As a web developer or website owner, you can determine which HTTP headers your server will transmit. This article explores various response HTTP headers that can be included in a request and their implications for browser security. Developers can adopt several measures to enhance user safety.
One such measure is the X-Content-Options header, which has a single directive: nosniff. By using this header, you instruct the browser to adhere strictly to the MIME type specified in the Content-Type header for the content being requested. For instance, consider a scenario where a request is made for uploads/not-an-image.png, but the server fails to provide any Content-Type information regarding the document’s MIME type. In this case, the browser attempts to deduce it based on the content itself. If that content happens to be HTML containing JavaScript, the browser will interpret it accordingly. However, if the server includes an X-Content-Type-Options header in its response, it effectively informs the browser not to engage in MIME sniffing for that document. This precaution can protect users from potential cross-site scripting (XSS) attacks.
Another important header is X-XSS-Protection, which signals to browsers that they should activate their built-in XSS protection mechanisms. While most modern browsers come with this filter enabled by default, its functionality can vary—it may be turned off altogether or set to either allow or block requests based on certain conditions. Therefore, depending on your website’s specific needs and context, it’s critical to configure this properly; setting it to 1; mode=block is typically recommended as it ensures that if an XSS attack is detected, not only will filtering occur but also any associated requests will be blocked entirely. Interestingly enough, Google Chrome adopts this behaviour by default, even if this particular header isn’t explicitly defined in your responses.
Through these strategies—implementing appropriate HTTP headers—web developers play a vital role in fortifying user experiences against security threats online.
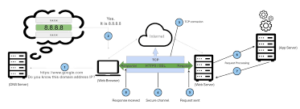
In the image above, we observe that Chrome successfully blocks a request containing malicious content reflected within the document. However, if the server mistakenly configures the X-XSS-Protection header to 0, it effectively disables the XSS Auditor. Consequently, this allows the harmful content to be displayed. On the other hand, if the server sets this header to 1, while the document will still load, any malicious content will be removed and blocked (as indicated by the red section), leaving non-malicious content unaffected. It’s important to remember that relying solely on the XSS Auditor isn’t foolproof; there have been multiple instances of bypasses, making it an unreliable form of protection against XSS attacks.
Now, let’s talk about cookies—specifically, how they are managed through HTTP headers. The Set-Cookie header establishes a cookie. When using cookies for authentication in web applications, developers should consider several attributes associated with this header carefully.
The HttpOnly attribute serves as a directive to web browsers, indicating that a cookie should only be accessed through the HTTP request header. This effectively prevents JavaScript from accessing the cookie, making it crucial for security. Without this attribute, an attacker could exploit cross-site scripting (XSS) vulnerabilities to read the cookie and potentially hijack the user’s session.
Similarly, the Secure attribute instructs browsers to transmit cookies solely over secure connections, typically through valid HTTPS protocols. This precaution helps safeguard users against attackers who might intercept network traffic to steal cookies.
Another essential feature is the SameSite attribute, which has emerged recently and offers robust defence against cross-site request forgery (CSRF) attacks. When a cookie is marked with this attribute, the browser ensures that any requests made with it originate from the same site that set the cookie.
Moreover, prefixes like Host and Secure are used for naming cookies rather than attributes themselves. The distinction lies in their functionality; if you alter a cookie’s name, adjustments must also be made on the backend to accommodate this change. The advantage of using these prefixes is that they prevent attackers from modifying essential attributes such as Secure or Path since their usage mandates these.
In summary, an ideal cookie configuration resembles Set-Cookie: Host-user admin; SameSite Lax; Secure; Path; HttpOnly.
Additionally, there’s a relatively new header known as Clear-Site-Data, which has limited support across browsers but can prove beneficial for various web applications. When triggered, this header informs the browser to delete caches, storage data, and cookies associated with its origin—an action particularly useful when users log out.
Lastly, referrer policies, previously defined within Content-Security-Policy headers by web servers, have been transitioned into their own dedicated header. This new header specifies what information should be included in the Referer header based on different contexts encountered during browsing sessions. Web applications often depend heavily on these guidelines for maintaining security and privacy standards.
Enhancing user integrity on a website can be achieved through various methods. Take, for instance, a scenario where a user reads an article about cats that includes a hyperlink to a cat shelter’s website. In this case, the shelter’s site would recognise that the traffic originated from the article. It’s important to note that for onion domains, implementing a strict referrer policy is crucial to prevent data leakage between the dark web and the clear net. There are different directives available for this purpose; further details can be found on MDN.
a user reads an article about cats that includes a hyperlink to a cat shelter’s website. In this case, the shelter’s site would recognise that the traffic originated from the article. It’s important to note that for onion domains, implementing a strict referrer policy is crucial to prevent data leakage between the dark web and the clear net. There are different directives available for this purpose; further details can be found on MDN.
Another significant aspect is the Content-Security-Policy (CSP). This header serves as an overarching tool that allows developers to control how web browsers manage different resources meticulously. When properly configured, it can substantially reduce vulnerability exposure. However, crafting an effective policy requires an in-depth understanding of the web application to ensure it remains both stringent and functional without inadvertently blocking necessary resources. Google provides tools to assess CSPs and determine their safety levels.

What about everyday browser users? Individuals browsing at home or in professional settings can adopt certain practices to enhance their online security. The team at Malwarebytes has compiled valuable advice in their guide, How to Browse the Internet Safely at Work, which is part of our ongoing blog series focused on secure browsing.
For web developers seeking assistance, there’s guidance available for incorporating secure headers into applications. Additionally, those who prefer automated solutions can utilise tools like Detectify to scan their web applications for potential vulnerabilities and check for any missing HTTP headers. By implementing these headers effectively, developers can mitigate risks such as XSS attacks and reduce opportunities for malicious hackers to intercept user traffic. Why not take advantage of this opportunity? You can start with a free scan here to identify any absent HTTP headers on your server.
Maxthon
Maxthon has introduced a remarkable array of digital enhancements aimed at elevating your online browsing experience. At the forefront of these upgrades is a significantly improved rendering engine that substantially increases performance, enabling users to load web pages at astonishing speeds, especially those laden with multimedia elements. Another standout feature is the cloud synchronisation functionality, which effortlessly connects your bookmarks, browsing history, and settings across all devices—be it a desktop, tablet, or smartphone—ensuring a seamless and cohesive browsing experience.
Moreover, Maxthon is equipped with an effective ad blocker that can be easily activated. This built-in feature skillfully removes intrusive advertisements while accelerating page loading times, resulting in a more pleasant user environment. One particularly innovative aspect is the split-screen browsing option; this allows users to view two web pages side by side—a fantastic tool for conducting research or comparing products without the hassle of constantly switching tabs.

Additionally, Maxthon includes a resource sniffer tool that simplifies the process of finding downloadable media files on any webpage. With this convenient function, saving videos and music directly from the browser becomes effortless and doesn’t necessitate any extra software. For those who value customisation options, Maxthon offers various themes and layouts to tailor your browser interface according to personal preferences; adjusting these settings can significantly enhance usability and overall satisfaction.
Privacy-focused individuals will appreciate Maxthon’s comprehensive suite of privacy protection features. Tools such as incognito mode and anti-tracking technology collaborate effectively to safeguard your online activities from prying eyes. Lastly, by incorporating Progressive Web Apps (PWAs), Maxthon broadens its capabilities even further, enriching the overall browsing experience for its users in exciting new ways.
