Industry Development Programs
- Capability Building: Supporting the development of local fintech capabilities
- International Collaboration: Facilitating partnerships with global fintech ecosystems
- Standards Setting: Leading the development of industry security standards
Part III: CSA (Cyber Security Agency) Solutions & Support
1. National Cybersecurity Strategy Implementation
1.1 Critical Information Infrastructure (CII) Protection
- Sector-Specific Guidelines: Tailored cybersecurity requirements for the financial services sector
- Mandatory Reporting: Incident reporting requirements for early threat detection
- Regular Assessments: Periodic security evaluations of critical systems
1.2 Cybersecurity Act Enhancements
- Expanded Coverage: Updated legislation covering emerging technologies and threats
- Enforcement Mechanisms: Clear penalties for non-compliance with cybersecurity requirements
- International Cooperation: Framework for cross-border cybersecurity collaboration
2. Threat Intelligence & Information Sharing
2.1 SG-CERT Services
- Real-Time Threat Intelligence: Continuous monitoring and analysis of cyber threats
- Incident Response Coordination: 24/7 support for cyber incident management
- Vulnerability Disclosure: Coordinated disclosure of security vulnerabilities
2.2 Industry Collaboration Programs
- FS-ISAC Partnership: Strategic collaboration with Financial Services Information Sharing and Analysis Centre
- Threat Intelligence Sharing: Real-time sharing of threat indicators and attack patterns
- Joint Exercises: Regular cybersecurity drills and simulations
3. Cybersecurity Skills Development
3.1 National Cybersecurity Industry-recognised Professional
- Professional Certification on Industry-recognised cybersecurityyertifications
- Skills Framework: Clear career progression paths for cybersecurity professionals
- Continuous Learning: Ongoing education programs for emerging threats and technologies
3.2 Executive Education
- C-Suite Awareness Programs: Cybersecurity governance training for senior executives
- Board-Level Education: Director education on cybersecurity oversight responsibilities
- Strategic Planning Support: Assistance with cybersecurity strategy development
4. Technology Standards & Guidelines
4.1 Cybersecurity Frameworks
- Multi-Organisational Security Framework: A Comprehensive Approach to Organisational Cybersecurity
- Industry Best Practices: Sector-specific implementation guidance
- Management Tools: Self-assessment capabilities for organisations
4.2 Emerging Technology Guidance
- AI Security Guidelines: Best practices for artificial intelligence deployment security
- Cloud Security Standards: A Comprehensive Cloud Adoption Security Framework
- IoT Security Requirements: Guidelines for Internet of Things device security
5. Incident Response & Recovery
5.1 National Incident Response Framework
- Coordinated Response: Multi-agency coordination for significant cyber incidents
- Recovery Support: Technical assistance for incident recovery
- Lessons Learned: Post-incident analysis and improvement recommendations
5.2 Business Continuity Planning
- Continuity Framework: Guidelines for maintaining operations during cyber incidents
- Testing Requirements: Regular testing of business continuity plans
- Industry Coordination: Sector-wide continuity planning collaboration
Part IV: Broader Government Initiatives & Support
1. Whole-of-Government Cybersecurity Approach
1.1 Inter-Agency Coordination
- Cybersecurity Coordination Centre: Central coordination of national cybersecurity efforts
- Multi-Agency Task Forces: Harmonisation addressing cross-sector challenges
- Policy H Harmonisation, ensuring consistent cybersecurity policies across the government
1.2 International Cooperation
- ASEAN Cybersecurity Collaboration: Regional cooperation on cybersecurity threats
- Bilateral Partnerships: Strategic cybersecurity partnerships with key allies
- Global Standards Participation: Active participation in international cybersecurity standards development
2. Research & Development Support
2.1 National Research Programs
- Cybersecurity Research Grants: Funding for cutting-edge cybersecurity research
- Public-Private Partnerships: Collaboration between government, academia, and industry
- Innovation Hubs: Creating centres of excellence for cybersecurity research
2.2 Technology Development Initiatives
- Local Capability Building: Supporting the development of indigenous cybersecurity capabilities
- Startup Ecosystem Support: Nurturing the cybersecurity startup ecosystem
- International Talent Attraction: Programs to attract global cybersecurity talent
3. Economic Incentives & Support
3.1 Tax Incentives
- R&D Tax Benefits: Tax incentives for cybersecurity research and development
- Investment Allowances: Accelerated depreciation for cybersecurity infrastructure
