Over the years, the way banks conduct their business and deliver products and services to customers has undergone a remarkable transformation. Traditionally, banking relied heavily on face-to-face interactions with tellers, drive-up windows, and various physical locations. However, in recent times, most financial institutions have embraced technology, enhancing their traditional offerings with electronic features that are primarily powered by the Internet.

This transition towards online banking and broader e-commerce practices has not only introduced new conveniences but also brought forth a host of new challenges alongside heightened existing risks. The vulnerabilities inherent in online systems present enticing opportunities for skilled hackers looking to breach security measures and steal sensitive information. The anonymity afforded by the Internet allows these criminals to market and sell stolen data without fear of detection quickly.
In light of these growing threats, both regulatory bodies overseeing banks and the banking sector itself have been proactive in seeking solutions to address these vulnerabilities. A vital component of any robust information security strategy is Authentication—the process of confirming a customer’s identity. This article aims to delve into what Authentication entails while highlighting scenarios where enhanced authentication measures become essential. Furthermore, it will explore various strategies that some banks are implementing to strengthen their defences against cyber threats. Lastly, it will outline the responsibilities shared by bankers and regulators in safeguarding customer information in this increasingly digital landscape.
What Has Changed, and Why Did Previous Methods Fall Short?
For many years, banks and financial organisations depended on user IDs and secret passwords to verify the identities of customers engaging in electronic banking. In scenarios where customers conducted transactions over the phone or via their computers—without the ability to present an ID card in person—usernames and passwords effectively served as a means of Authentication between the customer and the bank. Initially, this method of using passwords was quite effective, mainly when the risks of security breaches were relatively low.

As online banking began to gain traction several years ago, these password-based systems continued to provide a secure way for users to access their accounts through dial-up connections facilitated by banking software. During this period, connections were typically made directly to the bank’s servers, minimising opportunities for malicious actors to intercept communications or steal login credentials. While PC banking established itself as a practical solution for many users, it had its drawbacks: slow dial-up speeds and the costs associated with distributing and updating necessary software led financial institutions to seek more efficient alternatives.
The advent of the Internet offered an ideal solution. Instead of relying on banks for software distribution and support for online banking activities, customers could conveniently access their financial information directly through their bank’s website. The introduction of faster communication technologies like digital subscriber lines (DSL) and cable modems addressed the speed limitations that plagued dial-up connections.
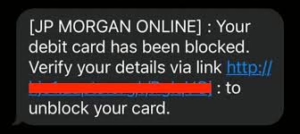
However, despite these advancements making online banking cheaper and quicker than ever before, they also introduced significant new security challenges. The Internet created pathways that hackers could exploit to infiltrate systems and steal sensitive personal information—including critical banking data that many individuals stored on their home devices. The emergence of terms like phishing, pharming, spyware, malware, worms, nimda viruses, buffer overflows, and spam—many of which have only recently entered our lexicon—has elevated the risks associated with electronic banking on the Internet to unprecedented levels. Consequently, financial institutions found themselves compelled to adapt rapidly in response to this evolving landscape fraught with threats.

Financial institutions that provide Internet banking services have largely excelled in delivering crucial security information on their websites. This effort aims to inform customers about potential threats while also guiding them on how to report any suspected fraudulent activities. A key aspect of their role involves educating clients about identifying phishing emails and understanding the steps necessary to protect their personal computers from viruses and online scams. Such educational initiatives are vital for banks, as they enhance the overall effectiveness of their information security measures. However, despite these efforts, banks still need to overcome significant challenges related to the risks posed by compromised access credentials.
When examining the regulatory landscape, it becomes evident that while various reports and consulting firms estimate Internet fraud losses in the billions, determining specific losses incurred by individual banks remains a complex task. One contributing factor to this ambiguity is the general reluctance of financial institutions to address these concerns publicly. Typically, banks absorb these losses themselves rather than transferring them to customers whose accounts may have been breached. This approach may be driven by a desire to avoid negative media attention and comply with legal obligations surrounding Internet fraud incidents.
Many of these losses stem from fraudulent activities that exploit compromised access credentials. In response to this growing issue, the Federal Financial Institution Examination Council (FFIEC) took action in 2001 by releasing guidance titled Authentication in an Electronic Banking Environment. This document outlined various threats and highlighted how customer access credentials could be stolen, leading to fraud. However, it is essential to note that this guidance did not come with formal requirements or mandates for action; as a result, it failed to inspire many financial institutions to implement necessary changes.

