This is concerning information about a sophisticated scam targeting Android users through social media advertisements. Let me highlight the key points:
The scam works through these steps:
- Victims see Facebook or TikTok ads and leave their contact details
- Scammers contact them via WhatsApp, requesting payment
- When victims try to pay, they encounter “payment issues”
- To “fix” the issue, victims are tricked into downloading malicious APK files
- The malware gives scammers remote access to steal information like SMS OTPS
- Scammers then make unauthorised transactions
Some important details:
- At least 128 cases reported since February 2025
- Total losses of at least $2.4 million
- In some cases, victims are instructed to disable Google Play Protect
- Victims may also be asked to download VPN apps to help scammers bypass banking security
The Singapore police recommend:
- Disabling “Install Unknown App” or “Unknown Sources” in phone settings
- Not granting permissions to suspicious pop-ups
- Only downloading apps from official stores like Google Play
- Being cautious of requests to disable Google Play Protect
This appears to be part of a larger scam problem in Singapore, with victims losing $1.1 billion to scams in 2024 and more than $3.4 billion since 2019.
Android Malware Scams: An In-Depth Analysis
Common Malware Scam Techniques
Social Media Advertisement Baiting
The recent Singapore case highlights how scammers are using Facebook and TikTok advertisements as entry points. They create seemingly legitimate ads for products or services, collect contact information, and then switch to WhatsApp for direct manipulation. This technique works because it leverages trusted platforms to establish initial credibility.
Malware Deployment Strategies
Scammers typically employ several tactics to get malware onto victims’ devices:
- APK Sideloading – Convincing users to install apps outside the Google Play Store through direct APK files
- Security Bypass Instructions – Instructing victims to disable security features like Google Play Protect
- Trojan Apps – Presenting malware as legitimate apps like “payment verification tools” or “special offer apps”
- VPN Installation – Having victims install legitimate VPN apps that allow remote access to their devices
Technical Aspects of Android Malware
Modern Android malware typically includes:
- Keyloggers – Recording everything typed, including passwords and PINS
- Screen Capture – Taking screenshots during banking operations
- SMS Interceptors – Capturing authentication codes sent via text
- Remote Access Trojans (RATS) – Allowing complete remote device control
- Data Exfiltration – Stealing contacts, photos, and other sensitive information
Psychological Manipulation Techniques
These scams succeed through:
- Urgency – Creating time pressure to complete actions quickly
- Problem-Solution Narrative – Presenting malware as the “fix” to a payment problem
- Technical Intimidation – Using technical jargon to confuse and overwhelm victims
- Incremental Compliance – Starting with small requests before escalating to malware installation
Anti-Scam Resources in Singapore
Government Initiatives
- ScamShield App – A mobile application developed by the Singapore government that blocks known scam calls and messages. Available on ios and Android platforms.
- Anti-Scam Centre (ASC) – Established by the Singapore Police Force in 2019, the ASC works to disrupt scam operations and recover stolen funds. They coordinate between banks, telecommunications companies, and other stakeholders.
- National Crime Prevention Council (NCPC) – Runs the “Scam Alert” website and educational campaigns to raise public awareness about various scams.
- Report Hotlines:
- Police Hotline: 1800-255-0000
- Anti-Scam Helpline: 1800-722-6688
Banking Protections
Singapore banks have implemented several anti-scam measures:
- Mandatory cooling-off periods for new device registration
- Transaction limits for online transfers
- AI-based fraud detection systems
- SMS alerts for unusual transactions
- Dedicated fraud investigation teams
Community Support
- Victim Support Groups – Organisations like AWARE provide counselling for scam victims
- Scamsg Community – Online forums where people share experiences and warning signs
- NCPC Volunteer Programs – Community ambassadors who educate vulnerable populations
Prevention Best Practices
- Device Security:
- Keep “Install Unknown Apps” disabled
- Never disable Google Play Protect
- Use anti-malware apps from reputable companies
- Keep your operating system and apps updated
- Transaction Safety:
- Use a separate device for banking if possible
- Enable biometric authentication for financial apps
- Set up transaction notifications and limits
- Verify website URLS before entering credentials
- Red Flags to Watch For:
- Requests to install apps outside Google Play
- Instructions to disable security features
- Unexpected “payment errors” requiring special solutions
- Pressure to act quickly or lose an opportunity
- Huge discounts or deals requiring upfront deposits
The evolving sophistication of these scams highlights the importance of ongoing education and vigilance, as technical protections alone cannot entirely prevent social engineering attacks.