- Startup Support: Tax relief for cybersecurity startups and scale-ups
3.2 Procurement Programs
- Government as First Customer: Government procurement of innovative cybersecurity solutions
- Local Preference: Preference for locally developed cybersecurity solutions
- Risk Sharing: Government co-investment in cybersecurity technology development
4. Education & Awareness
4.1 National Digital Literacy
- Public Education Campaigns: Broad-based cybersecurity awareness programs
- School Curriculum Integration: Cybersecurity education in the formal education system
- Community Outreach: Targeted programs for different demographic groups
4.2 Professional Development
- Continuing Education: Ongoing professional development requirements
- Industry Certification: Recognition of international cybersecurity certifications
- Skills Upgrading: Government-supported skills upgrading programs
Part V: Strategic Implementation Roadmap
Phase 1: Foundation Building (0-12 months)
Immediate Priorities
- Regulatory Compliance: Ensure full compliance with updated MAS TRM guidelines and CSA requirements
- Risk Assessment: Comprehensive cybersecurity risk assessment across all FSI operations
- Executive Engagement: Board-level cybersecurity governance implementation
- Incident Response: Establish robust incident response capabilities with CSA coordination
Key Milestones
- Complete TRM compliance assessment
- Implement mandatory cyber hygiene practices
- Establish executive cybersecurity governance
- Deploy basic threat intelligence capabilities
Phase 2: Capability Enhancements)
Strategic Initiatives
- Identity Security MMoModernisationlement comprehensive identity and access management systems
- Threat Intelligence Integration: Deploy advanced threat intelligence and sharing capabilities
- Skills Development: Launch comprehensive modernisation development
- Technology Modernisation: Begins systematic modernisation of legacy security systems
Key Milestones
- Deploy a zero-trust architecture foundation
- Implement AI-driven security operations
- Complete staff cybersecurity training programs
- Establish threat intelligence sharing partnerships
Phase 3: Advanced Capabilities (24-36 months)
Advanced Implementation
- AI-Powered Security: Full deployment of artificial intelligence for security operations
- Ecosystem Integration: Complete integration with national and international cybersecurity frameworks
- Innovation Leadership: Become leaders in cybersecurity innovation and best practices
- Regional Collaboration: Lead regional cybersecurity initiatives and standards
Key Milestones
- Achieve advanced cybersecurity maturity levels
- Lead regional cybersecurity collaboration
- Implement next-generation security technologies
- Establish innovation partnerships globally
Part VI: Success Metrics & Evaluation Framework
Quantitative Metrics
Security Effectiveness
- Incident Reduction: 50% reduction in successful cyber attacks within 24 months
- Response Time: Mean time to incident detection and response under 30 minutes
- Compliance Score: 100% compliance with MAS TRM and CSA requirements
- Vulnerability Management: 95% of critical vulnerabilities remediated within 72 hours
Operational Efficiency
- Access Provisioning: Reduce access provisioning time from 10+ days to under 24 hours
- Automation of security operations is automated
- Cost OptimisationAchieve ROI of 3030% Utilisation security investments within 36 months
- Resource Utilisation: 80% reduction in manual security management tasks
Business Impact
- Customer Trust: Maintain 95 % % %++ customer satisfaction with digital security
- Regulatory Compliance: Zero regulatory penalties or sanctions
- Innovation Speed: 50% faster deployment of new digital services
- Market Position: Maintain competitive advantage in digital banking
Qualitative Metrics
Strategic Objectives
- Regulatory Recognition: Recognition as a cybersecurity leader by MAS and CSA
- Industry Leadership: Acknowledged as a best practice example by industry peers
- International Standards: Active participation in international cybersecurity standards
- Innovation Ecosystem: CConOrganizationalSiSingapore’scybersecurity innovationn ecosystem
OOrganizationalMaturity
- Sorganizationure: Embedded security-first culture across the organisation
- Executive Engagement: Active board-level cybersecurity governance
- Skills Development: Comprehensive cybersecurity capability across the workforce
- Continuous Improvement: Established continuous improvement processes
Conclusion
Singapore’s financial services institutions (FSIs) face an unprecedented convergence of challenges tharequiressre a coordinated response from multiple stakeholders. The combination of digital transformation pressures, sophisticated cyber threats, regulatory complexity, and talent constraints demands a multifaceted approach.