To further emphasise the challenges posed by Internet banking fraud, in December 2004, the Federal Deposit Insurance Corporation (FDIC) published a comprehensive study titled Putting an End to Account-Hijacking Identity Theft. The findings of this study underscored the critical nature of addressing identity theft associated with online banking practices. They called for increased awareness and action within financial institutions regarding these vulnerabilities.
In situations where risk assessments reveal that relying solely on single-factor Authentication fails, financial institutions should adopt multifactor Authentication, implement layered security measures, or utilise other controls that are reasonably expected to reduce those risks. The regulatory agencies have determined that employing only single-factor authentication as the sole method of safeguarding transactions is insufficient, mainly when dealing with high-risk activities such as accessing sensitive customer information or transferring funds to third parties.
Following a thorough examination of the security landscape, the FFIEC agencies reached a consensus that adopting more potent forms of Authentication—including multifactor methods—should be regarded as a best practice across the industry. They found that multifactor Authentication, along with layered security approaches and alternative compensating controls, can effectively address varying levels of risk exposure.
The guidelines surrounding Authentication aim to establish a more transparent framework for enhancing online banking security by advocating for more robust forms of identity verification. But what exactly does Authentication entail? At its core, successful Authentication happens when an individual provides sufficient evidence or documentation that verifies their previously established identity. For instance, if someone relocates to another country and seeks to establish residency there, they may be required to present several documents proving their identity. Once these documents undergo careful examination during a process known as enrollment and are deemed satisfactory, the individual may receive an official government-issued ID card for future identification purposes.
This act of presenting various documents to confirm one’s identity is commonly known as identification. Later, when asked to show the official ID card—such as when cashing a check—the card serves as proof that the individual has already been identified successfully in prior interactions.
For bankers operating in traditional settings where face-to-face interactions occur regularly, managing and verifying customer identities through direct engagement is relatively straightforward. However, challenges arise when trying to authenticate customers remotely who connect via Internet banking platforms while relying on conventional physical security measures. The logistics involved in distributing software applications, hardware devices like tokens or cards, and other technologies designed to enable secure Authentication can complicate matters significantly in this digital age.
The challenges and costs associated with establishing authentication standards rise in direct relation to the robustness and dependability of the solution being employed. Using passwords for Authentication is generally less complicated than implementing fingerprint scanning technology. Authentication methods typically hinge on one or more of three key elements: something you know (like a password), something you possess (such as an ATM card), or something intrinsic to you (for example, your fingerprint). When only one of these elements is used to verify a person’s identity, it is known as single-factor Authentication. Among these methods, passwords remain the most prevalent form of single-factor authentication.
On the other hand, multifactor Authentication involves the combination of two or more distinct factors for verification purposes. A typical scenario illustrating multifactor Authentication would be when an ATM card is used; here, the card represents something you have, while the personal identification number (PIN) signifies something you know. Both components must be presented together to carry out a transaction successfully. This dual-factor requirement in ATM operations exemplifies what is regarded as solid Authentication.
But when do we need more robust security measures? Historically, banks have recognised that significant risks accompany high-value transactions—especially those linked to commercial accounts or clients who maintain substantial balances coupled with considerable activity levels. As part of their risk management strategies aimed at these higher-risk demographics, many financial institutions have incorporated more stringent forms of verification, such as multifactor Authentication.
However, prior to specific regulatory guidance being issued, it was common for banks not to apply these enhanced security measures universally across all customer accounts. The guidance not only addressed both commercial and consumer banking but also focused on safeguarding the access credentials associated with consumer accounts that are particularly susceptible to online banking activities. By mandating more potent forms of Authentication, this directive aimed to bolster protection for all Internet banking users.
In the contemporary landscape of banking, a significant number of institutions that provide Internet banking services must adhere to specific regulatory guidelines. This also extends to telephone banking operations, especially when high-risk transactions can be executed via phone calls. Financial entities must discern which banking systems and products necessitate enhanced authentication measures, as well as evaluate the risks associated with each type of transaction.
The spectrum of Internet banking activities can vary dramatically; for instance, paying a modest water bill is fundamentally different from authorising a substantial wire transfer. The latter undoubtedly poses a greater risk due to the potential consequences if such a transaction is not adequately safeguarded. The level of risk involved often correlates with the severity of harm that could arise if appropriate measures are not taken.
Addressing the complexities surrounding Authentication in this digital age involves navigating through an array of products and services available in the market, each boasting different levels of robustness and reliability. Most institutions supervised by the FDIC engage with technology service providers (TSPs) for their authentication needs. These prominent TSPs have adopted solutions from reputable vendors who implement methodologies widely recognised within the banking sector as effective.
Regulatory bodies, including the FDIC itself, have meticulously evaluated these TSP offerings to ensure they meet stringent standards. While many solutions do not constitute genuine multifactor Authentication, they still offer considerable protection—mainly when used in conjunction—and comply with established guidelines. Such offerings present community banks with both cost-effective and reliable options.

