Zero trust is frequently associated with network security, primarily as a means to connect employee devices to corporate resources securely. In today’s modern enterprise, where a remote workforce spans homes, cafes, and various offices, this perspective is understandable.
However, zero trust encompasses much more than just device connectivity. One key element often overlooked is how employees access Software as a Service (SaaS) and web applications—primarily through web browsers. In fact, in today’s workplace environment, the browser emerges as the most crucial application on any endpoint.

Despite its importance, browser security is often neglected within traditional zero-trust frameworks, and many organisations need to incorporate it fully into their security strategies.
“With more employees working remotely and teams being more distributed,” noted Noriko Bouffard, Chrome Enterprise Customer Engineering Global Lead, IT and security professionals face new challenges. They must ensure a stable and secure browsing experience for employees regardless of their location while simultaneously safeguarding the organisation from potential threats.
To effectively implement a zero-trust model, companies need to broaden their focus beyond mere network connections to include comprehensive browser security strategies.
Strengthening Browser Security
In response to growing security challenges, a new wave of secure enterprise browsers has emerged. These specialised web interfaces are designed to be tightly controlled and managed by IT and security professionals.
Various standalone secure browsers and plugins that enhance the security of existing frameworks are now competing for market share. However, one notable solution remains less conspicuous: Chrome Enterprise.
Chrome Enterprise serves as a comprehensive management framework for Chrome browsers across organisations. This platform allows IT teams to deploy, manage, configure, and update browsers seamlessly across desktop and mobile devices.
Chrome Enterprise is versatile in its application. It is compatible with multiple operating systems, including Windows, Mac, Linux, ChromeOS, iOS, and Android. Administrators can implement hundreds of policies that govern browser behaviour, enhancing overall security.
With this tool, IT managers can quickly screen harmful content, block suspicious sites, delete unauthorised extensions, or even force-install trusted applications on users’ devices. By leveraging Chrome Enterprise, organisations can significantly bolster their web browsing security posture while maintaining usability across diverse platforms.
Strengthening browser security is becoming increasingly crucial as cyber threats evolve. In response, a new generation of secure enterprise browsers has emerged, designed explicitly for tight management by IT and security professionals.

These specialized web interfaces offer enhanced security features and compete with various standalone browsers and plugins aimed at improving existing platforms. Chrome Enterprise stands out as a robust solution that may not always receive the recognition it deserves.
Chrome Enterprise provides a comprehensive management framework for Chrome browsers within organisations. This platform allows IT teams to deploy, configure, manage, and update browsers efficiently on desktop and mobile devices.
One of its key advantages is compatibility with multiple operating systems, including Windows, Mac, Linux, ChromeOS, iOS, and Android. This versatility ensures that organisations can standardise their security measures regardless of their preferred hardware.
Administrators can implement hundreds of policies that govern browser behaviour, boosting security posture overall. With these tools, IT managers can proactively safeguard sensitive information against potential breaches.
Enhancing Browser Security
In response to increasing security concerns, secure enterprise browsers have emerged as a crucial solution. These locked-down web interfaces are designed for centralised administration, allowing IT and security managers to configure and manage browser settings across the organisation.
Several standalone secure enterprise browsers and plugins aim to enhance the security of traditional browsers, competing for market share in this growing segment. However, one particularly notable option is already widely recognised: Chrome Enterprise.