The solutions provided by MAS, CSA, and broader government initiatives offer a robust framework for addressing these challenges. However, success requires active engagement from FSIs in implementing these solutions, combined with continued evolution of government support as threats and technology landscapes change.
The strategic implementation roadmap provides a practical path forward, with clear milestones and success metrics to ensure progress. The ultimate goal is not just compliance or risk mitigation, but the establishment of Singapore’s FSI sector as a global leader in secure, innovative financial services.
This comprehensive approach, combining regulatory excellence, technological innovation, and public-private collaboration, positions Singapore to maintain its leadership as a global financial hub while ensuring the highest standards of cybersecurity and customer protection.
Digital Storm: A Singapore FSI Under Siege
Chapter 1: The Calm Before
The Singapore skyline glittered in the pre-dawn darkness as Sarah Chen arrived at the Cyber Security Agency’s headquarters on Science Park Drive. As Senior Manager of the Financial Services Cybersecurity Division, she had grown accustomed to early mornings, but something felt different today. The usual hum of overnight monitoring systems seemed more urgent, and the night shift analysts wore expressions of barely contained concern.
“Sarah, thank God you’re here early,” called Marcus Lim, the night shift supervisor, his voice cutting through the ambient noise of keyboards and hushed conversations.”We’ve been tracking some unusual network probes targeting Pacific Banking Group since 0300 hours. The patterns are… sophisticated”
Sarah set down her coffee and immediately switched into crisis mode. Pacific Banking Group was one of the largest traditional banks, serving over 3 million customers across Southeast Asia. Any threat to PBG wasn’t just a corporate crisis—it was a national security concern.
“Show me what we have,” she said, settling into the command centre’s central workstation.
Marcus pulled up a complex network visualisation on the main screen. Red indicators pulsed across multiple entry points, indicating systematic reconnaissance attempts against PBG’s digital infrastructure.
“The attackers are using a combination of techniques we haven’t seen before,” Marcus explained, his finger tracing the attack vectors.”They’re probing the bank’s open banking APIs, but they’re also targeting the legacy SWIFT connections and even the mobile banking infrastructure simultaneously. This isn’t random—they know exactly what they’re looking for.”
Sarah’s mind raced through the implications. A coordinated attack on multiple vectors suggests advanced persistent threat actors, possibly at a nation-state level. The timing was also suspicious: just days after PBG had announced its major AI-powered customer service initiative, making headlines as Singapore’s traditional banking sector’s answer to the digital banks.
“Have we alerted PBG’s security team? she asked.
“Initial contact made at 0315. Their CISO, Dr. Robert Tan, is already in their crisis centre. But Sarah..” Marcus paused, his expression darkening.”TheThere’sething else. The attack signatures are eerily similar to those that hit targeted European banks last month. If this is the same group, they don’t just steal data—they demonstrate their capabilities by disrupting operations.”
Chapter 2: The Storm Hits
By 0600, Sarah had established a direct command link with PBG’s crisis centre. The bank’s imposing headquarters in Raffles Place buzzed with emergency activity as its cybersecurity team worked frantically to understand and contain the threat.
“Sarah, this is unlike anything we’ve seen.” Dr. Tan’s voice crackled through the secure communication link.”They’re not just prohibited, they’re inside our perimeter. Our identity management system is showing unauthorised access attempts across multiple administrative accounts.”
Sarah’s team had prepared for this moment. Years of tabletop exercises, threat intelligence sharing, and incident response drills had built muscle memory for coordinated crisis response. But theory and reality were vastly different beasts.
“Robert, I need you to immediately activate your incident response protocol,” Sarah instructed, her voice steady despite the adrenaline coursing through her system.”Isolate all non-critical systems, and implement the emergency information sharing protocol. My team is pushing real-time threat intelligence to your security operations centre now.”
