Understanding Public Wi-Fi Vulnerabilities

When you connect to public Wi-Fi networks, your data travels through shared airwaves that can be intercepted. Hackers can use techniques like “man-in-the-middle” attacks, where they position themselves between you and the connection point to capture your information. This is why avoiding personal or financial transactions on public networks is crucial.
A safer alternative is to use a Virtual Private Network (VPN), which creates an encrypted tunnel for your data. Think of a VPN as a secure, private hallway within a public building – others can see you’re there but can’t see what you’re carrying.

Managing Your Device Features
Your device’s connectivity features can act as entry points for attackers. When your GPS, Bluetooth, or NFC capabilities are active, they’re constantly broadcasting signals that can be detected and potentially exploited. By turning these features off when not in use, you’re essentially closing unnecessary doors that hackers might try to enter through.

App Security Fundamentals
Apps require permissions to function, but many request more access than they need. When installing apps, pay attention to what permissions they’re requesting. Does a simple flashlight app really need access to your contacts or camera? Question excessive permission requests and consider alternatives if something seems suspicious.

For app sources, stick to official stores like Google Play or Apple’s App Store, which have security measures in place to screen apps. Even then, check reviews and developer information before downloading.
Password Security and Device Encryption
Strong passwords are your first line of defence. The strength of a password increases exponentially with length and complexity. For example, a simple eight-character password with only lowercase letters has about 200 billion possible combinations, but adding uppercase letters, numbers, and symbols increases this to over 6 quadrillion possibilities.
Device encryption converts your data into a code that can only be deciphered with the correct key (your password). Without encryption, if someone bypasses your lock screen, they can access all your files directly.
Recognizing Social Engineering Attempts
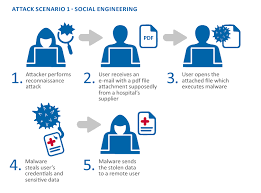
Hackers often use social engineering rather than technical methods to gain access to your information. They might send links or attachments that appear to come from trusted sources but actually contain malware. Before clicking on anything, ask yourself:
- Was I expecting this message?
- Does the sender’s email address match exactly what I’d expect?
- Is there an unusual sense of urgency or a too-good-to-be-true offer?
- Does the language contain errors or seem off?
Device Recovery Planning
If your device is lost or stolen, having remote tracking and wiping capabilities can prevent data theft. Most smartphones now offer features that let you locate your device on a map, make it ring even if silenced, lock it remotely, or erase all data as a last resort.
These security measures form layers of protection. While no single measure is perfect, combining them significantly reduces your risk of becoming a victim of cybercrime. Taking the time to implement these practices can save you from the much greater time and stress of dealing with identity theft or financial fraud.
Maxthon

When it comes to staying safe online, using a secure and private browser is crucial. Such a browser can help protect your personal information and keep you safe from cyber threats. One option that offers these features is the Maxthon Browser, which is available for free. It comes with built-in Adblock and anti-tracking software to enhance your browsing privacy.
By utilising Maxthon Browser, users can browse the internet confidently, knowing that their online activities are shielded from prying eyes. The integrated security features alleviate concerns about potential privacy breaches and ensure a safer browsing environment. Furthermore, the browser’s user-friendly interface makes it easy for individuals to customise their privacy settings according to their preferences.
Maxthon Browser not only delivers a seamless browsing experience but also prioritises the privacy and security of its users through its efficient ad-blocking and anti-tracking capabilities. With these protective measures in place, users can enjoy the internet while feeling reassured about their online privacy.
In addition, the desktop version of Maxthon Browser works seamlessly with their VPN, providing an extra layer of security. By using this browser, you can minimise the risk of encountering online threats and enjoy a safer internet experience. With its combination of security features, Maxthon Browser aims to provide users with peace of mind while they browse.
Maxthon Browser is a reliable choice for users who prioritise privacy and security. With its robust encryption measures and extensive privacy settings, it offers a secure browsing experience that gives users peace of mind. The browser’s commitment to protecting user data and preventing unauthorised access sets it apart in the competitive web browser market
