Analysis of the Singapore Court Case on Debt Avoidance
How the Business Owner Attempted to Avoid Debt
The business owner, who ran a renovation firm, employed a calculated strategy to avoid paying compensation to a client:
- Strategic fund withdrawal: After losing a lawsuit to a dental company over substandard renovation work, he systematically emptied his company accounts before paying the court-ordered compensation of over $500,000.
- Method of extraction: He withdrew approximately $1.18 million through two channels:
- $500,000 as dividends to himself
- $680,000 as repayment for “debt” he claimed the company owed him
- Timing: The court noted the suspicious timing of his actions. While he hadn’t drawn dividends between 2012 and 2015, he paid himself a total of $2,800,000 in dividends and $820,746 in loan repayments after the client filed the lawsuit.
- Legal shield attempt: He attempted to apply the principle of separate legal personality (which holds that a company is distinct from its shareholders) to argue that he owed no personal obligation to creditors.
How He Was Caught
The case took an unusual turn when the company was wound up due to its inability to pay compensation:
- Liquidators’ action: Instead of simply declaring the company bankrupt, the liquidators actively pursued the owner to recover the money he had withdrawn.
- Money trail examination: The financial transactions between the owner and his company were scrutinised, revealing the pattern and timing of withdrawals.
- Financial health assessment: Following the $1.18 million withdrawal, the company was left with less than $90,000 in working capital, clearly demonstrating a deliberate depletion of company resources.
The Legal Process and Investigation
The case went through multiple levels of the judicial system:
- Initial lawsuit: The dental company successfully sued the renovation firm for substandard work that resulted in flooding and mould issues.
- High Court ruling: The High Court ordered the owner to return $1.18 million to his firm, finding that as a director, he failed to act in the company’s best interests.
- Appeal process: The owner appealed the decision, but the Court of Appeal upheld the order.
- Landmark ruling: Chief Justice Sundaresh Menon delivered a significant ruling establishing that company directors are bound to consider creditors’ interests in certain circumstances.
Implications for Businesses
The Court of Appeal’s decision has far-reaching implications:

- Director accountability: Business owners and directors can be held personally accountable for company debts if they deliberately siphon funds to avoid paying creditors.
- “Creditor duty”: Directors now have a legal obligation to act in good faith toward creditors, particularly when the company is facing financial difficulties.
- Recovery mechanisms: Liquidators can pursue directors who breach their duty by depleting corporate funds in disregard of creditor interests.
- Balance of risk and responsibility: The ruling distinguishes between legitimate business decisions that may fail (which do not trigger personal liability) and deliberate attempts to defraud creditors (which do).
- Three-tiered approach: The court established different standards for director conduct based on the company’s financial status:
- Solvent companies: Directors primarily consider shareholder interests
- Companies at risk of default: Directors’ decisions face heightened scrutiny
- Insolvent companies: Directors have an explicit “creditor duty”
This landmark case strengthens protections for creditors in Singapore while establishing clearer guidelines for director conduct during financial distress, particularly regarding transactions that benefit shareholders or directors at the expense of creditors.
Bakery Financial Mismanagement Case
Here are the key points from this corporate mishap:

- A director lent $150,000 to his bakery chain company to help open a new branch. When he asked for repayment, he was accused of stealing money that was actually his in the first place.
- The company’s finance manager had embezzled approximately $400,000. This complicated situation led to accusations that the director and managing director were conspiring with the finance manager.
- The company filed a lawsuit against all three, but it failed spectacularly because:
- The company was unable to prove any conspiracy.
- Their financial records were so poor that they couldn’t even definitively prove how much the finance manager had stolen.
- The director had proper documentation for his loan
- Ironically, the finance manager returned approximately $420,000 but later claimed she might have overpaid by $80,000 and attempted to recover that amount.
- The High Court judge, Hri Kumar Nair, ruled against the company, noting that their lawsuit only succeeded in demonstrating their lack of proper financial controls.