On her command screen, Sarah watched as her team activated Singapore’s Financial Services Cyber Incident Response Framework. Automated alerts were sent to the Monetary Authority of Singapore, relevant law enforcement agencies, and other major financial institutions in the alert network. This wasn’t just about saving one bank—it was about protecting Singapore’s entire financial ecosystem.
“Ma’a, called out Jennifer Wong, one of CCSA’s top threat analysts, we’re seeing a spill-over reconnaissance against two other major banks. The attackers are using the intelligence they’ve gathered from PBG to probe for similar vulnerabilities across the sector.”
This was Sarah’s worst-case scenario playing out in real time. A coordinated attack designed not just to compromise one institution, but to test the resilience of Singapore’s entire financial infrastructure.
Chapter 3: The Human Element
As the morning progressed, the true sophistication of the attack became clear. The team was not made up of technicians—they understood human psychology and organisational culture.
“Sara. we have a problem”” Dr.Tan’ss voice carried a new level of urgency.”They have initiated a social engineering campaign targeting our senior executives. Our CEO received a call thirty minutes ago from someone claiming to be from MAS, requesting emergency access credentials for”regulatory compliance verification” The caller knew details about our recent AI implementation that should be confidential.
Sarah felt her stomach tighten. This was the convergence of technical and human attack vectors that made modern cyber threats so dangerous. While her technical teams battled the digital intrusion, the attackers were simultaneously exploiting human trust and authority relationships.
“Robert, I need you to immediately contact all C-suite executives and board members. No one—and I mean no one—provides any access or information to anyone without going through the verified incident response chain, also activating our executive protection protocol.
Sarah turned to her deputy, Alex Kumar, who had been coordinating with law enforcement. Alex, I need immediate contact with the Commercial Affairs Department and INTERPOL’s cybercrime unit. If these are the same actors who hit Europe, we need international intelligence sharing activated immediately.”
The next few hours became a blur of coordinated defensive actions. Sarah found herself orchestrating a complex ballet of technical countermeasures, stakeholder communications, and strategic decision-making. Every choice carried massive implications—too aggressive a response could disrupt legitimate banking operations for millions of customers, too passive a response could allow the attackers to achieve their objectives.
Chapter 4: The Technical Battle
By midday, the attack had evolved into a sophisticated campaign that showcased the attackers’ deep understanding of modern banking infrastructure. They had managed to establish persistent access to PBG’s hybrid cloud environment and were slowly moving laterally through the network, carefully avoiding detection systems while mapping critical assets.
“Sarah, they’re good,” admitted Jennifer, CSA’s normally unflappable threat analyst. Every time we close one avenue, they pivot to another. They’re using legitimate administrative tools to navigate the network, making it incredibly difficult to distinguish their activities from regular operations.
Sarah stood before the main situation display, watching real-time network traffic flows and security alerts cascade across multiple screens. Years of experience had taught her that the most dangerous moment in any cyber incident was when the technical team became so focused on the immediate threat that they lost sight of the bigger picture.
“Jennifer, I need you to think like an attacker for a moment,” Sarah said, her voice cutting through the technical chatter.”They’ve invested enormous resources in this operationThey’re not here for a quick data grab. What’s their endgame?”
As if in response to her question, Marcus called out from his workstation: “Arah, we’re seeing unusual activity in PBG’s score banking system. They’re not extracting data; they’re mapping transaction flows and customer relationship patterns’s like they’re building a comprehension of how money moves through Singapore’s banking ecosystem.”
The realisation hit Sarah like a physical blow. This wasn’t just an attack on Pacific Banking Group—it was an intelligence-gathering operation for a potential systemic attack on Singapore’s financial infrastructure. The attackers were using PBG as a window into the interconnected network of relationships, systems, and processes that formed the backbone of Southeast Asia’s financial hub.
Chapter 5: Coordinated Response
Sarah immediately escalated the incident to Singapore’s highest cybersecurity response levels. Within minutes, she was on a secure video conference with the Minister for Home Affairs, the Managing Director of MAS, and senior leadership from multiple government agencies.
“Minister, we’re dealing with what appears to be a reconnaissance operation targeting Singapore’s financial infrastructure,” Sarah reported, her voice steady despite the magnitude of the situation. The immediate threat is contained, but the intelligence gathered could enable future attacks against our entire banking sector.”