Social Engineering Attacks: Understanding The Human Element of Cybersecurity
Social engineering attacks exploit human psychology rather than technical vulnerabilities. They manipulate people into breaking security protocols, revealing sensitive information, or taking actions that compromise security. These attacks are hazardous because they bypass technical security measures by targeting the most vulnerable element in any security system: human behaviour.
Core Principles of Social Engineering
Social engineering attacks typically leverage these psychological principles:
- Authority – Pretending to be a figure of authority (boss, tech support, government official) to compel compliance
- Urgency – Creating time pressure that forces hasty decisions without proper verification
- Fear – Generating anxiety about negative consequences (account closure, legal issues, missed opportunities)
- Trust – Building rapport before making requests or exploiting established trusted relationships
- Scarcity – Suggesting limited availability (“act now or miss out”) to push immediate action
- Social proof – Implying that others have already complied with similar requests
Common Social Engineering Attack Types
Phishing
Email or messaging attacks that impersonate legitimate organizations to steal credentials or install malware. Variants include:
- Spear phishing – Highly targeted attacks using personal information
- Whaling – Targeting high-value individuals like executives
- Smishing – Phishing via SMS messages
- Vishing – Voice-based phishing via phone calls
Pretexting
Creating a fabricated scenario (pretext) to extract information. For example, calling as a “survey researcher” or “HR representative conducting verification” to collect personal details.
Baiting
Offering something enticing (free movie download, USB drive in the parking lot) that contains malware or leads to credential theft.
Quid Pro Quo
Offering a service or benefit in exchange for information or system access (e.g., “free IT support” that requires your password).
Tailgating/Piggybacking
Physically following an authorized person into a secured area by appearing to belong or asking for assistance (“Could you hold the door? My hands are full”).
Watering Hole Attacks
Compromising websites frequently visited by the target group, rather than attacking the target directly.
Scareware
False alarms or fake virus alerts that trick users into installing malicious software that claims to solve a non-existent problem.
Signs of a Social Engineering Attack
- Unusual urgency or pressure to act quickly
- Requests for sensitive information or unusual access
- Communication with grammar or spelling errors
- Slight variations in email domains or website URLs
- Unsolicited attachments or download requests
- Offers that seem too good to be true
- Appeals to fear or authority to bypass normal procedures
- Requests to keep the interaction secret
Protection Strategies
For Individuals
- Verify requests through official channels before taking action
- Be suspicious of urgency, especially regarding financial matters
- Check email sender addresses carefully
- Never provide sensitive information in response to unsolicited requests
- Use multi-factor authentication wherever possible
- Think before clicking links or opening attachments
For Organizations
- Regular security awareness training for all employees
- Simulated phishing exercises to test and improve awareness
- Clear protocols for verifying identities and handling sensitive information
- Strong authentication policies
- Designated contacts for reporting suspicious communications
- Clear escalation procedures for security concerns
Social engineering continues to evolve, with attackers becoming increasingly sophisticated in how they blend technical elements with psychological manipulation. The most effective defence combines technical safeguards with educated, vigilant users who understand these attack methods.