The article highlights three crucial lessons:
- Maintain proper records – The director’s documentation of his loan saved him from the accusations.
- Understand employee duties – Employees following company procedures shouldn’t fear wrongful accusations.
- Wrongdoings must be proven – The company couldn’t prove that the misappropriation prevented business expansion.
The company ultimately had to pay significant legal costs to all parties: $75,000 to the finance manager, $95,000 to the director, and $120,000 to the managing director.
The closing message is clear: without proper financial records, it becomes challenging to reclaim missing funds.
Analysis of Corporate Scam Issues in the Bakery Chain Case
Key Scam Issues

- Internal Embezzlement: The finance manager exploited weak financial controls to misappropriate approximately $400,000 over a period of several years.
- Poor Documentation: The lack of proper record-keeping created an environment where theft could occur undetected, and the company was unable to determine how much was stolen.
- Informal Decision-Making: Business decisions made through informal channels, such as phone messages, without proper documentation, led to confusion and disputes.
- False Accusations: The company incorrectly accused innocent parties, including the director and managing director, of participating in the embezzlement scheme.

Complications That Arose
- Inability to Track Funds: The company was unable to determine the exact amount stolen or trace the whereabouts of the money.
- Misidentification of Culprits: Poor financial oversight led to the wrongful accusation of those who actually helped the company, specifically the lending director.
- Legal Backfire: The company’s baseless lawsuit resulted in substantial legal costs, totalling $290,000, being awarded against it.
- Counterproductive Recovery Efforts: The embezzler’s uncertainty about how much she stole led to her claiming she overpaid during restitution.
- Trust Breakdown: The accusations likely damaged relationships among company leadership and shareholders.

Prevention Methods
- Implement Robust Financial Controls:
- Require multiple approvals for significant transactions.
- Separate financial duties among different employees (authorisation, recording, custody)
- Conduct regular reconciliation of accounts
- Document All Financial Transactions:
- Create formal agreements for all loans and investments
- Maintain comprehensive supporting documentation for all transactions
- Record board decisions in official minutes
- Regular Independent Audits:
- Schedule periodic third-party audits to detect irregularities
- Implement surprise audits to deter potential fraud
- Clear Authority Boundaries:
- Establish written policies defining spending authority limits
- Document exceptions to standard procedures
- Improve Corporate Governance:
- Formalise shareholder communication and decision-making processes.
- Create an audit committee to oversee financial controls
- Document all shareholder loans and capital injections properly
- Staff Training:
- Train employees to recognise potential fraud indicators
- Establish whistleblower protocols for reporting suspicious activities
- Technology Solutions:
- Implement accounting software with audit trails.
- Use electronic payment systems with built-in approval workflows
- Leverage automation to reduce manual record-keeping errors
By implementing these preventive measures, companies can significantly reduce the risk of internal scams, foster accountability, and ensure that if issues do arise, they have the necessary documentation to address them properly.
Applying Fraud Prevention to Singapore’s Business Context
Singapore-Specific Challenges & Considerations
- Regulatory Framework:
- Singapore companies must comply with the Companies Act, which requires proper financial record-keeping
- Listed companies are subject to additional scrutiny under Singapore Exchange (SGX) regulations.
- The Accounting and Corporate Regulatory Authority (ACRA) oversees corporate compliance.
- Business Culture:
- Singapore’s business environment often features family-owned businesses with close-knit management structures.
- Trust-based relationships sometimes override formal controls, especially in SMES
- The bakery chain case exemplifies this issue, with decisions often made through informal messages.
- Digital Transformation:
- Singaporean businesses are increasingly operating digitally, creating new vulnerabilities to fraud.
- E-payment systems are widespread, requiring specific security measures