The response was swift and comprehensive. Singapore’s whole-of-government cybersecurity approach activated like a well-oiled machine. The Monetary Authority of Singapore issued emergency guidance to all financial institutions, law enforcement agencies coordinated with international partners, and diplomatic channels opened discussions with allied cybersecurity agencies.
“Sarah, you have full authority to coordinate whatever response is necessary,” the Minister declared. Singapore’s position as a financial hub depends on maintaining the highest levels of cybersecurity. Whatever resources you need, you have them.”
Back at CSA headquarters, Sarah’s team worked in unprecedented coordination with PBG’s cybersecurity professionals. Using advanced threat hunting techniques and AI-powered behavioural analysis, they began the methodical process of identifying and removing the attackers’ presence from PBG’s systems.
“We’re implementing a controlled deception strategy,arah Dr. Tan explained during one of their hourly coordination calls.”We’re allowing the attackers to think they maintain access while we map their complete infrastructure and methods. Once we have full intelligence on their capabilities, we’ll execute a coordinated removal operation.”
Chapter 6: The Counter-Strike
The breakthrough came at 1800 hours when CSA’s cyber forensics team identified the attackers’ command and control infrastructure. Working with international partners, they had traced the attack to a sophisticated anonymisation operation involving servers in multiple countries and advanced anonymisation techniques.
“Sarah, we’ve identified the threat actor,” Alex reported, excitement barely contained in his voice. It’s the group known as ‘Digital TTypho,’ the same actors responsible for the European banking attacks. “They’re believed to be state-sponsored, with capabilities rivalling those of the most advanced cyber warfare units.
This identification changed everything. Singapore was facing not just a criminal enterprise, but a geopolitical threat with implications far beyond cybersecurity. Sarah found herself at the centre of a response that bridged national security, financial stability, and international diplomacy.
“Initiate Phase 3 of the incident response,” Sarah commanded. Full counterintelligence operations, coordinated with allied agencies. We’re not just defending against this attack; we’re gathering intelligence for future defensive operations.
The counter-operation was a masterpiece of coordination. While maintaining the appearance of ongoing vulnerability, Sarah’s team and their international partners began systematically documenting the attackers’ tool techniques and procedures. Every move the threat actors made was monitored, analysed and added to a growing intelligence picture that would help defend against future attacks.
Chapter 7: Resolution and Reflection
The final phase of the operation lasted 72 hours, during which Sarah’s team executed a coordinated expulsion of the threat actors from PBG’s systems while simultaneously disrupting their command and control infrastructure. The operation required split-second timing across multiple time zones, involving cybersecurity agencies from Singapore, the United States, the European Union, and Australia.
“All systems clean,” Dr. Tan reported at 0300 on the fourth day of the crisis.”We have completed tNSICsic imaging of all affected systems, implemented additional security controls, and restored all services to normal operations. Customer data integrity is confirmed, andthere’ss no evidence of financial theft or manipulation.”
Sarah allowed herself a moment of relief, but she knew the real work was just analysing the intelligence gathered during the incident, which would need to be analysed and shared with partner agencies, and used to strengthen Singapore’s cybersecurity posture against future threats.
In the days that followed, Sarah found herself in briefing rooms across Singapore’s government complex, explaining the incident’s implications to senior leadership and helping shape policy responses. The attack had revealed both strengths and vulnerabilities in Singapore’s financial cybersecurity infrastructure.
“The good news,” Sarah explained to the MAS leadership team,” is that our incident response framework performed exactly as designed. The coordination between CSA, MAS, law enforcement, and the private sector was seamless. We contained a sophisticated threat actor within 96 hours and transformed a defensive operation into an intelligence-gathering opportunity.
“But,” prompted the Managing Director of MAS.
“But this attack was a demonstration of capabilities, not a full-scale assault,” Sarah continued. Digital Typhoon was testing our responses, mapping our defences, and gathering intelligence about Singapore’s financial infrastructure. They’ll be back, and next time they’ll be better prepared.”
Chapter 8: Lessons and Legacy
Three months after the attack, Sarah stood before an international conference of financial cybersecurity professionals in Geneva, sharing the lessons learned from Singapore’s experience with Digital Typhoon.
