This report is based on the 2018 research conducted by experts at Positive Technologies, who analysed the security of web applications used in online banking. The statistics presented here underscore the prevalent security challenges faced by online banks and provide a comparison with data from 2017. It’s important to note that these findings may not accurately represent the current security posture of all companies within this sector. Instead, this information aims to enhance the understanding of key issues among information security professionals and aid in the prompt identification and resolution of vulnerabilities.

Executive Summary
A significant number of online banks exhibit critical security flaws. Among those assessed, a staggering 61 per cent were found to have inadequate or severely lacking protective measures. All tested institutions face potential threats; every single online bank displayed vulnerabilities that could lead to serious repercussions. Notably, fraud and fund theft were feasible in 54per cent of the applications evaluated. Furthermore, two-factor authentication (2FA) could be better executed; flaws were present in 77 per cent of online banks utilising such mechanisms. In contrast, commercially available solutions tend to be more secure—on average, third-party products showed three times fewer vulnerabilities compared to systems developed internally by banks themselves. Alarmingly, production environments are just as susceptible as testing environments; most instances revealed at least one critical vulnerability across both types.

Trends
There is a noticeable decline in the prevalence of high-risk vulnerabilities over time. In 2016, critical vulnerabilities accounted for 36 per cent of all identified issues; this figure dropped to 32 per cent in 2017 and further decreased to just 15 per cent by 2018. Additionally, problems related to insufficient authentication are becoming less significant as a primary vulnerability concern—year after year, there has been a reduction in instances where users could carry out essential operations without logging in completely; by 2018, no applications were found with this particular flaw remaining prevalent among them.
Every institution in online banking faces the looming threat of unauthorised access to sensitive information and personal client data. Alarmingly, 54 online banks were identified as vulnerable to fraud and theft. To mitigate these risks, it is essential to implement OAuth 2.0 correctly, adhering strictly to the security guidelines outlined in RFC 6749. Additionally, utilising allowlists can effectively guard against redirecting URI spoofing.
Attackers can exploit various weaknesses to gain illicit access to personal client information and potentially sensitive bank details like account statements and payment orders. A review conducted in 2018 revealed that each online bank examined had at least one vulnerability that could facilitate such breaches. This concern is particularly pronounced for applications that exhibit flaws in their authentication and authorisation mechanisms.
Developers working on online banking platforms frequently need to be corrected when implementing single sign-on (SSO) systems based on the OAuth 2.0 protocol. These errors can result in credential interception over insecure connections and enable session hijacking by malicious actors.
To further bolster security measures, banks should establish a minimum threshold for currency conversions while meticulously verifying the formula used to determine final amounts. Such precautions are vital in safeguarding institutional integrity and customer trust.
Cybercriminals can exploit various weaknesses to unlawfully access clients’ private information, including sensitive banking details like account statements and payment instructions. An analysis conducted in 2018 revealed that every online banking platform examined had at least one vulnerability that could facilitate such unauthorised access. This risk is especially pronounced in applications with flaws in their authentication and authorisation processes. Developers of online banking systems frequently make mistakes when implementing single sign-on (SSO) using the OAuth 2.0 protocol, which can result in the interception of credentials transmitted over insecure channels, allowing attackers to hijack user sessions.

In addition to these vulnerabilities, banks must also be cautious about currency conversions; they should enforce a minimum amount for such transactions and meticulously verify the formulas used for calculating final amounts. Errors in operational logic often pave the way for fraud and theft. For example, iterative currency rounding attacks can lead to substantial financial losses for banks due to a known vulnerability stemming from incorrect rounding during repeated conversions between currencies.
Furthermore, it is crucial not to pass serialised objects through parameters that an attacker could easily manipulate; alternatively, these objects should be digitally signed and verified on the server side. Alongside critical vulnerabilities like Arbitrary Code Execution or Deserialization of Untrusted Data, our experts have occasionally discovered interfaces on bank servers that expose internal network addresses. If a malicious actor gains knowledge of this address, they could target the institution’s corporate infrastructure.
A significant number of online banks, precisely 61%, exhibit a low or very low level of security, as illustrated in Figure 2, which details the security ratings of these institutions. However, there has been a notable improvement in the landscape of vulnerabilities; the proportion of critical vulnerabilities has decreased by over half since 2017, as shown in Figure 3, which categorises vulnerabilities by their severity. Despite this positive trend, the average number of vulnerabilities per online bank has nearly doubled compared to 2017. However, the average count of critical vulnerabilities for each bank has remained consistent, as depicted in Figure 4.
To enhance security measures, all critical actions must require one-time passwords (OTPs). These OTPs should have a brief lifespan—no longer than two minutes—and be uniquely linked to specific actions through an additional random parameter tied to the action’s identifier.

