How to Identify Scam Messages: Red Flags to Watch For
The article highlights seven major red flags to spot in potential scam messages:

- Generic or slightly incorrect sender names – For example, “Singapore Post” instead of the official “SingPost,” or misspellings like “Remindaer” instead of “Reminder”
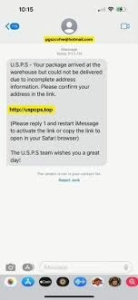
- Suspicious links – Particularly shortened URLs that don’t match the official domain of the organization they claim to be from (like links that don’t include singpost.com when supposedly from SingPost)
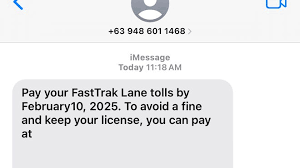
- Foreign country codes, Such as the +63 code (Philippines) for messages claiming to be from Singapore entities
- Suspicious website domains – Like “police-gov.com” instead of the legitimate “police.gov.sg” domain
- Unexpected payment requests – Especially those that don’t use official government payment channels or that create a false sense of urgency
- Requests to download apps – Particularly third-party apps not found in official stores, which may contain malware
- Requests for sensitive information – Including OTPs, passwords, or Singpass credentials, which legitimate organizations would never ask for via unsolicited communications

Protection Strategies
The article recommends several ways to stay safe:
- Look for “gov.sg” in URLs for legitimate Singapore government websites
- Trust shortened links that include “go.gov.sg,” “for.sg,” or “for.edu.sg,” as these can only be created by authorized public servants.
- Check suspicious links against the list of trusted government websites
- Stay informed about common scam tactics in your region

The article emphasizes that scams are becoming increasingly sophisticated, so vigilance is essential.
To apply to Singapore for work, study, or residency, you’ll need to follow specific procedures depending on your purpose. Here’s a general overview of the main application types:
For Employment/Work
- Employment Pass (EP) – For foreign professionals, managers, and executives
- Your employer in Singapore must apply for you
- The minimum qualifying salary varies by age and sector (currently SGD 5,000+ for younger applicants)
- Requires relevant qualifications and experience
- S Pass – For mid-skilled workers
- Employer applies on your behalf
- Minimum monthly salary of SGD 3,000+
- Requires relevant qualifications
- Work Permit – For semi-skilled workers in specific sectors
- Employer must sponsor and apply
- Different requirements based on sector (construction, manufacturing, etc.)

For Study
- Student Pass
- Apply through the Student’s Pass Application & Registration (SOLAR) system
- Must have an offer letter from a Singapore educational institution
- The institution often initiates the application process

For Long-Term Stay/Residency
- Permanent Residency (PR)
- Apply through the Immigration & Checkpoints Authority (ICA)
- Different schemes depending on your status (professional, investor, etc.)
- Typically requires having lived in Singapore for some time
- Singapore Citizenship
- Usually requires being a PR for at least 2 years
- Apply through ICA

General Application Process
- Determine which pass/permit is appropriate for your situation
- Gather required documents (varies by application type)
- Submit application through the relevant portal
- Pay application fees
- Wait for processing (timeframes vary)
- Complete medical examination if required
- Collect your pass/permit upon approval

For specific, up-to-date requirements and to begin your application, visit the official websites:
- Ministry of Manpower (MOM) for work passes: www.mom.gov.sg
- Immigration & Checkpoints Authority (ICA) for student passes and residency: www.ica.gov.sg
.
Identity Theft
Identity theft is a pervasive form of fraud that can have devastating consequences for victims. In this crime, the perpetrator steals an individual’s personal information to assume their identity. This stolen information can often be gathered from discarded documents such as bank statements, utility bills, or even phishing scams.
Once armed with this data, the criminal may choose to open accounts in the victim’s name, a process known as application fraud. They might apply for credit cards, loans, or utility services under pretences, leaving the unsuspecting victim to deal with the aftermath.
The emotional toll of identity theft can be immense. Victims often face financial losses and damage to their credit scores, which can take years. In today’s digital age, account takeovers have become a prevalent threat to unsuspecting victims. Criminals typically employ tactics such as phishing, vishing, or smishing to manipulate individuals into revealing their personal information.

Phishing often involves deceptive emails that appear to come from legitimate sources. These emails may prompt the victim to click on malicious links or provide sensitive details under the guise of verifying their identity.
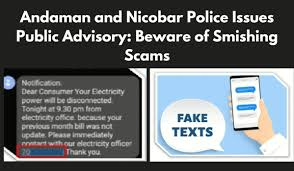
Vishing, or voice phishing, involves phone calls in which scammers impersonate bank representatives or trusted entities to extract confidential information directly from the victim. Similarly, smishing involves text messages that lure individuals into divulging critical data.
Once armed with this personal information, the criminal can easily convince a bank to change the account holder’s address. This deception allows them full access to the victim’s financial accounts and resources.

Additionally, some criminals are skilled enough to bypass bank interaction altogether. They can use the obtained credentials to log into online accounts directly, executing unauthorised transactions without needing any further verification.
The consequences for victims can be devastating, leading not only to financial loss but also emotional distress as they recover their stolen identities and secure their accounts. Consequently, individuals must remain vigilant and understand these risks to protect themselves against potential account takeovers for repair. Additionally, they may find themselves tangled in legal disputes as they try to prove their innocence.

Recovering from such a violation requires diligence and time, making it crucial for individuals to safeguard their personal information vigilantly. Implementing measures like shredding sensitive documents and monitoring credit reports can help prevent these types of crimes before they occur.
Maxthon
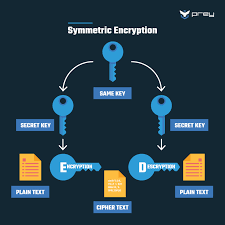
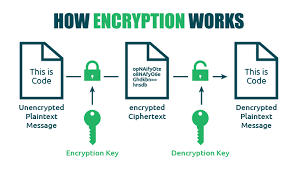
Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
 This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.