“The attack on Pacific Banking Group taught us that modern cyber threats require not just technical solutions, but comprehensive coordination across multiple dimensions,” she explained to the audience of global cybersecurity leaders. We needed technical excellence, regulatory coordination, international cooperation, and strategic thinking about geopolitical implications.”
The incident had indeed transformed Singapore’s approach to financial cybersecurity. New protocols required enhanced information sharing between Financial Stability Institutions (FSIs), improved coordination with international partners, and more sophisticated threat intelligence capabilities. Most importantly, it had demonstrated that cybersecurity was no longer just a technical challenge—it was a national security imperative requiring whole-of-government coordination.
“The most crucial lesson,” Sarah concluded her Geneva presentation,” was that cybersecurity professionals today must be more than technical experts. We must be strategic thinkers, diplomatic coordinators, and crisis managers capable of operating across multiple domains simultaneously.”
Epilogue: The Continuing Mission
Back in Singapore, Sarah continued her work at CSA with a deeper understanding of the evolving threat landscape. The Digital Typhoon incident had been a defining moment in her career and in Singapore’s cybersecurity evolution. It had proven that with proper preparation, coordination, and strategic thinking, even the most sophisticated threats could be defeated.
But Sarah knew that the victory was temporary. In the digital age, cybersecurity was not a problem to be solved but a capability to be continuously developed and refined. Every day brought new threats, new vulnerabilities, and new challenges requiring constant vigilance and adaptation.
As she reviewed the latest threat intelligence reports in her office overlooking Singapore’s financial district, Sarah reflected on the responsibility she carried. Protecting Singapore’s position as a global financial hub required not only defending against current threats but also anticipating and preparing for challenges that hadn’t yet emerged.
The skyline outside her window represented more than just buildings and businesses—it represented trust, stability, and prosperity that depended on the invisible work of cybersecurity professionals worldwide. Sarah understood that her mission was not just about preventing attacks, but about preserving faith in the digital systems that had become the foundation of modern life.
The next threat was always just a click away, but Singapore was ready.
This story, while fictional, is based on real cybersecurity challenges and response frameworks used by Singapore’s government agencies and financial institutions. It illustrates the complexity of modern cyber threats and the coordinated response required to protect critical national infrastructure,
Cybersecurity Tips To Prevent Fraud
- Keep devices updated: Regularly update your computer and mobile devices to patch security vulnerabilities.
- Use security software: Install antivirus and anti-malware protection on your computers and schedule regular scans.
- Practice good password habits: Create strong, unique passwords for each account, enable multi-factor authentication, and avoid sharing passwords.
- Secure your home network: Set strong Wi-Fi passwords, use proper encryption (at least WPA2), update router software, and consider hiding your network.
- Defend against phishing/vishing: Be vigilant about suspicious emails or calls requesting personal information, and verify legitimacy through official channels.
- Back up your data: To recover from potential compromises, regularly copy files to external storage or secure cloud services.
- Educate family members: Discuss internet security with children and older relatives who may be vulnerable to different types of cyber tricks.
- Prevent identity theft: Shred sensitive documents, avoid suspicious links, and regularly review your credit report.
- Know what to do if victimized: Consider enabling fraud alerts or credit freezes if your information is compromised.
- Control your information: Be cautious about sharing sensitive information online and regularly review privacy settings.
According to the article, the global financial impact of cyber fraud is rising dramatically, with victims losing $37.4 billion to cybercriminals in the past five years. Phishing scams are the most common, while investment scams are the costliest (over $4.5 billion lost in 2023).

The article also mentions that scammers are increasingly using AI tools like deepfakes and large language models to create more sophisticated fraud attempts.

