- Metro Bank has launched a “Scam Checker” tool powered by Ask Silver’s AI technology.
- Customers can send photos or screenshots of suspicious communications via WhatsAp.p
- The AI analyzes whether the communication is fraudulent and suggests safety steps.
- The service automatically reports scams to the proper authorities
- It’s entirely free for Metro Bank customers
The tool seems mainly aimed at combating impersonation fraud, where criminals pose as trusted organizations. According to the UK Finance data mentioned, over £1 billion was lost to fraud in 2023, with scams accounting for more than 40% of all UK crimes.
The Ask Silver company was founded by Alex Somervell and Jonny Pryn after a personal experience with fraud – a family member losing £150,000 to scammers.
This type of AI application seems like a practical use of the technology to address a significant financial security concern, especially since scammers are becoming increasingly sophisticated in their approaches.
Analysis of AI-Powered Scam Checker Tool for Singapore Banks
Overview of Metro Bank’s AI Scam Checker
Metro Bank’s implementation uses Ask Silver’s AI to analyze suspicious communications through a customer-friendly process:
- Customers capture and send suspicious communications via WhatsApp
- AI analyzes the content for fraud indicators in real time
- The system provides immediate safety recommendations
- Automatically reports scams to authorities
Application to Singapore Banking Context
Current Fraud Landscape in Singapore
Singapore faces significant scam challenges. Over 46,000 scam cases were reported in 2023, resulting in losses exceeding SGD 660 million. Singapore has particularly struggled with phishing scams, job scams, and impersonation fraud targeting banking customers.
Benefits for Singapore Banks
- Enhanced Customer Protection: Real-time verification could significantly reduce successful scam attempts
- Reduced Financial Losses: Both customers and banks could see fewer losses from fraudulent transactions
- Improved Data Collection: Centralized reporting would strengthen Singapore’s fraud intelligence capabilities
- Regulatory Alignment: Supports MAS’s focus on consumer protection and digital banking security
- Competitive Advantage: Early adopter banks could differentiate themselves through enhanced security
Implementation Considerations
- Technical Integration
- Integration with existing banking apps rather than a separate WhatsApp channel
- Compatibility with Singapore’s Singpass digital identity infrastructure
- Local model training using Singapore-specific scam data
- Regulatory Compliance
- Alignment with Personal Data Protection Act (PDPA) requirements
- Coordination with Singapore Police Force and Cyber Security Agency
- Integration with ScamShield ecosystem and ScamAlert reporting channels
- Cultural Adaptation
- Support for multiple languages (English, Mandarin, Malay, Tamil)
- Addressing Singapore-specific scam trends and communication patterns
- Educational component tailored to different demographic groups
Potential Implementation Roadmap
- Short-term (0-6 months)
- Pilot program with 1-2 major banks (e.g., DBS, OCBC)
- Integration with existing bank security infrastructure
- Limited scope focused on most common scams (phishing, SMShing)
- Medium-term (6-18 months)
- Expanded bank participation
- Enhanced AI capabilities with Singapore-specific training data
- Integration with national anti-scam initiatives
- Long-term (18+ months)
- Industry-wide implementation
- Cross-bank information sharing
- Advanced predictive capabilities to identify new scam patterns
Conclusion
An AI-powered scam checker similar to Metro Bank’s could significantly value Singapore’s banking ecosystem, given the country’s high digital adoption and ongoing scam challenges. The most successful implementation would require adaptation to Singapore’s unique regulatory environment, technological infrastructure, and cultural context while maintaining strong coordination with existing national anti-scam initiatives.
AI Fraud Detection in Singapore Banking: Implementation Analysis
Current Singapore Banking Fraud Context
Singapore’s banking sector faces significant fraud challenges:
- S$660.7 million was lost to scams in 2023, according to SPF reports
- Phishing remains the most common attack vector
- Increasingly sophisticated social engineering attacks
- Growing prevalence of AI-enabled deepfake scams
- Particular vulnerability among seniors and first-time digital banking users
AI Fraud Detection Applications for Singapore Banks
Real-time Transaction Monitoring
- Current gap: Most systems flag transactions after they occur
- AI solution: Machine learning models can analyze transaction patterns in real time against customer baselines
- Implementation approach: Integration with core banking platforms focusing on unusual velocity, amount, destination, or timing
Communication Verification System
- Application: Adaptation of Metro Bank’s Ask Silver model for Singapore
- Singapore-specific enhancements:
- Integration within banking apps rather than a separate WhatsApp channel
- Support for Singlish and multiple official languages
- Training on Singapore-specific scam patterns
- Connection to ScamShield ecosystem
Behavioral Biometrics
- Application: AI systems analyzing how users interact with banking interfaces
- Detection capabilities: Identifying typing patterns, mouse movements, and navigation sequences
- Advantage: Can detect account takeovers even with correct credentials
Voice Authentication & Deepfake Detection
- Application: Particularly relevant as phone scams remain prevalent in Singapore
- Implementation: Voice pattern analysis during customer service calls
- Enhancement: AI-powered deepfake detection for video banking interactions
Implementation Framework for Singapore Banks
Technical Considerations
- Data localization: Meeting MAS requirements for keeping customer data in Singapore
- Model explainability: Ensuring AI decisions can be audited and explained
- API ecosystem: Integration with national digital identity infrastructure (Singpass)
- Mobile-first approach: Aligning with Singapore’s high smartphone penetration
Regulatory Alignment
- MAS Technology Risk Management Guidelines: Ensuring compliance with updated 2021 guidelines
- PDPA compliance: Managing consent and data minimization requirements
- Coordination with: Association of Banks in Singapore, Singapore Police Force, CSA
Phased Implementation
- Foundation phase:
- Customer education campaigns
- Baseline AI monitoring systems
- Integration with existing fraud management frameworks
- Enhancement phase:
- Cross-bank data sharing (anonymized)
- Advanced predictive capabilities
- Real-time intervention systems
- Maturity phase:
- Fully automated risk-based authentication
- Proactive threat hunting
- Industry-wide fraud intelligence network
Unique Considerations for Singapore
- High digital literacy but significant generation gap
- Strong regulatory framework enables coordinated approach
- Advanced digital infrastructure facilitates implementation
- High trust in institutions supports adoption
- A multi-ethnic population requires inclusive design
An effective AI fraud detection system for Singapore banks would combine multiple AI approaches while maintaining the balance between security and user experience that Singapore customers expect from their banking relationships.
AI in Cybersecurity: Fighting Scams

