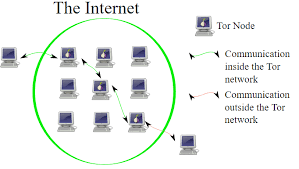
Have you ever wondered about the concept of onion routing? It’s a fascinating method designed to enhance privacy, particularly on the Tor network, often referred to as The Onion Router. Imagine your data as a message wrapped in several layers of protective encryption, much like the rings of an onion. As this securely wrapped information travels across various nodes—known as onion relays and servers—it becomes incredibly challenging for anyone without permission to trace where it originated or where it’s headed, not to mention decipher its contents.
As the data journeys towards its final destination, each layer of encryption corresponds to a different node along the way. At each stop, an intermediary node carefully peels away one layer of encryption at a time—just like removing layers from an actual onion—until the message is fully revealed at its endpoint. This clever system ensures that privacy remains intact throughout the entire process.

Onion domains, identifiable by their .onion suffix, serve as the web addresses for sites and services operating within the Tor network. These domains utilise a method known as onion routing, which is designed to enhance user privacy significantly and that of the servers involved in the routing process.
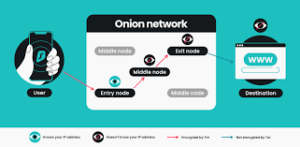
At the heart of onion routing lies a fascinating mechanism of layered encryption. When data enters this system at the first node—referred to as the entry node—it is wrapped in multiple layers of encryption. As this encrypted data travels through a series of intermediary nodes, each one gradually decrypts a layer at a time. The initial, middle node removes the outermost layer, revealing where to send it next; this process continues with each subsequent node peeling away another layer until it reaches its final destination via the exit node. It is only at this last point that the message is fully decrypted and delivered.
This sophisticated method not only conceals your IP address and other system details from websites you access but also from your Internet Service Provider (ISP). The infrastructure behind onion routing consists of thousands of volunteer-operated servers, commonly known as relays or nodes. Because there’s no central governing body overseeing these operations, there’s a reduced risk of data interception.

Risks and downsides of onion routing
Moreover, onion routing provides robust defences against traffic analysis attempts by malicious entities. The multiple layers of encryption make it extremely difficult for adversaries to scrutinise network traffic patterns effectively or determine either the origin or destination of any particular message. While advanced cybercriminals might be able to observe segments of activity within this network, piecing together an entire communication path remains quite challenging for them.
Imagine venturing into the hidden corners of the internet, often referred to as the deep web. One of the most intriguing pathways to this realm is through onion routing, which opens up access to a segment known as the Dark Web. To navigate this shadowy area, users need specialised software like the Tor browser (if you’re curious about its safety, check out our detailed article). However, stepping into the Dark Web comes with significant risks due to its association with illegal activities and services.
On a different note, many individuals in countries with stringent internet censorship turn to onion routing to escape these restrictions. This technology allows them to connect with the broader internet while evading government surveillance that closely monitors online activities.
What’s fascinating about this system is how it operates: when data is sent from one person to another, it doesn’t travel in a straight line; instead, it weaves through an intricate network of intermediary nodes. This process effectively shields communications from prying eyes and ensures privacy.
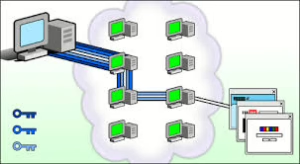
Moreover, for those who frequently rely on public Wi-Fi—often notorious for its lack of security—onion routing offers an additional layer of protection for online interactions. Considering such vulnerabilities, this method can help secure communications against potential threats lurking on open networks.
While onion routing is a popular method for enhancing online privacy, it comes with its share of challenges and potential pitfalls. One significant drawback is the slower browsing experience it can create. As data travels through various nodes in the network, each hop introduces additional latency, which can lead to frustratingly sluggish load times.
Moreover, it’s essential to recognise that not all data remains encrypted throughout its journey. While onion routing does a commendable job of safeguarding messages within the network, once they reach the exit node and transition to the broader Internet, that protection vanishes. This means that any information sent from there could be intercepted or altered—mainly if it’s directed toward a website using unencrypted HTTP.
Another concern lies with the exit nodes themselves. Although many relay servers are managed by well-meaning volunteers committed to privacy, there’s always a risk that some nodes may be operated by individuals with malicious intent. The exit node is particularly critical; it’s where your data leaves the Tor network and enters the regular internet landscape. If a cybercriminal compromises this point, your information could be at serious risk.