Singapore-Focused Prevention Strategies
- Leverage Singapore’s Regulatory Resources:
- Utilize ACRA’s guidance on proper corporate governance
- Implement the Singapore Code of Corporate Governance principles
- Follow Monetary Authority of Singapore (MAS) guidelines on financial controls
- Singapore-Specific Audit Practices:
- Engage Singapore-registered public accountants for regular audits
- Implement Singapore Standards on Auditing (SSA) recommendations
- Consider specialized audits for high-risk areas (e.g., cash handling in F&B businesses)
- Employee Training for Singapore Context:
- Train staff on Singapore’s Prevention of Corruption Act
- Create awareness of Singapore’s Whistleblower Protection framework
- Establish clear reporting channels compliant with local regulations
- Technology Solutions Available in Singapore:
- Adopt accounting software approved by IRAS for Singapore businesses
- Implement PayNow Corporate or GIRO payment systems with approval workflows
- Consider blockchain solutions for transparent record-keeping (Singapore is a blockchain hub)
- Cultural Adaptations:
- Balance Singapore’s relationship-oriented business culture with formal controls
- Implement structured documentation while respecting cultural norms
- Establish clear boundaries between family/personal relationships and business decisions
- Singapore Government Support:
- Utilize Enterprise Singapore’s resources for SMEs to improve governance
- Access Singapore Business Federation training on financial best practices
- Apply for a Productivity Solutions Grant to implement financial control systems
- Industry-Specific Considerations for F&B Businesses in Singapore:
- Implement point-of-sale systems with audit trails (particularly relevant for bakery chains)
- Establish inventory management controls to prevent leakage
- Create standard operating procedures for cash handling at multiple outlets

Implementation Timeline for Singapore Businesses
- Immediate Steps (1-3 months):
- Conduct a compliance check against the Singapore Companies Act requirements
- Review and formalise all shareholder agreements and loans
- Document authority limits for all management positions
- Medium-Term Actions (3-12 months):
- Implement appropriate accounting software with Singapore-compliant features.
- Establish regular internal audit processes
- Train staff on financial controls and fraud prevention
- Long-Term Strategy (12+ months):
- Develop a comprehensive corporate governance framework.
- Create a culture of transparency and accountability
- Establish board-level oversight of financial controls

By implementing these Singapore-specific prevention measures, local businesses can significantly reduce their vulnerability to internal fraud while maintaining compliance with Singapore’s regulatory environment.

General Scam Prevention Tips
- Trust your instincts
- If an offer seems too good to be true, it probably is
- Keep personal and financial information confidential
- Stay informed about the latest scam techniques
- Report suspicious activities to the authorities
- Educate family members, especially older relatives
- Use secure, updated technology
- Maintain a healthy level of scepticism online

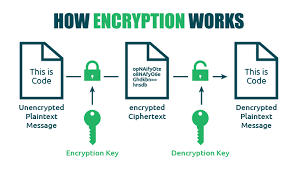
How Encryption Works

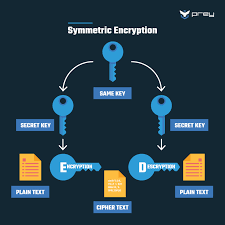
Encryption utilises mathematical algorithms to transform plaintext (readable data) into ciphertext (encrypted data). Only those with the decryption key can convert the ciphertext back into usable information. There are two main types:
- Symmetric Encryption: Uses the same key for both encryption and decryption. It’s efficient, but it requires a secure key exchange.
- Asymmetric Encryption uses a pair of keys—a public key for encryption and a private key for decryption—to allow secure communication without prior key exchange.
Key Encryption Applications for Privacy
Device Encryption
- Full-disk encryption: Protects all data on your computer or smartphone (BitLocker for Windows, FileVault for Mac, built-in encryption for iOS and Android)
- File-level encryption: Protects individual files and folders

Communication Encryption
- HTTPS: Secures website connections (look for the padlock icon in your browser)
- End-to-end encryption: Used in messaging apps like Signal, WhatsApp, and others to ensure only you and your recipient can read messages
- Email encryption: Options include PGP (Pretty Good Privacy), S/MIME, or encrypted email services
Network Encryption
- VPNs: Create an encrypted tunnel for all your internet traffic
- Wi-Fi encryption: WPA3 is the current most substantial standard for wireless networks
Cloud Storage Encryption
- At-rest encryption: Protects stored data
- Zero-knowledge encryption: The provider has no access to your encryption keys
- Client-side encryption: Data is encrypted before leaving your device