Examples of Malware Social Engineering Scams
Here are some common examples of how social engineering tactics are used to deliver malware:
Job Offer Scams
- Approach: Victim receives an attractive job offer via email or LinkedIn
- Hook: “We’re impressed with your profile and want to interview you”
- Malware Delivery: Fake application forms or “interview preparation documents” containing malware
- Psychology Used: Appealing to career ambitions and financial opportunity
Package Delivery Notifications
- Approach: SMS or email claiming “delivery attempted” or “package waiting”
- Hook: “Click here to reschedule delivery” or “track your package”
- Malware Delivery: Fake tracking apps or malicious links disguised as delivery portals
- Psychology Used: Curiosity about unexpected packages and the urgency to not miss the delivery
Tech Support Scams
- Approach: Pop-up warnings or calls claiming your device is infected
- Hook: “Your computer has a critical virus! Call this number immediately”
- Malware Delivery: Remote access tools that attackers claim will “fix” your computer
- Psychology Used: Fear of data loss and trust in technical authority figures
Banking Alert Scams
- Approach: SMS or email appearing to be from your bank about “suspicious activity”
- Hook: “Verify your identity to prevent account freeze”
- Malware Delivery: Fake banking apps or “security verification tools”
- Psychology Used: Fear of financial loss and urgency to protect assets
Software Update Deception
- Approach: Fake update notifications for standard software like Adobe, Java, or browsers
- Hook: “Critical security update required immediately”
- Malware Delivery: Trojanized versions of legitimate software
- Psychology Used: Security consciousness is being weaponised against the user
COVID-19/Health Crisis Scams
- Approach: Information about vaccines, treatments, or health protocols
- Hook: “Download the latest health guidelines” or “verify your vaccination status”
- Malware Delivery: Fake health apps or infected PDF “information guides”
- Psychology Used: Health concerns and desire for protection during crises
Government Impersonation
- Approach: Messages claiming to be from tax authorities, law enforcement, or other agencies
- Hook: “Tax refund available” or “legal action pending – respond immediately”
- Malware Delivery: Malicious attachments disguised as official forms
- Psychology Used: Authority compliance and fear of legal consequences
Social Media Profile Viewing Scams
- Approach: Messages claiming someone viewed your profile or tagged you
- Hook: “See who viewed your profile” or “see the photo you were tagged in”
- Malware Delivery: Fake social media apps or browser extensions
- Psychology Used: Social curiosity and FOMO (fear of missing out)
Investment Opportunity Scams
- Approach: Offers for exclusive investment platforms or cryptocurrency deals
- Hook: “Early access to our trading platform” or “crypto mining software”
- Malware Delivery: Fake investment apps that steal credentials or crypto wallets
- Psychology Used: Greed and fear of missing financial opportunities
Free Software/Media Scams
- Approach: Offers for free premium software, games, or media content
- Hook: “Get [expensive software] for free!” or “Watch new movies before release”
- Malware Delivery: Trojanized software or fake media players
- Psychology Used: Desire for valuable content without payment
Each of these scams succeeds by creating an emotional response that overrides critical thinking, while presenting malware as a solution to a problem or path to an opportunity. The most effective protection is recognising these patterns and maintaining healthy scepticism toward unexpected communications, especially those creating pressure to act quickly.
I’ve read the article about fraudsters using malware to access victims’ bank accounts and take out loans. Here are the key points:
- Scammers are now using malware to empty victims’ bank accounts and take out credit cards and personal loans through compromised banking apps.
- This malware typically comes from apps downloaded from non-official app stores, which allow hackers to spy on and control the victim’s device.
- In the first half of 2023, hackers stole more than $10 million from compromised accounts across 750+ cases in Singapore.
- Between January and August, at least 30 victims had unauthorized loans taken out in their names via credit card cash advances.
- The article compares loan application processes across three central Singapore banks:
- DBS/POSB: Allows quick loans with minimal verification, taking just seconds to complete
- OCBC and UOB: Require more verification steps, including Singpass authentication
- A cybersecurity expert recommends that banking apps implement more security challenges and “cooling periods” for suspicious transactions.
Analysis of Malware Scams in Singapore
How Malware Scams Work
Based on the article, malware scams in Singapore typically follow this pattern:
- Initial Deception: Victims are tricked into downloading malicious applications from non-official app stores.
- Device Compromise: Once installed, the malware allows hackers to:
- Monitor the victim’s activities
- Take control of the device
- Access banking applications
- Financial Exploitation: Hackers then:
- Empty bank accounts directly
- Taking out unauthorized loans via credit card cash advances
- Transfer funds to their own accounts
- Expanding Tactics: The evolution from simply emptying accounts to taking additional loans shows that scammers are becoming more sophisticated in maximizing financial damage.
Current Impact
- Over $10 million stolen in the first half of 2023 alone
- More than 750 cases were reported in this period
- At least 30 victims were burdened with unauthorized loans between January and August.