Crime Prevention Methods
Crime prevention encompasses a variety of strategies designed to reduce criminal activity by addressing its root causes and opportunities. Here are the main approaches to crime prevention:
Situational Crime Prevention
These methods focus on reducing opportunities for crime by making criminal acts more difficult and risky:
- Target hardening: Using physical barriers like locks, alarms, and security systems to protect property
- Access control: Limiting entry to specific areas through key cards, security gates, or doormen
- Natural surveillance: Designing spaces to increase visibility (better lighting, removing visual obstructions)
- CCTV and surveillance: Installing cameras and monitoring systems to deter criminals and collect evidence
- Environmental design: Using CPTED (Crime Prevention Through Environmental Design) principles to create safer spaces

Social Crime Prevention
These strategies address the underlying social factors that contribute to crime:
- Education and awareness programs: Teaching people about risks and prevention strategies
- Community engagement: Neighborhood watch programs, community policing initiatives
- Youth intervention programs: After-school activities, mentoring, and education to provide positive alternatives
- Economic opportunity development: Job training, employment programs, and economic revitalization
- Family support services: Counseling, parenting classes, and support for at-risk families

Law Enforcement Strategies
Proactive approaches by police and criminal justice systems:
- Hot spot policing: Concentrating resources in high-crime areas
- Problem-oriented policing: Identifying and addressing specific crime problems
- Intelligence-led policing: Using data analysis to predict and prevent crime
- Swift and inevitable consequences: Ensuring quick and consistent responses to criminal behaviour
- Focused deterrence: Targeting specific criminal behaviours with enhanced enforcement

Technological Prevention
Using technology to prevent various types of crime:
- Cybersecurity measures: Firewalls, anti-virus software, encryption, and multi-factor authentication
- Biometric security: Fingerprint scanners, facial recognition, and other identity verification methods
- Smart home security: Internet-connected security systems that can be monitored remotely

- Location tracking: GPS monitoring for high-risk offenders
- Data analytics: Using big data to identify patterns and predict potential criminal activity
Individual Prevention Measures
Steps that individuals can take to reduce their risk:
- Personal awareness: Being alert to surroundings and potential dangers
- Target removal: Not displaying valuables, securing personal information
- Routine adjustments: Varying routes and schedules to avoid predictability
- Self-defence training: Learning physical defence techniques and situational awareness
- Building social connections: Developing networks of neighbours who watch out for each other
Each approach has strengths and limitations, and the most effective crime prevention strategies employ multiple methods in coordination.

Crime Prevention Methods in Singapore
Singapore is known for its low crime rates and effective crime prevention strategies. Here’s how the various crime prevention methods are applied in the Singapore context:
Situational Crime Prevention in Singapore
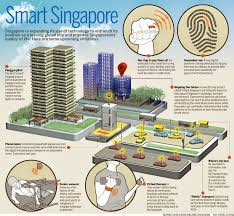
- Extensive CCTV network: Singapore has one of the world’s most comprehensive public surveillance systems with over 90,000 police cameras installed across public housing estates, public areas, and transportation networks.
- Smart Nation initiatives: The government’s Smart Nation program includes sensors and surveillance technologies that enhance public safety.
- Housing design: HDB (Housing & Development Board) flats are designed with security features and community spaces that promote natural surveillance.
- Police cameras: The PolCam initiative places police cameras in public housing blocks and common areas to deter crime and aid investigations.
- Secured By Design: Commercial buildings and public facilities implement crime prevention through environmental design principles.
Social Crime Prevention in Singapore

- Community Policing: The Singapore Police Force’s Community Policing System divides neighbourhoods into smaller sectors with dedicated Neighborhood Police Centers.
- Citizens on Patrol: Volunteer residents patrol their neighbourhoods alongside police officers.
- Yellow Ribbon Project: Rehabilitation and reintegration programs for ex-offenders to reduce recidivism.
- Racial Harmony policies: Programs that promote social cohesion and reduce tensions between different ethnic groups.
- Education system: Schools incorporate character development and values education to promote law-abiding behaviour.

Law Enforcement Strategies in Singapore

- Swift and sure justice: Singapore’s criminal justice system is known for its efficiency and certainty of punishment.
- Deterrent sentencing: Relatively harsh penalties for crimes serve as strong deterrents.
- Low corruption: Strong anti-corruption measures ensure police integrity.
- Data-driven policing: The Police Intelligence Department uses analytics to identify crime patterns and deploy resources effectively.
- Community engagement: Regular community outreach by Neighbourhood Police Centres helps build trust and gather intelligence.
Technological Prevention in Singapore
- National Digital Identity System: Singpass provides secure digital identification for government and financial services.
- Cybersecurity infrastructure: The Cyber Security Agency of Singapore coordinates national efforts to protect critical infrastructure.