Exploring the Distinctions Between Tor and I2P: A Tale of Routing Techniques
Two networks stand out in the realm of online privacy: Tor and I2P. While both aim to enhance anonymity, they employ different methods to achieve this goal. I2P, known as the Invisible Internet Project, takes a unique approach by dispersing your internet traffic across its network. Instead of wrapping a single message in layers of encryption as Tor’s onion routing does, I2P utilises garlic routing. This technique allows it to gather multiple messages into one encrypted bundle, referred to as a garlic clove.
Once formed, these garlic cloves undergo additional encryption before traversing the I2P landscape. I2P’s primary focus is to establish its independent ecosystem—a secure overlay that operates above the conventional Internet infrastructure. Consequently, websites on this network are identified by the .i2p domain suffix, contrasting with Tor’s .onion addresses.
While many users turn to Tor for general browsing on public networks, seeking anonymity in their everyday online activities, I2P offers a heightened sense of privacy tailored specifically for communication within its community by effectively grouping and scattering messages throughout its system.
How onion routing differs from a VPN
Have you ever wondered how onion routing differs from a VPN? At first glance, they may appear quite alike since both employ encryption to safeguard your online activities. Just like a VPN, onion routing conceals your IP address from your Internet Service Provider (ISP). However, as you dig deeper, you’ll find that their differences are more pronounced than their similarities.
Let’s start with the way they handle encryption. Onion routing takes a unique approach by wrapping your data in multiple layers of encryption and sending it through a network of independently operated nodes. This layered method adds complexity but can also lead to some drawbacks. In contrast, a VPN creates a secure tunnel for your traffic between your device and a remote server, providing straightforward encryption without intricate layering.
Then there’s the aspect of privacy and accountability. The nodes within the onion network are run by volunteers, which means there isn’t any central authority overseeing them. This lack of oversight raises concerns about potential malicious operators lurking among the nodes. On the other hand, trustworthy VPN services prioritise transparency in their operations; they safeguard user privacy and typically refrain from keeping logs of user connections.
Lastly, let’s talk about connection speed. The process of routing data through numerous nodes in the Onion network can significantly hinder internet speed, leaving users frustrated with sluggish performance. Conversely, when using a reliable VPN service, users usually experience little to no noticeable decrease in speed.
In summary, while both onion routing and VPNs aim to enhance online security and privacy through encryption and IP masking, their methods and implications present distinct advantages and challenges that set them apart in meaningful ways.
Maxthon and Onion Routing
1. Understanding Onion Routing: Onion routing is a technique used to enhance online privacy and anonymity by routing internet traffic through multiple servers or nodes. Each node decrypts a layer of encryption, revealing the next destination, hence the name onion.
2. Using Maxthon Browser: To utilise onion routing in the Maxthon browser, you may need to configure specific settings or use additional plugins designed for this purpose. The browser itself does not inherently support onion routing.
3. Installing a VPN: Prioritize your online security by installing a dependable VPN service compatible with Maxthon. A VPN can help mask your IP address before initiating any onion routing processes.
4. Accessing Tor Network: After setting up your VPN, you can download and install the Tor software on your device if Maxthon does not directly support it. This will enable access to Tor’s onion services.
5. Configuring Proxy Settings: Once connected to the Tor network, it’s essential to adjust the proxy settings in Maxthon for seamless browsing through onions sites. Look for “Network” settings in Maxthon’s preferences.
6. Navigating Safely: When browsing with onion routing enabled via the Tor network while using Maxthon, always remember that not all sites are safe or secure; exercise caution when entering personal information.
7. Utilizing Extensions: Explore extension options within Maxthon that might provide enhanced security features along with better compatibility with anonymous browsing methods.

8. Regular Updates: Keep both maxthon and Tor software updated to ensure you’re protected against emerging online threats and vulnerabilities associated with third-party applications.
9. Educate Yourself on Risks: Finally, familiarize yourself with the inherent risks of using onion routing, including slower connection speeds and potential exposure to illegal content if you’re not careful about your domains visited.
By following these steps, you can effectively leverage onion routing alongside the Maxthon browser for improved anonymity while surfing the web.