Security Vulnerabilities
The article highlighted significant differences in bank security practices:
- DBS/POSB: Allows loan applications to be processed within seconds with minimal verification
- OCBC/UOB: Implement stronger security with multiple verification steps, including Singpass authentication
Anti-Scam Resources in Singapore
If you’re in Singapore and need help with scams, here are the key resources:
- Anti-Scam Helpline: 1-800-722-6688
- For reporting scams and getting immediate assistance
- Police Hotline: 1-800-255-0000
- For filing police reports about scam incidents
- ScamShield App:
- Government-developed app that blocks scam calls and messages
- Available for iOS and Android
- Scam Alert Website: www.scamalert.sg
- Provides information on the latest scam tactics
- Offers prevention tips and resources
- National Crime Prevention Council:
- Runs anti-scam campaigns
- Provides educational materials
- Bank-Specific Support:
- Each bank has dedicated fraud reporting hotlines
- Some offer immediate account freezing options through their apps
Protecting Your Device From Malware
Prevention Measures
- Only Download Apps From Official Sources
- Stick to the Google Play Store or Apple App Store
- Avoid sideloading apps from third-party websites or unknown sources
- Keep Your Device Updated
- Install operating system updates promptly
- Enable automatic updates when possible
- Update apps regularly
- Install Mobile Security Solutions
- Use reputable antivirus/anti-malware apps
- Consider using ScamShield (Singapore’s official anti-scam app)
- Verify App Permissions
- Review permissions before installing apps
- Be suspicious of apps requesting excessive permissions
- Deny unnecessary access to sensitive functions
- Be Cautious With Links
- Don’t click on suspicious links in SMS, WhatsApp, or emails
- Verify the sender’s identity before clicking any links
- Check for URL spelling errors or suspicious domains
- Enable Two-Factor Authentication
- Set up 2FA for banking apps and important accounts
- Use authentication apps rather than SMS when possible
- Regularly Monitor Financial Accounts
- Check bank statements frequently
- Set up transaction alerts for unusual activity
Steps to Take When Compromised
Immediate Actions
- Disconnect from the Internet
- Turn on airplane mode or disconnect from Wi-Fi/mobile data
- This helps prevent further data transmission
- Contact Your Bank Immediately
- Call your bank’s fraud hotline
- Request immediate freezing of accounts
- Dispute any unauthorized transactions
- Report any unauthorized loans
- Change Passwords
- Using a different, uninfected device
- Start with financial and email accounts
- Use strong, unique passwords
- File a Police Report
- Contact Singapore Police at 1-800-255-0000
- File a report on the Police website
- Document case number for reference
- Reset Your Device
- Back up important data if possible (but be cautious not to back up malware)
- Perform a factory reset to remove malware
- Set up the device as new rather than restoring from backup
Follow-Up Steps
- Monitor Credit Reports
- Check for unauthorized accounts or loans
- Look for suspicious inquiries
- Report to Singapore’s Anti-Scam Helpline
- Call 1-800-722-6688 for assistance
- Report the incident to help prevent others from being victimized
- Install Protection Before Restoring Apps
- Set up security software before installing other apps
- Be selective when reinstalling applications
- Educate Yourself
- Visit www.scamalert.sg for the latest scam tactics
- Follow official channels for security updates
Remember that preventing malware infection is far easier than dealing with the aftermath of a compromise. Always be vigilant about what you download and install on your devices.
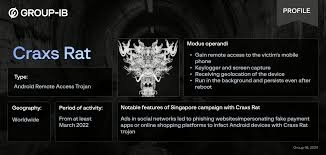
This article details a sophisticated Remote Access Trojan (RAT) called Craxs Rat that has been used in phishing campaigns targeting Singapore since April 2023. Here are the key points:
What is Craxs Rat?
- A Remote Access Trojan that gives attackers complete control over victims’ Android devices
- Developed by a threat actor named “EVLF” based on leaked source code from an earlier RAT called Spymax
- Specifically designed to target Android devices
- The latest version (as of the article) is Craxs Rat v7.5, released on April 17, 2024

How the attacks work:
- Victims are lured with fake advertisements or phishing websites
- Users are tricked into downloading fake Android apps posing as legitimate brands
- Once installed, the malware requests extensive permissions (SMS, calls, camera, etc.)