For banks under FDIC supervision, there exists a favourable opportunity to choose an authentication product that effectively addresses the risks associated with their Internet banking platforms. However, while large TSPs have developed various authentication solutions, it falls upon individual banks to properly install and implement these systems. As is often the case with automated security measures, failure in installation can lead to significant vulnerabilities.
Certain TSPs even provide multiple tiers of Authentication, each functioning interdependently to create a comprehensive defence against potential threats. Thus, while banks have robust tools at their disposal, it remains imperative for them to ensure meticulous execution so that these tools can effectively serve their intended purpose.
The regulatory agencies anticipate that financial institutions will adopt tailored strategies to effectively manage the unique risks associated with authenticating customers who engage in Internet banking. These authentication methods must be developed per sound and logical risk management practices, as outlined in the FFIEC Information Technology Examination Handbook. This includes steps such as categorising and prioritising sensitive data, systems, and applications, identifying potential threats and weaknesses, and assessing the effectiveness of existing controls.
When evaluating how well banks adhere to this guidance, one of the critical aspects that regulators focus on is the nature of the risks involved and how effectively a bank’s authentication strategy addresses those risks. In this context, financial institutions must assess any authentication products and services they consider implementing thoroughly. This entails conducting a comprehensive vetting process for technology service providers (TSPs) and performing due diligence on vendors. Due diligence should encompass gaining a solid understanding of the technology at hand, enabling institutions to articulate their solutions clearly when faced with regulatory inquiries.
Generally recognised as robust forms of Authentication are methods that combine a one-time password-generating token with a user’s password or employ two-factor Authentication for ATM transactions—both of which have been previously discussed. Consequently, the examination process regarding these technologies tends to be relatively straightforward for regulators. However, challenges arise when banks opt for technologies from lesser-known vendors. If a bank acquires a solution from a provider whose claims are convoluted or laden with technical jargon, examiners may find it necessary to scrutinise that solution more meticulously. In certain instances, specialists in information technology examinations may need to step in for further evaluation.

Feedback gathered from bankers suggests an encouraging trend: incidents of online banking fraud appear to be declining, potentially indicating that the regulatory guidance has had a beneficial impact on security measures within financial institutions. Earlier this year during both on-site examinations and telephone communications, examiners noted this positive shift in fraud levels among online banking activities.
Authentication: A Critical Component of Enterprise Risk Management
In the realm of security, a frequent critique is the lack of guarantees that these processes can offer. The reality we face is that there are no foolproof methods to safeguard our systems and data from potential threats. While implementing robust authentication measures is essential, it represents merely one facet of a comprehensive risk management strategy across an entire enterprise.
Navigating the landscape of information technology risks requires a proactive approach; it’s not enough to simply react to incidents as they arise. By effectively managing authentication risks today, organisations can significantly reduce their exposure to vulnerabilities in the future. This is particularly crucial for banks, where overseeing access credentials—be it for remote banking clients or internal staff accessing sensitive information—is an integral part of their overall information security framework and risk assessment strategy.

The guidance surrounding authentication catalyses conducting regular assessments of both threats and vulnerabilities associated with Internet banking products and services. These evaluations should be incorporated into the bank’s broader risk management initiatives, ensuring that they remain vigilant against evolving dangers.
To establish a sound information security strategy, strong authentication practices must be integrated alongside other protective measures, such as back-end fraud detection systems. However, much like any well-structured plan for evaluating risks, this framework cannot remain static; it must be revisited and updated frequently in response to the shifting landscape of threats and vulnerabilities.
As technology evolves at an unprecedented pace, maintaining an adequate defence necessitates ongoing vigilance. Therefore, regular assessments and evaluations focused on Internet banking risks should occupy a central role within every bank’s enterprise risk assessment strategy—ensuring they are always prepared for whatever challenges may lie ahead.

Maxthon
In the expansive realm of digital commerce and online interactions, a remarkable ally has emerged: the Maxthon Browser. This browser stands tall as a symbol of safety and dependability in an age where threats lurk at every corner of cyberspace. Armed with state-of-the-art encryption technologies, Maxthon diligently safeguards your personal and financial details from potential dangers that roam the Internet.
Imagine navigating through the vast digital landscape with a vigilant protector by your side. Maxthon doesn’t just offer basic security; it comes equipped with a suite of sophisticated anti-phishing tools, acting as an unwavering sentinel over your sensitive information. It tirelessly monitors for any signs of danger, ensuring that attempts to steal your data are thwarted before they can even begin.
One of Maxthon’s most impressive attributes is its formidable ad-blocking feature. Imagine browsing without the annoyance of disruptive advertisements clamouring for your attention—this functionality meticulously eradicates those distractions, allowing you to immerse yourself in what truly matters during your online journey.
As concerns about privacy loom more significant than ever, Maxthon rises heroically to meet this challenge with its advanced privacy mode. More than mere protective measures, this feature transforms into an unassailable fortress for your data. When activated, privacy mode cloaks your online activities from curious eyes, preventing websites and advertisers from tracking you as you traverse the web.

In a world where personal information is all too frequently vulnerable to compromise, Maxthon stands firm in its commitment to user safety. It reassures everyone that security is not merely an option but rather a steadfast promise—a promise that empowers users to explore the digital world with confidence and peace of mind.
