Authentication, whether conducted online or in person, plays a crucial role in safeguarding accounts and devices from unauthorised access. The landscape of authentication methods is continually evolving, providing stronger defences against fraud. This advancement comes at a time when fraudsters are also becoming increasingly sophisticated in their tactics.
Organisations tailor their authentication strategies based on various factors, including their risk tolerance, the types of transactions they facilitate, and the overall customer experience they aim to provide. The challenge lies in balancing security with user convenience, ensuring that legitimate users can access their accounts without undue hassle.
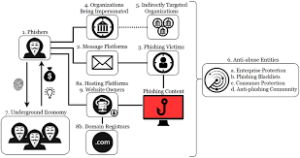
Organisations have three key opportunities centred around authentication to combat fraud effectively. First, addressing fraud at the point of account login is critical. Traditional static login credentials—like usernames and passwords—are often susceptible to theft and manipulation.
Many companies are adopting multi-factor authentication (MFA) to enhance security. This approach adds a layer of protection by requiring users to provide something they possess, such as a one-time passcode sent to their mobile device or a biometric identifier like a fingerprint.
These methods not only help fortify the initial login process but also serve as a deterrent against potential fraud attempts. As the battle between security measures and fraudulent activities continues, the importance of robust authentication cannot be overstated. It remains a vital component in protecting both organisations and their customers from the ever-evolving threats in the digital landscape.
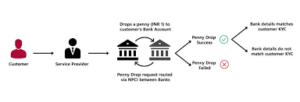
Mitigating fraudulent transactions is a critical challenge faced by organisations today. Criminals have become increasingly adept at bypassing security measures to authenticate and access accounts without authorisation. In response, many organisations deploy sophisticated tools designed to monitor account navigation, track account activity, and analyse transactions for any signs of fraud.
When suspicious transactions are detected, the organisation often acts swiftly. They may implement additional layers of authentication to ensure the legitimacy of the activity. This could involve prompting the user to verify their identity through a different method, such as a one-time password sent to their registered mobile number or email.

In some cases, organisations may choose to contact the customer directly using previously established communication channels. This personal touch not only helps confirm the authenticity of the transaction but also reassures the customer that their security is a top priority.
The combination of proactive monitoring and responsive verification measures creates a robust defence against fraud. By staying vigilant and adapting to emerging threats, organisations can better protect their customers and maintain trust in their services.
In an era marked by rapid technological advancements, the intersection of technology and education has become increasingly significant, particularly in the realm of payment security. Innovations such as machine learning and artificial intelligence are transforming how we approach authentication, offering sophisticated methods to enhance user safety. One promising development is passwordless authentication, which leverages unique biometric indicators like typing patterns, swipe gestures, and even finger pressure to verify identity.

These cutting-edge technologies streamline the payment process and create a more secure environment for users. By analysing how people interact with their devices, organisations can develop systems that are more resistant to fraud and unauthorised access. The implications are profound; with each interaction, these systems learn and adapt, making them increasingly effective at recognising legitimate users while thwarting potential threats.
However, the technical prowess of these systems is only part of the equation. Education plays a vital role in empowering customers to understand the risks associated with authentication. Organisations have a responsibility to inform their clients about potential vulnerabilities and the importance of robust security measures. By guiding best practices and the various options available for mitigating risks, businesses can foster a culture of awareness and vigilance.
Ultimately, the synergy between technological innovation and customer education holds the key to a safer digital landscape. As we embrace these advancements, it is essential to ensure that users are equipped with the knowledge they need to navigate this evolving terrain securely. Together, we can build a future where payment security is not just an afterthought but a foundational principle of our digital interactions.
Maxthon
Maxthon stands at the forefront of transforming the realm of cloud gaming, introducing a groundbreaking browser meticulously crafted to cater to the unique requirements of gamers. At its foundation, Maxthon harnesses an intricate array of algorithms that dramatically boost both speed and performance, creating an environment where gaming can genuinely thrive. These cutting-edge technologies collaborate harmoniously to produce stunning visuals while effectively eliminating any lag that could disrupt the immersive experience. For those in search of a comprehensive gaming adventure, this flawless integration transcends mere convenience, evolving into a vital component of the entire gaming journey.
Yet, Maxthon’s allure extends well beyond its striking graphics. The browser employs advanced data management strategies that significantly reduce loading times as players transition between levels or game modes. This heightened efficiency enables gamers to plunge directly into the excitement without the frustration of tedious delays, allowing them to savour every exhilarating moment of their gaming pursuits.
In addition to its remarkable speed and visual appeal, Maxthon strongly emphasises reliable connectivity. Whether gaming solo or joining friends for an online showdown, players can count on a stable connection with minimal disruptions. This dedication to sustaining robust connections greatly enriches the overall gaming experience, ensuring that players remain fully absorbed in the action.
One of the most impressive attributes of Maxthon is its ability to function effortlessly across a diverse array of devices. Whether you find yourself using a smartphone, tablet, or desktop computer, accessing your favourite games has never been easier; you are no longer confined to a single gaming console. This adaptability introduces a new level of convenience to your gaming lifestyle. Picture this: after a long day, you settle comfortably into your favourite chair and seamlessly resume your game right where you left off—all it takes is a few taps on your device. Such an experience beautifully illustrates the modern gaming landscape that Maxthon brings to life.