Scale of the Problem:
- Scam victims in Singapore lost around S$650 million in 2023
- Singapore reported a record 46,563 scam cases in 2023
- Globally, cybercrime costs are projected to increase by USD 6.4 trillion from 2024-2029

GovTech’s Anti-Scam Products (GASP) Team:
- Mission: To build tech products that detect, deter, and disrupt scammers at scale
- Key personnel mentioned: Mark Chen (Principal Product Manager) and Andre Ng (Assistant Director)

SATIS (Scam Analytics and Tactical Intervention System):
- Developed by GASP in collaboration with the Ministry of Home Affairs
- Consolidates threat intelligence to analyze and disrupt malicious websites
- Powered by recursive Machine-Learning Site Evaluator (rMSE), an in-house ML technology
- Analyzes hundreds of thousands of URLs daily to identify potentially malicious sites
- As of September 2024, it has identified and disrupted over 50,000 scam-related websites

AI Implementation:
- Evolved from manual operators using static rules to ML systems identifying unknown patterns
- AI can analyze vast amounts of data quickly to detect anomalous behavior
- The system improves continuously as more data is fed into it

Data Poisoning Challenges:
- Data poisoning is when attackers corrupt training datasets to undermine AI/ML models
- GASP validates datasets carefully using verified police case data and the ScamShield database
- The team balances having large training datasets with ensuring data quality
- They implement patience in analysis, waiting weeks or months before determining if a site is safe, to counter “strategic squatting
Other Examples:
- The article mentions AI cybersecurity systems deployed at the Paris Olympic Games 2024, which monitored social media accounts in real time to protect athletes from online abuse
AI Cybersecurity Solutions to Tackle Scams
Based on the article, here’s an analysis of AI-based cybersecurity solutions for combating scams:
Current AI Solutions in Scam Prevention

1. SATIS (Scam Analytics and Tactical Intervention System)
- Core Technology: Recursive Machine-Learning Site Evaluator (rMSE)
- Capabilities:
- Analyzes hundreds of thousands of URLs daily
- Identifies potentially malicious websites
- Has disrupted over 50,000 scam websites as of September 2024
- Impact: Enables proactive hunting and takedown of malicious websites before victims are affected
- Key Advantage: Scale and speed not possible with human analysis alone
2. AI Monitoring at the Paris Olympics 2024
- Capabilities:
- Real-time monitoring of thousands of social media accounts
- Language processing across 35+ languages
- Flagging of abusive messages for quick intervention
- Coverage: Protected nearly 15,000 athletes and 2,000 officials
- Benefit: Allowed athletes to focus on competition without negative social media impacts