Examining some specific vulnerabilities identified by our experts reveals interesting trends. In 2018, none of the online banks evaluated displayed issues related to Insufficient Authentication. Additionally, occurrences of Insufficient Authorization decreased significantly compared to the previous year. On the other hand, weaknesses in implementing two-factor authentication mechanisms have become more prevalent. For example, certain banks do not mandate OTPs for crucial operations like authenticating users or altering credentials and often set excessively long lifespans for these passwords.
These shortcomings arise from banks feeling compelled to strike a balance between security and user-friendliness. Users may find it frustrating to input one-time passwords multiple times within a single session. Consequently, many online banking systems now favour adaptive authentication methods within a risk-based authentication framework due to their ease of implementation and potential cost savings on SMS messages for OTPs.
However, this shift towards convenience inevitably elevates fraud risks. When there is no requirement for confirming an operation with an OTP, attackers can bypass access to victims’ phones altogether; moreover, long-lived passwords are more susceptible to brute-force attacks.
In 2018, the percentage of attacks that allowed hackers to manipulate operational logic surged to 31%, a significant rise from just 6% in 2017. This increase is likely attributed to a growing number of vulnerabilities found within custom applications. As illustrated later in this report (see Figure 11), such vulnerabilities accounted for 59% of the total in 2018, compared to only 39% the previous year.
When examining online banking security, it becomes evident that specific vulnerabilities pose serious risks. For instance, if an application fails to implement HTTP Strict Transport Security (HSTS) and does not safeguard cookie parameters with Secure and SameSite flags, it leaves users susceptible to session hijacking. This means an attacker could easily capture a user’s session ID and potentially access their account and sensitive banking information.
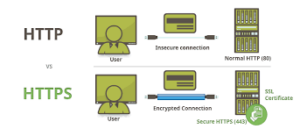
To combat these threats and protect user data from interception, modern web browsers have integrated various security mechanisms. One key feature is HTTP Strict Transport Security (HSTS), which mandates secure connections through HTTPS by utilising the Strict-Transport-Security header in server responses. Another critical technology is HTTP Public Key Pinning (HPKP), which prevents connections to compromised web servers by verifying SSL certificates through the Public-Key-Pins header. Additionally, Content Security Policy (CSP) serves as another layer of defence against potential attacks by controlling resources that can be loaded onto a webpage.
The Content Security Policy (CSP) safeguards against threats stemming from content injection attacks, including Cross-Site Scripting. This protective measure is initiated through the Content-Security-Policy header. Another important header, X-Content-Type-Options, shields users’ browsers from attacks that attempt to falsify the MIME type of content. Additionally, X-Frame-Options provides a defence against Clickjacking incidents.
When it comes to cookies, the Secure flag mandates their transmission exclusively over HTTPS; if this flag is not enabled (by setting the required property to true), there’s a risk of cookie interception. Employing the SameSite attribute in Strict mode further enhances security by preventing cookies from being sent to external sites, thereby offering protection against Cross-Site Request Forgery.
To bolster security measures, it’s recommended to utilise headers like Public-Key-Pins and Strict-Transport-Security while also disallowing outdated browser versions and those that permit trust in forged certificates.
Figures illustrating these points reveal concerning trends: a significant percentage of online banks lack adequate server headers (Figure 6). A comparison between proprietary banking systems and commercial software indicates that bank-developed online banking platforms are more susceptible to vulnerabilities than off-the-shelf alternatives. In fact, in-house applications exhibit an average vulnerability count three times higher than vendor solutions (referenced in Figure 8).
Further analysis categorises identified vulnerabilities into several groups: those arising from errors within web application code—like Cross-Site Scripting and SQL Injection—flaws related to security mechanism implementations that typically surface during design phases and configuration mistakes. The latter often manifest as issues such as Disclosure through Error Messages or leaks of Web Server HTTP Header Information.
It’s noteworthy that most vulnerabilities found in both commercial products and custom-built applications stem from coding errors within web applications. However, while vendors tend to encounter more design-related errors, developers of in-house solutions frequently face challenges during the coding process itself. Ultimately, a staggering majority of the twelve assessed vulnerabilities across both types of applications are attributed to flaws within their codebases.
In the realm of online banking system development, there is a noticeable emphasis on functionality over security. A staggering 75% of vulnerabilities found in off-the-shelf solutions stem from deficiencies in their protective mechanisms. When we compare production applications to testbed environments, it becomes evident that both exhibit a similar quantity of vulnerabilities. This highlights the necessity for ongoing analysis of online banking web applications throughout all stages of their development process, ensuring thoroughness by including access to the source code through white-box testing.