- Police technology: Advanced tools include the POLCAM 2.0, which features analytics capabilities, and the i-Witness mobile app, enabling citizens to report incidents.
- Smart lamp posts: As part of Smart Nation initiatives, lamp posts equipped with sensors and cameras enhance public safety.
- Cashless society initiatives: Reducing cash transactions helps prevent certain types of theft and robbery.

Individual Prevention Measures Promoted in Singapore
- SGSecure app: A mobile application that allows citizens to report suspicious activities and receive emergency alerts.
- Public education campaigns: Regular campaigns, such as “Low Crime Doesn’t Mean No Crime,” remind citizens to remain vigilant.
- Crime prevention messaging: Frequent public service announcements about scams and new crime trends.
- Neighbourhood watch groups: Resident committees and neighbourhood watch groups in residential areas.
- Public transport safety: Campaigns educating commuters about safety measures and reporting mechanisms.
Unique Aspects of Singapore’s Approach
- Total Defence: A national ideology that includes social and psychological defence against crime.
- Multi-agency collaboration: Different government agencies work together on crime prevention.
- Strict regulations: Controls on weapons, drugs, and public disorder serve as preventative measures.
- Community involvement: Strong emphasis on citizen participation in crime prevention.
- Integrated approach: Combining strict enforcement with rehabilitation and social support.
Singapore’s success in maintaining low crime rates is attributed to its comprehensive, multi-faceted approach, which combines strong enforcement with community engagement and technological innovation.
Secure browsing
When it comes to staying safe online, using a secure and private browser is crucial. Such a browser can help protect your personal information and keep you safe from cyber threats. One option that offers these features is the Maxthon Browser, which is available for free. It comes with built-in AdBlock and anti-tracking software to enhance your browsing privacy.

Maxthon Browser is dedicated to providing a secure and private browsing experience for its users. With a strong focus on privacy and security, Maxthon implements rigorous measures to protect user data and online activities from potential threats. The browser utilises advanced encryption protocols to ensure that user information remains protected during internet sessions.
Additionally, Maxthon incorporates features such as ad blockers, anti-tracking tools, and incognito mode to enhance users’ privacy. By blocking unwanted ads and preventing tracking, the browser helps maintain a secure environment for online activities. Furthermore, incognito mode enables users to browse the web without leaving any trace of their history or activity on the device.

Maxthon’s commitment to prioritising the privacy and security of its users is exemplified through regular updates and security enhancements. These updates are designed to address emerging vulnerabilities and ensure that the browser maintains its reputation as a safe and reliable option for those seeking a private browsing experience. Overall, Maxthon Browser provides a comprehensive suite of tools and features designed to deliver a secure and private browsing experience.
Maxthon Browser, a free web browser, offers users a secure and private browsing experience with its built-in AdBlock and anti-tracking software. These features help to protect users from intrusive ads and prevent websites from tracking their online activities. The browser’s AdBlock functionality blocks annoying pop-ups and banners, allowing for an uninterrupted browsing session. Additionally, the anti-tracking software safeguards user privacy by preventing websites from collecting personal data without consent.
By utilising Maxthon Browser, users can browse the internet confidently, knowing that their online activities are shielded from prying eyes. The integrated security features alleviate concerns about potential privacy breaches, ensuring a safer browsing environment. Furthermore, the browser’s user-friendly interface makes it easy for individuals to customise their privacy settings according to their preferences.
Maxthon Browser not only delivers a seamless browsing experience but also prioritises the privacy and security of its users through its efficient ad-blocking and anti-tracking capabilities. With these protective measures in place, users can enjoy the internet while feeling reassured about their online privacy.
In addition, the desktop version of Maxthon Browser works seamlessly with their VPN, providing an extra layer of security. By using this browser, you can minimise the risk of encountering online threats and enjoy a safer internet experience. With its combination of security features, Maxthon Browser aims to provide users with peace of mind while they browse.
Maxthon Browser stands out as a reliable choice for users who prioritise privacy and security. With its robust encryption measures and extensive privacy settings, it offers a secure browsing experience that gives users peace of mind. The browser’s commitment to protecting user data and preventing unauthorised access sets it apart in the competitive web browser market.