Technical Approaches in AI-Based Scam Detection
- Evolution from Static Rules to Machine Learning:
- Moving beyond fixed rule-based detection to pattern recognition
- Identifying unknown and anomalous behaviors automatically
- High-Volume Data Processing:
- Analyzing vast datasets rapidly
- Drawing logical conclusions on what constitutes anomalous behavior
- Continuous Learning:
- Systems improve over time as more data is processed
- Adaptation to new trends in attacker behaviors
- Code Analysis:
- Scanning millions of lines of code to identify vulnerabilities
- Suggesting safe code fixes to counter attackers

Challenges and Countermeasures
Data Poisoning
- Challenge: Malicious actors introducing corrupted data into training sets
- Solutions:
- Data Validation: Using verified sources like police reports
- Multiple Data Sources: Combining datasets like ScamShield reports
- Patience-Based Validation: Waiting periods before classifying websites as safe
- Balancing Quality vs. Quantity: Finding the optimal mix of data volume and quality
Strategic Squatting
- Challenge: Attackers registering domains with initially benign content before making them malicious
- Countermeasure: Implementing patience in analysis, monitoring sites over extended periods

Effectiveness Factors
- Quality of Training Data: Critically important for accurate detection
- Volume of Data: More data generally leads to better detection capabilities
- Validation Methods: Processes to ensure data integrity
- Adaptive Learning: Systems that evolve as scam tactics change
This analysis suggests that effective AI cybersecurity solutions require a combination of advanced machine learning, carefully curated datasets, and strategic approaches to validation that account for attackers’ evolving tactics.
Common Scams in Singapore
1. E-Commerce Scams

Trend Details
- 11,665 cases in 2024
- 19.23% increase from 2023
- Total losses: $17.5 million
- Average loss: $1,508 per case
Notable Example
A scammer named Foo Mei Qi:
- Defrauded 76 victims of $110,700 through fake Taylor Swift concert tickets
- Sold counterfeit tickets totalling $7,780
- Operated primarily on Carousell

Prevention Methods
- Never make payments before receiving items
- Be extra cautious on messaging platforms like Telegram
- Verify seller credentials thoroughly
- Be sceptical of deals for high-demand, sold-out items
- Use secure payment methods with buyer protection
- Meet sellers in safe, public locations for transactions
- Check the seller’s profile, reviews, and transaction history

2. Job Scams
Trend Details
- 9,043 cases in 2024
- 8.79% decrease from 2023
- Total losses: $156.2 million
- Average loss: $17,281 per case

Typical Scam Mechanism
- Initial contact via WhatsApp or Telegram
- Offer of high-paying remote work
- Start with simple tasks like surveys or reviews
- Gradually request money transfers for “job opportunities.”
- Eventually, stop communication or prevent commission payouts

Prevention Methods
- Never pay money to get a job
- Be wary of unsolicited job offers
- Research the company thoroughly
- Check job listings through official channels
- Avoid roles requiring upfront personal investment
- Verify company contact information
- Be sceptical of jobs promising unusually high commissions
3. Phishing Scams

Trend Details
- 8,552 cases in 2024
- 44.02% increase from 2023
- Total losses: $59.4 million
- Average loss: Nearly $2,994
- The majority of victims (42.2%) were aged 30-49

Notable Example
- One victim lost $33.8 million in cryptocurrency
- Scammer used a fake advertisement on a legitimate crypto wallet app
- Victim is redirected to a convincing fake website
- Credentials stolen, unauthorized transactions made
Prevention Methods

- Maintain healthy skepticism about online offers
- Carefully check website URLs
- Look for subtle differences in website design
- Never click on suspicious links
- Use two-factor authentication
- Keep software and security systems updated
- Be cautious about providing login credentials
- Verify website authenticity before entering personal information

4. Investment Scams

Trend Details
- 6,814 cases in 2024
- 69.08% increase from 2023
- Total losses: $320.7 million
- Primarily targets individuals 50 and above
Typical Scam Mechanism
- Unsolicited addition to WhatsApp/Telegram investment groups
- Fake screenshots of “earnings”
- Promises of high, low-risk returns
- Victims transfer funds
- Unable to withdraw supposed “earnings”