- Attackers gain complete remote control of the victim’s device
Technical details:
- The malware encodes its Command & Control (C2) server details using base64 encoding
- Analysis of C2 infrastructure suggests Chinese-speaking threat actors are behind the Singapore campaign
- The malware supports multiple languages (English, Arabic, Turkish, Simplified Chinese)
- Phishing websites use the CRMEB admin panel, popular among Chinese developers

Timeline and evolution:
- The original Spymax RAT was developed by “✶ s c я є α м” in 2019
- Source code leaked in 2020
- EVLF created Craxs Rat based on the leaked code
- EVLF’s original Telegram channel was sold on September 5, 2023
- EVLF created a new Telegram channel and continues to develop Craxs Rat
- The latest version (7.5) was released on April 17, 2024
Recommendations for protection:
- Only download apps from trusted app stores (Google Play, Apple App Store)
- Be cautious with digital communications
- Educate teams and customers about phishing threats
- Monitor and control app permissions
- Work with reliable security vendors
Detailed Analysis of Craxs Rat Malware & Prevention Strategies for Singapore
Technical Analysis of Craxs Rat
Origins and Evolution
Craxs Rat evolved from Spymax (also known as SpyNote), which was initially developed by a threat actor called “✶ s c я є α м” in 2019. When the Spymax source code leaked in 2020, a developer known as “EVLF” (likely based in Syria) modified it to create Craxs Rat. The timeline shows continuous development, with the latest version (7.5) released on April 17, 2024.
Technical Capabilities
- Complete Device Control: Once installed, Craxs Rat provides attackers with comprehensive remote access to the victim’s device.
- Extensive Permission Exploitation: The malware requests and abuses permissions for:
- SMS access (reading and sending)
- Call recording and logs
- Contact list access
- Camera and microphone control
- GPS location tracking
- File system access
- Screen recording/viewing
- Ability to make calls
- Command & Control Infrastructure:
- Uses base64 encoding to hide C2 server details
- Communicates with Windows Server 2019 systems (with Chinese language settings)
- Maintains persistent connections for ongoing control
- Multi-Language Support: Interface supports English, Arabic, Turkish, and Simplified Chinese, indicating global targeting.
- Accessibility Service Abuse: Uses Android’s Accessibility Service to gain more profound control of device functions.
- Delivery Mechanism in Singapore: Primarily distributed through:
- Fake shopping platforms
- Impersonation of anti-scam centers (ironic)
- Fake food delivery apps
- Other local service providers

Singapore-Specific Campaign Analysis
The Singapore campaign began in April 2023 and has targeted multiple sectors:
- Impersonated Brands: At least 10 different brands were spoofed, including:
- 1st Mall, E2 Mall, Shopnow
- Anti-Scam center
- SG-Furniture
- Grab & Go
- Various local businesses

- Attack Infrastructure:
- Phishing websites administered via CRMEB (popular among Chinese-speaking developers)
- C2 servers running Windows with Chinese language settings
- Multi-language support suggests targeting diverse communities in Singapore
- Attack Flow:
- Victims encounter fake advertisements
- They’re directed to phishing websites mimicking legitimate services
- Users are convinced to download “payment” or “verification” apps
- Once installed, the RAT requests extensive permissions
- Attackers gain complete device control and access to banking credentials
Prevention Strategies for Singapore
For Individuals
- App Installation Discipline:
- Only download apps from Google Play or the Apple App Store
- Be highly suspicious of apps shared via messaging, SMS, or email links
- Verify app publishers and check reviews before installing
- Permission Awareness:
- Review permissions requested by apps – Be suspicious if a simple app requests extensive access
- Be particularly cautious of Accessibility Service requests
- Regularly audit app permissions on your device
- Banking Security:
- Use separate devices for banking when possible
- Consider using banking-specific security tools
- Enable two-factor authentication for financial accounts
- Verify transactions through separate channels
- Phishing Recognition:
- Check URLs carefully – legitimate Singapore businesses typically use .sg or .com.sg domains.