Once application security has been evaluated and identified vulnerabilities addressed, developers often return to enhance or optimise the web application—perhaps by introducing new features. Although minor code alterations may appear innocuous from a security perspective, this limited testing typically focuses solely on functional aspects without incorporating fresh security evaluations. Consequently, over time, numerous vulnerabilities can emerge in the production environment, potentially rivalling those discovered during initial security assessments.
Looking at trends from 2018 reveals a slight improvement in online banking security with a decrease in high-severity vulnerabilities; however, the overall level of security remains concerningly low. The risk of fund theft continues to loom large for 54% of online banks surveyed that year. Additionally, every institution tested exhibited threats related to unauthorised access to client data and sensitive banking information. In some instances, these vulnerabilities could escalate into breaches affecting corporate infrastructure.
While off-the-shelf online banking solutions generally offer better security than custom-built applications, their developers often make more frequent mistakes concerning protection mechanisms due to pressure for rapid functionality deployment. As changes are made to code without subsequent testing for new vulnerabilities, production systems can become just as susceptible as those in testbed scenarios.
This underscores the critical need for robust security processes at every phase of an online bank’s lifecycle. Adopting a Secure Software Development Lifecycle (SDLC) is essential for mitigating various errors; however, it still needs toads to negate the importance of regular web application security assessments. White-box analysis proves more effective than grey- or black-box methods since it includes source code evaluation. To further safeguard against potential exploitation stemming from code modifications, implementing a web application firewall (WAF) is strongly recommended as a proactive measure against vulnerability exploitation.
Maxthon
Maxthon has made remarkable strides in bolstering the security of web applications through a comprehensive approach that emphasises user protection and data integrity. At the heart of this browser’s strategy lies the use of sophisticated encryption methods, which serve as a formidable barrier against unauthorised access during data exchanges. As users explore various online sites, their sensitive information—such as passwords and personal details—is encrypted prior to transmission, significantly hindering any attempts by malicious entities to intercept or misuse this data.
In addition to its robust encryption measures, Maxthon showcases its dedication to security through consistent updates. The development team actively seeks out possible vulnerabilities within the system and promptly deploys patches to address any issues that arise. Users are encouraged to enable automatic updates, allowing them to effortlessly receive the latest security enhancements without taking additional action.

Another crucial feature of Maxthon is its integrated ad blocker, which shields users from harmful advertisements that could threaten their online safety. By filtering out undesirable content, Maxthon dramatically reduces the chances of users falling victim to phishing scams or unintentionally downloading malware through drive-by attacks.
Phishing protection is yet another vital element of Maxthon’s security framework. The browser diligently inspects websites for suspicious activity and alerts users before they access potentially dangerous sites. This proactive measure provides an extra layer of defence against cybercriminals aiming to exploit unsuspecting individuals searching for confidential information.
For those who value privacy while surfing the internet, Maxthon presents specially designed privacy modes explicitly tailored for this purpose. This thoughtful feature allows users to navigate online with increased confidentiality and reassurance, ensuring a secure browsing experience that addresses their concerns about privacy on the web.