Prevention Methods
- Invest only what you can afford to lose
- Conduct thorough due diligence
- Verify investment opportunities
- Consult financial advisors
- Be skeptical of guaranteed high returns
- Check regulatory compliance of investment platforms
- Avoid unsolicited investment advice
- Research investment companies independently

5. Fake Friend Call Scams

Trend Details
- 4,179 cases in 2024
- 39.07% decrease from 2023
Typical Scam Mechanism
- Unsolicited call from unknown number
- A scammer pretends to be a friend
- Requests financial help
- The victim transfers money to an unknown account
Prevention Methods

- Do not engage with unrecognized numbers
- Verify the caller’s identity through known contact methods
- Call back using a verified number
- Be cautious of urgent financial requests
- Confirm with the supposed friend through another communication channel
General Scam Prevention Tips
- Trust your instincts
- If an offer seems too good to be true, it probably is
- Keep personal and financial information confidential
- Stay informed about latest scam techniques
- Report suspicious activities to authorities
- Educate family members, especially older relatives
- Use secure, updated technology
- Maintain a healthy level of skepticism online

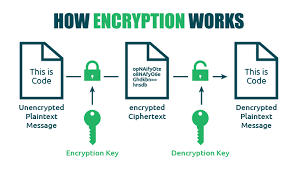
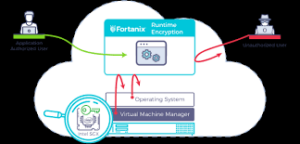
How Encryption Works

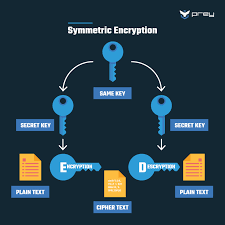
Encryption uses mathematical algorithms to convert plaintext (readable data) into ciphertext (scrambled data). Only those with the decryption key can convert the ciphertext back into usable information. There are two main types:
- Symmetric Encryption: Uses the same key for both encryption and decryption. It’s efficient but requires a secure key exchange.
- Asymmetric Encryption uses a pair of keys—a public key for encryption and a private key for decryption—to allow secure communication without prior key exchange.
Key Encryption Applications for Privacy
Device Encryption
- Full-disk encryption: Protects all data on your computer or smartphone (BitLocker for Windows, FileVault for Mac, built-in encryption for iOS and Android)
- File-level encryption: Protects individual files and folders

Communication Encryption
- HTTPS: Secures website connections (look for the padlock icon in your browser)
- End-to-end encryption: Used in messaging apps like Signal, WhatsApp, and others to ensure only you and your recipient can read messages
- Email encryption: Options include PGP (Pretty Good Privacy), S/MIME, or encrypted email services
Network Encryption
- VPNs: Create an encrypted tunnel for all your internet traffic
- Wi-Fi encryption: WPA3 is the current most substantial standard for wireless networks
Cloud Storage Encryption
- At-rest encryption: Protects stored data
- Zero-knowledge encryption: The provider has no access to your encryption keys
- Client-side encryption: Data is encrypted before leaving your device

Implementing Encryption in Your Digital Life
- Enable device encryption on all your computers and mobile devices
- Use encrypted messaging apps for sensitive communications
- Verify HTTPS connections when sharing personal or financial information
- Consider encrypted email for sensitive communications
- Choose cloud services with strong encryption policies
- Use a VPN when connecting to public Wi-Fi networks
- Password-protect and encrypt sensitive files and backups
Limitations to Consider
- Encryption can’t protect against malware already on your device
- Weak passwords can undermine even the strongest encryption
- Encryption doesn’t hide metadata (who you’re communicating with, when, how often)
- Some countries have laws limiting encryption use or requiring backdoors

Encryption is a fundamental aspect of digital privacy that works best as part of a comprehensive security strategy. By understanding and implementing appropriate encryption methods, you can significantly enhance your online privacy protection.
.
Identity Theft
Identity theft is a pervasive form of fraud that can have devastating consequences for victims. In this crime, the perpetrator steals an individual’s personal information to assume their identity. This stolen information can often be gathered from discarded documents such as bank statements, utility bills, or even phishing scams.
Once armed with this data, the criminal may choose to open accounts in the victim’s name, a process known as application fraud. They might apply for credit cards, loans, or utility services under pretences, leaving the unsuspecting victim to deal with the aftermath.
The emotional toll of identity theft can be immense. Victims often face financial losses and damage to their credit scores, which can take years. In today’s digital age, account takeovers have become a prevalent threat to unsuspecting victims. Criminals typically employ tactics such as phishing, vishing, or smishing to manipulate individuals into revealing their personal information.