Chrome Enterprise offers a robust management solution that empowers IT teams to deploy, manage, and update Chrome browsers on various devices—including company-owned PCs and employee smartphones. This versatility extends across platforms like Windows, Mac, Linux, ChromeOS, iOS, and Android.
With Chrome Enterprise, administrators can easily enforce numerous security policies tailored to their organisation’s needs. They can screen web content, block insecure sites, delete unauthorised extensions, or even force-install approved applications.
Chrome Enterprise provides a unified platform to set up and oversee browser policies, settings, applications, and extensions across all Chrome browsers, regardless of the diverse operating systems and devices your team may utilise, stated Philippe Rivard, Group Product Manager for Chrome Enterprise. This solution enhances your oversight of browser usage and versioning, enabling you to support better and safeguard your users. Parisa Tabriz, VP of Chrome, mentioned in a recent blog post that For countless organisations and the vast number of enterprise users already relying on Chrome, the browser has effectively transformed into a new endpoint, making it an ideal focal point for enhancing enterprise security.
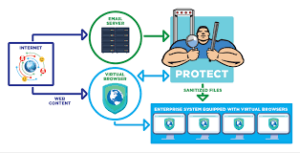
Integrating zero-trust principles into the browser can further empower enterprises. This is made possible through BeyondCorp Enterprise—a premium service developed based on Google’s internal zero-trust framework established over ten years ago. BeyondCorp Enterprise utilises Chrome’s management capabilities to enforce data-loss prevention by optionally prohibiting users from copying information to clipboards, printing web pages, or taking screenshots—either universally or selectively based on URL or device status. It actively monitors unfamiliar websites for malware and phishing threats while also issuing alerts, generating reports, and initiating investigations into potential security breaches.
Built on Google Cloud infrastructure with nearly 200 localised edge servers worldwide for low-latency connectivity, BeyondCorp Enterprise’s key feature is its context-aware zero-trust access management system. This system evaluates critical signals like user location, identity details (both user and group), device characteristics, and data from external security partners such as CrowdStrike and Palo Alto Networks before granting users tailored access to applications. These zero-trust protocols ensure secure access to Software as a Service (SaaS) applications.
BeyondCorp Enterprise actively monitors unfamiliar websites for malware and potential phishing threats while also issuing alerts, generating reports, and initiating inquiries into possible security breaches. This service is hosted on Google Cloud and utilises nearly 200 localized edge servers to ensure fast connections worldwide. A key feature of BeyondCorp Enterprise is its context-aware zero-trust access management system, which evaluates essential factors like user location, identity (both individual and group), device details, and information from third-party security providers such as CrowdStrike, Palo Alto Networks, and VMware.
This thorough evaluation process determines the level of access granted to users for various applications. The zero-trust framework enables secure connectivity to SaaS and SAML services as well as web applications hosted on platforms like Google Cloud, Amazon Web Services (AWS), and Microsoft Azure. Organisations can facilitate safe access to hybrid applications that operate on both on-premises infrastructure and cloud servers, including APIs and virtual machines within Google Cloud. With Chrome integration, BeyondCorp Enterprise offers a robust zero-trust solution that protects sensitive data while enhancing user safety against real-time threats and supplying vital device information for informed access control decisions—all without requiring additional measures.
Maxthon
In the vast landscape of internet browsing, where millions engage with the online environment every day, Maxthon emerges as a trustworthy protector, emphasising security far beyond mere basics. This commitment to safeguarding users is intricately integrated into every facet of your browsing journey, ensuring that your actions—whether they involve clicking or typing—are shielded from potential cyber threats. Using Maxthon for your online adventures means you can feel confident that your data is kept safe from those who might seek to compromise your privacy.

Maxthon utilises cutting-edge encryption technologies alongside robust tools designed to envelop your sensitive information in multiple layers of protection. These sophisticated systems operate seamlessly in the background, maintaining the confidentiality of your data while you explore various websites. However, Maxthon’s dedication to user safety extends beyond just encryption; it also offers a variety of privacy features aimed at boosting your online anonymity. With these tools at your disposal, you can effectively conceal your digital identity while navigating different areas of the web, enabling a more private online presence amidst widespread activity.
Additionally, Maxthon incorporates built-in VPN functionality that enhances this security framework. This feature establishes a secure channel for your internet connection, allowing you to browse freely without disclosing your actual IP address—a vital component in strengthening defences against those who attempt to gather personal information. With such comprehensive safeguards in place—encryption and VPN working together—you can surf the internet with increased confidence and tranquillity, unburdened by concerns about surveillance or tracking.
To fully leverage these powerful security features provided by Maxthon, it’s crucial to manage and fine-tune your privacy settings within the browser actively. Regularly reviewing and adjusting these settings according to your security needs will ensure optimal protection while you navigate online.