- Be suspicious of deals that seem unusually generous
- Verify company contacts through official channels
- Be wary of urgency tactics pushing immediate app downloads

For Organizations in Singapore
- Employee Education:
- Conduct Singapore-specific training on mobile threats
- Create awareness about local brands being impersonated
- Establish clear protocols for verifying legitimate apps
- Implement regular security awareness updates
- Technical Controls:
- Deploy Mobile Device Management (MDM) solutions
- Implement Mobile Threat Defense (MTD) tools
- Consider mobile application management policies
- Set up network monitoring for suspicious connections
- Incident Response:
- Develop specific procedures for mobile malware incidents
- Create dedicated channels for reporting suspicious apps/messages
- Partner with Singapore’s Cyber Security Agency (CSA) for threat intelligence
- Maintain contact with SingCERT for the latest threat updates
- Multi-Language Security Communications:
- Given Singapore’s diverse population, provide security alerts in multiple languages
- Ensure security awareness reaches all demographic groups

For Singapore Government and Organizations
- Public Awareness:
- Launch campaigns specifically targeting Craxs Rat and similar threats
- Partner with telecom providers for security messaging
- Leverage Singapore’s ScamShield app to block known phishing URLs
- Regulatory Approach:
- Work with app stores to expedite the removal of fake apps
- Coordinate with banks to enhance mobile banking security
- Collaborate with INTERPOL and regional partners on cross-border investigations
- Technical Countermeasures:
- Share Craxs Rat indicators of compromise (IoCs) with local organizations
- Block known C2 domains at national internet gateways
- Provide analysis tools to help identify infected devices
- Industry Coordination:
- Facilitate information sharing between affected businesses
- Coordinate response through the Singapore Financial Services Information Sharing and Analysis Center (FS-ISAC)
- Develop early warning systems for new phishing campaigns
The continued evolution of Craxs Rat (with v7.5 just released in April 2024) suggests this threat will remain active in Singapore. A comprehensive approach involving individuals, organizations, and government entities offers the best protection against this sophisticated mobile threat.
Infostealer Malware
Infostealer malware has emerged as one of the most significant cybersecurity threats in recent times, casting a wide net over unsuspecting users. This type of malware comes in various forms, each with its distinct name and functionality. Alarmingly, some of these malicious tools are available as subscription-based services, allowing cybercriminals to pay monthly fees for access—much like a Netflix subscription.
The economy surrounding infostealer malware is thriving. A recent report from Kaspersky revealed that a staggering 25 million users were targeted between the beginning of 2023 and the end of 2024. This surge highlights the growing sophistication and prevalence of these attacks.

Infostealers are particularly insidious, explicitly designed to capture valuable personal information. They can extract bank card details, login credentials, and even sensitive media files, leaving victims vulnerable to financial loss and identity theft.
As this threat continues to evolve, it becomes increasingly crucial for individuals to stay informed and vigilant. Protect yourself by signing up for resources like Kurt’s The CyberGuy Report, which offers security alerts and expert tech tips tailored to keep you safe in the digital world. Awareness is your first line of defence against these lurking dangers.
A newly published report from Kaspersky Digital Footprint Intelligence paints a grim picture of the cybersecurity landscape for 2023 and 2024. Alarmingly, nearly 26 million devices fell victim to infostealer malware during this period. Among the casualties, more than 2 million unique bank card details were leaked, underscoring the extensive reach of cyber criminals.
Perhaps the most shocking revelation is that one in every 14 infections resulted in stolen bank card data. The implications of such breaches extend beyond mere financial loss; passwords, second-factor authentication cookies, and other sensitive credentials were also compromised, leaving users vulnerable to further attacks.
Kaspersky analysts highlighted a significant uptick in infections in 2024, primarily driven by specific strains of malware. RisePro, which accounted for only 1.4% of infections in 2023, skyrocketed to an alarming 22.45% in 2024. Meanwhile, Stealc—a newer threat first identified in 2023—also gained momentum, increasing its share from 2.65% to 13.33%.
Despite the emergence of these new threats, Redline maintained its notorious status as the most widespread infostealer, responsible for a staggering 34.36% of all infections. As the digital landscape evolves, the need for robust cybersecurity measures has never been more critical.

By August 2024, researchers unveiled a staggering statistic: an estimated 15.9 million devices had fallen victim to infostealer malware throughout the previous year. This alarming trend painted a bleak picture of the cybersecurity landscape, indicating that malicious actors were becoming increasingly sophisticated.
However, as the calendar turned to March 2025, the situation worsened. The number of infected devices surged to 16.49 million, surpassing earlier predictions by a striking 3.69%. This unexpected rise left many experts scrambling to reassess their forecasts and strategies.
Adding to the concern, new log files from 2023 continued to emerge on dark web platforms. This influx of data hinted at the possibility that the actual number of infections could be even higher than initially believed.