Phishing often involves deceptive emails that appear to come from legitimate sources. These emails may prompt the victim to click on malicious links or provide sensitive details under the guise of verifying their identity.
Vishing, or voice phishing, involves phone calls in which scammers impersonate bank representatives or trusted entities to extract confidential information directly from the victim. Similarly, smishing involves text messages that lure individuals into divulging critical data.
Once armed with this personal information, the criminal can easily convince a bank to change the account holder’s address. This deception allows them full access to the victim’s financial accounts and resources.

Additionally, some criminals are skilled enough to bypass bank interaction altogether. They can use the obtained credentials to log into online accounts directly, executing unauthorised transactions without needing any further verification.
The consequences for victims can be devastating, leading not only to financial loss but also to emotional distress as they recover their stolen identities and secure their accounts. Consequently, individuals must remain vigilant and understand these risks to protect themselves against potential account takeovers for repair. Additionally, they may find themselves tangled in legal disputes as they try to prove their innocence.

Recovering from such a violation requires diligence and time, making it crucial for individuals to safeguard their personal information vigilantly. Implementing measures like shredding sensitive documents and monitoring credit reports can help prevent these types of crimes before they occur.t to emerging challenges incorporate regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
Analysis of Scam Types and Prevention in Singapore

Based on the document, here’s an analysis of the scam types prevalent in Singapore and the prevention strategies being implemented:
Main Scam Types
- Self-Effecting Transfer Scams
- Most common type where victims willingly transfer money to scammers
- Psychological tactics target emotions like desire for companionship, respect for authority, and greed
- Victims often refuse to believe they’re being scammed

- Malware and Phishing Attacks
- Target bank accounts and online credentials
- Often involve sophisticated technical deception
- Phone/SIM-Based Scams
- Scammers using local phone numbers to make calls and send SMS
- Creates a false sense of legitimacy
- Cryptocurrency Scams
- Fake crypto trading interfaces that simulate profits
- Malware/phishing to drain crypto wallets
- Requesting victims convert money to cryptocurrency to evade banking safeguards
- Social Media and Messaging App Scams
- 60% of scams occur through these platforms
- Telegram specifically mentioned as a platform of concern (scam reports doubled in 2024)

Prevention Strategies
Government Regulatory Measures

- Protection from Scam Bills (January 2025)
- Empowering police to temporarily restrict banking transactions as a last resort
- Target cases where victims refuse to believe they’re being scammed
- SIM Card Regulations
- Limits on post-paid SIM card ownership
- Criminalization of SIM card misuse and transfer
- Penalties for SIM card abuse in scams
- Online Criminal Harms Act
- Requires online services to implement anti-scam measures
- Encourages robust user verification against government-issued IDs
- Potential for additional legislative action against platforms like Telegram
Banking/Financial Protection

- Enhanced Authentication
- FIDO-compliant hardware tokens being studied
- Requires physical proximity for transaction authentication
- Transaction Safeguards
- Cooling-off periods for high-risk transactions
- Enhanced fraud analytics
- Information sharing on money mule accounts
- Cryptocurrency Protection
- Working with MAS-licensed digital payment token providers
- Strengthening operational links with law enforcement

Public Education and Empowerment

- ScamShield Suite
- Launched September 2024
- Allows the public to check, report, and stay updated on scams
- ScamShield hotline (1799) for assistance
- Targeted Awareness Campaigns
- Monthly media campaigns
- Tailored to vulnerable population segments for specific scam types

Key Challenges and Trends
- Rising Financial Impact
- Total losses reached $1.1 billion in 2024 (a 70% increase from 2023)
- Evolving Tactics
- Scammers pivoting to local phone numbers
- Increased use of cryptocurrency to evade banking safeguards
- Exploitation of anonymity on messaging platforms
- Cross-Platform Nature
- Requires collaboration between government, tech companies, and financial institutions
- International dimension (implied by sophisticated criminal syndicates)

The Singapore approach appears multifaceted. It combines regulatory powers, technological solutions, industry collaboration, and public education to create a comprehensive anti-scam ecosystem. The emphasis on both preventive measures and empowering individuals to recognize scams suggests a balanced strategy to address this growing threat.
Maxthon

Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
Maxthon private browser for online privacyThis meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