Implementing Encryption in Your Digital Life
- Enable device encryption on all your computers and mobile devices
- Use encrypted messaging apps for sensitive communications
- Verify HTTPS connections when sharing personal or financial information
- Consider encrypted email for sensitive communications
- Choose cloud services with strong encryption policies
- Use a VPN when connecting to public Wi-Fi networks
- Password-protect and encrypt sensitive files and backups
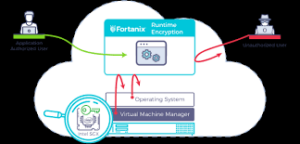
Limitations to Consider
- Encryption can’t protect against malware already on your device
- Weak passwords can undermine even the strongest encryption
- Encryption doesn’t hide metadata (who you’re communicating with, when, how often)
- Some countries have laws limiting encryption use or requiring backdoors

Encryption is a fundamental aspect of digital privacy that works best as part of a comprehensive security strategy. By understanding and implementing appropriate encryption methods, you can significantly enhance your privacy protection online.
.
Identity Theft
Identity theft is a pervasive form of fraud that can have devastating consequences for victims. In this crime, the perpetrator steals an individual’s personal information to assume their identity. This stolen information can often be gathered from discarded documents such as bank statements, utility bills, or even phishing scams.
Once armed with this data, the criminal may choose to open accounts in the victim’s name, a process known as application fraud. They might apply for credit cards, loans, or utility services under pretences, leaving the unsuspecting victim to deal with the aftermath.
The emotional toll of identity theft can be immense. Victims often face financial losses and damage to their credit scores, which can take years. In today’s digital age, account takeovers have become a prevalent threat to unsuspecting victims. Criminals typically employ tactics such as phishing, vishing, or smishing to manipulate individuals into revealing their personal information.

Phishing often involves deceptive emails that appear to come from legitimate sources. These emails may prompt the victim to click on malicious links or provide sensitive details under the guise of verifying their identity.
Vishing, or voice phishing, involves phone calls in which scammers impersonate bank representatives or trusted entities to extract confidential information directly from the victim. Similarly, smishing involves text messages that lure individuals into divulging critical data.
Once armed with this personal information, the criminal can easily convince a bank to change the account holder’s address. This deception allows them full access to the victim’s financial accounts and resources.

Additionally, some criminals are skilled enough to bypass bank interaction altogether. They can use the obtained credentials to log into online accounts directly, executing unauthorised transactions without needing any further verification.
The consequences for victims can be devastating, leading not only to financial loss but also emotional distress as they recover their stolen identities and secure their accounts. Consequently, individuals must remain vigilant and understand these risks to protect themselves against potential account takeovers for repair. Additionally, they may find themselves tangled in legal disputes as they try to prove their innocence.

Recovering from such a violation requires diligence and time, making it crucial for individuals to safeguard their personal information vigilantly. Implementing measures like shredding sensitive documents and monitoring credit reports can help prevent these types of crimes before they occur.
Maxthon
Maxthon has set out on an ambitious journey aimed at significantly bolstering the security of web applications, fueled by a resolute commitment to safeguarding users and their confidential data. At the heart of this initiative lies a collection of sophisticated encryption protocols, which act as a robust barrier for the information exchanged between individuals and various online services. Every interaction—be it the sharing of passwords or personal information—is protected within these encrypted channels, effectively preventing unauthorised access attempts from intruders.
 This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
This meticulous emphasis on encryption marks merely the initial phase of Maxthon’s extensive security framework. Acknowledging that cyber threats are constantly evolving, Maxthon adopts a forward-thinking approach to user protection. The browser is engineered to adapt to emerging challenges, incorporating regular updates that promptly address any vulnerabilities that may surface. Users are strongly encouraged to activate automatic updates as part of their cybersecurity regimen, ensuring they can seamlessly take advantage of the latest fixes without any hassle.
In today’s rapidly changing digital environment, Maxthon’s unwavering commitment to ongoing security enhancement signifies not only its responsibility toward users but also its firm dedication to nurturing trust in online engagements. With each new update rolled out, users can navigate the web with peace of mind, assured that their information is continuously safeguarded against ever-emerging threats lurking in cyberspace.