As researchers delved deeper, they found that over 9 million infections had already been tracked for 2024 alone. With this figure still climbing, it became clear that the final tally for the year would likely exceed the previous year’s numbers, though not by a substantial margin.
The relentless spread of info stealer malware served as a stark reminder of the ongoing battle between cybercriminals and those dedicated to safeguarding digital spaces.
In today’s digital landscape, where infostealer malware infections are surging at an alarming rate and cybercriminals are becoming increasingly cunning, it is more important than ever to take steps to safeguard your sensitive data. The threat to your bank cards and passwords is very real, but there are several effective strategies you can adopt to fortify your defences. Here are six thoughtful approaches that can help you protect your financial information.
First and foremost, investing in robust antivirus software is a fundamental step. Picture this: you install a powerful antivirus program on all of your devices, ensuring they are shielded from the ever-evolving threats lurking online. It’s not just about installation; keeping the software updated regularly is essential. This vigilant protector scans for potential threats, identifying and eliminating them before they can wreak havoc on your system. Imagine the peace of mind that comes with knowing your devices are equipped to combat malicious links that might attempt to infiltrate your private information. Furthermore, a good antivirus solution will alert you to phishing attempts and ransomware threats, acting as a digital guardian for your data and assets. If you’re curious about which antivirus software stands out in 2025, I have some recommendations that cater to Windows, Mac, Android, and iOS platforms.
Next, consider the innovative option of using virtual cards for online transactions. Instead of exposing your actual bank card details, you can generate temporary virtual cards through your bank or services like Privacy.com. These disposable cards serve as a protective layer, minimising the risk of your information being compromised in the event of a data breach. This simple yet effective strategy can significantly limit the fallout from any security incidents.

Additionally, it is crucial to take charge of your finances. By enabling transaction alerts and setting daily spending limits on your cards, you place yourself in a proactive position. Imagine receiving instant notifications for every transaction made with your card; this immediacy allows you to detect unauthorised activities right away. With daily spending limits in place, you can further control your finances and mitigate potential losses.
By embracing these measures and incorporating them into your daily routine, you can create a formidable barrier against the threats posed by infostealer malware and cybercriminals. Your sensitive information deserves protection, and with these strategies at your disposal, you can navigate the digital world with confidence and security.
Navigating the Digital Landscape: A Cautionary Tale
In the vast expanse of the digital world, where convenience often dances hand-in-hand with risk, a wise traveller must tread carefully. One of the most perilous missteps is the act of storing card information within web browsers. With a cunning nature, info stealers lay in wait, targeting the autofill data that resides in popular browsers like Chrome, Edge, and Firefox. Imagine a pop-up appearing before you, innocuously asking if you’d like to save your payment information. It may seem harmless, but resist the temptation! Instead, opt for the safety of a robust password manager. Moreover, consider fortifying your defences with supplementary security measures such as two-factor authentication. As technology evolves, innovative methods like Face ID and Touch ID are beginning to supplant traditional passwords, offering a new layer of protection for sensitive financial details.
As our digital journey continues, we encounter another pivotal aspect: passwords. The importance of maintaining strong passwords cannot be overstated. While adhering to all recommended password practices might not guarantee immunity from cyber breaches, it certainly helps bolster your defences. Since the exact desires of thieves remain shrouded in mystery, employing strong, frequently updated passwords is a prudent strategy. To simplify this task, I wholeheartedly recommend utilising a password manager—an invaluable tool that can generate and securely store complex passwords for you. For those seeking guidance on the best password managers available in 2025, further insights await.
Yet, the quest for security does not end there. Another layer of protection can be found in personal data removal services. While no service can promise to erase every trace of your existence from the internet, engaging with such a service offers a proactive approach to monitoring and managing your online footprint. These services can automate the often tedious process of eliminating your information from numerous websites over extended periods. If you’re curious about which data removal services stand out in this ever-evolving landscape, my curated recommendations are just a click away.
As we navigate this complex digital terrain, it’s crucial to remain vigilant against the threats posed by info stealers—malicious actors lurking in the shadows of our online lives. These threats are alarmingly prevalent, often masquerading as trustworthy applications or employing clever social engineering tactics to ensnare even the most discerning users. No one is entirely immune; even the most cautious among us can find ourselves ensnared by a meticulously crafted scheme.
Thus, the key to safeguarding oneself lies in exercising vigilance while exploring the web, downloading applications, or conducting financial transactions online. By leveraging tools like password managers and reliable antivirus software, we not only enhance our security but also streamline our digital experiences. In this grand narrative of our online existence, let us choose to be proactive heroes rather than unwitting victims, armed with knowledge and ready to face whatever challenges may arise in the realm of cyberspace.
In this age of digital connectivity, where our lives are interwoven with countless online accounts, many ponder a question: Have you embraced the convenience of a password manager, or do you find yourself still relying on the fragile faculties of memory or perhaps jotting down your passwords on scraps of paper?
Imagine a character in this narrative—let’s call her Clara. Each day, as she navigates the vast expanse of the internet, she faces the daunting task of keeping track of a multitude of passwords. With each new account she creates, a flicker of anxiety dances in her mind. Will she remember this one? Should she trust her memory, which can sometimes feel like a sieve? Or should she resort to scribbling those precious strings of characters on a notepad, leaving them vulnerable to prying eyes?
Clara often finds herself at a crossroads, contemplating the merits of modern solutions versus the age-old methods of recall and notation. In her heart, she knows there must be a better way—one that could alleviate the burden of remembering complex combinations and safeguard her online identity. Yet, as she sits at her computer, fingers poised over the keyboard, she wonders: Is it time to leap into the world of password managers, or will she continue to tread the familiar path of memorisation and note-taking?

Thus unfolds her journey—a tale not just about passwords but also about the choices we make in our digital landscape.
Secure browsing
When it comes to staying safe online, using a secure and private browser is crucial. Such a browser can help protect your personal information and keep you safe from cyber threats. One option that offers these features is the Maxthon Browser, which is available for free. It comes with built-in Adblock and anti-tracking software to enhance your browsing privacy.

Maxthon Browser is dedicated to providing a secure and private browsing experience for its users. With a strong focus on privacy and security, Maxthon employs strict measures to safeguard user data and online activities from potential threats. The browser utilises advanced encryption protocols to ensure that user information remains protected during internet sessions.
In addition, Maxthon implements features such as ad blockers, anti-tracking tools, and incognito mode to enhance users’ privacy. By blocking unwanted ads and preventing tracking, the browser helps maintain a secure environment for online activities. Furthermore, incognito mode enables users to browse the web without leaving any trace of their history or activity on the device.
Maxthon’s commitment to prioritising the privacy and security of its users is exemplified through regular updates and security enhancements. These updates are designed to address emerging vulnerabilities and ensure that the browser maintains its reputation as a safe and reliable option for those seeking a private browsing experience. Overall, Maxthon Browser offers a comprehensive set of tools and features aimed at delivering a secure and private browsing experience.
Maxthon Browser, a free web browser, offers users a secure and private browsing experience with its built-in Adblock and anti-tracking software. These features help to protect users from intrusive ads and prevent websites from tracking their online activities. The browser’s Adblock functionality blocks annoying pop-ups and banners, allowing for an uninterrupted browsing session. Additionally, the anti-tracking software safeguards user privacy by preventing websites from collecting personal data without consent.
By utilising the Maxthon Browser, users can browse the internet confidently, knowing that their online activities are shielded from prying eyes. The integrated security features alleviate concerns about potential privacy breaches and ensure a safer browsing environment. Furthermore, the browser’s user-friendly interface makes it easy for individuals to customise their privacy settings according to their preferences.
Maxthon Browser not only delivers a seamless browsing experience but also prioritises the privacy and security of its users through its efficient ad-blocking and anti-tracking capabilities. With these protective measures in place, users can enjoy the internet while feeling reassured about their online privacy.
In addition, the desktop version of Maxthon Browser works seamlessly with their VPN, providing an extra layer of security. By using this browser, you can minimise the risk of encountering online threats and enjoy a safer internet experience. With its combination of security features, Maxthon Browser aims to provide users with peace of mind while they browse.
Maxthon Browser stands out as a reliable choice for users who prioritise privacy and security. With its robust encryption measures and extensive privacy settings, it offers a secure browsing experience that gives users peace of mind. The browser’s commitment to protecting user data and preventing unauthorised access sets it apart in the competitive web browser market.