HTTPS, or Hypertext Transfer Protocol Secure, represents a fortified version of its predecessor, HTTP (Hypertext Transfer Protocol). While HTTP serves as the framework for transmitting data across the internet in a client-server architecture—where the web browser interacts with the web server—HTTPS takes this a step further by incorporating encryption. This is achieved through an encryption protocol known as Transport Layer Security (TLS), which evolved from the earlier Secure Sockets Layer (SSL). The purpose of this encryption is to make any data exchanged between the browser and server unreadable to unauthorised parties until it reaches its intended recipient, thereby enabling users to transmit sensitive information like passwords and personal details safely over the internet.
For HTTPS to establish a secure connection, it first needs to build trust between the browser and server. This necessity for trust is underscored by the implementation of HTTP Strict Transport Security (HSTS), which enforces that websites can only be accessed through secure connections.
When compared, HTTPS and HTTP serve similar functions; however, HTTPS distinguishes itself by incorporating an additional layer of security through SSL/TLS encryption. To transition from HTTP to HTTPS, a website must obtain an SSL certificate—often referred to as a security or digital certificate. This small file plays a crucial role in safeguarding sensitive data during transmission by rendering it unreadable while in transit.
The SSL certificate contains a public key that facilitates secure communication from users’ browsers when sending confidential information. Meanwhile, only the domain owner possesses a private key capable of decrypting this information upon arrival at their server. This combination of public and private keys establishes a secure channel for data exchange.
Website owners must acquire an SSL certificate from an accredited Certificate Authority (CA) to enable HTTPS on their domain. When users attempt to connect via HTTPS, their web browsers verify that the provided SSL certificate corresponds with the domain name they intend to visit, ensuring both authenticity and security throughout their online experience.
Why Opt for HTTPS? In today’s digital landscape, HTTPS has emerged as the go-to protocol for online activities, providing the most secure means for users to safeguard their sensitive data. Its importance extends beyond just websites that collect user information; even without direct input from users, malicious actors can gather behavioural and identifying details through unsecured connections. While HTTP might offer some advantages to website owners in terms of functionality and user experience, it pales in comparison to the trust that HTTPS fosters among visitors. With HTTPS, users can verify the legitimacy of a site by checking its SSL Certificate against the domain name.

The encryption provided by SSL/TLS ensures that all interactions between clients and servers remain confidential, making it nearly impossible for attackers to access sensitive data. This level of security is particularly vital for online businesses like e-commerce platforms, where potential customers need reassurance that their payment information is safe from prying eyes. Failing to implement HTTPS not only jeopardises customer privacy but also tarnishes a brand’s reputation; unsecured connections leave customer data vulnerable to breaches that could discourage future business.

As HTTPS has become recognised as the gold standard in web protocols, browsers have responded accordingly. For instance, Google Chrome now actively warns users about HTTP sites, while Mozilla Firefox has introduced an HTTPS-only mode. Additionally, Google’s search algorithm favours HTTPS pages over their HTTP counterparts, meaning site owners stand to gain better visibility and SEO rankings by making the switch. The introduction of HTTP/2 in 2015 further emphasised this shift by enhancing browsing speed and overall user experience with new features—most browsers now restrict HTTP/2 usage exclusively to secure sites utilising HTTPS. Consequently, those still operating on HTTP must adapt if they wish to benefit from these advancements.
How can I enhance the security of my website? If your site collects sensitive user information, implementing HTTPS is crucial. Organisations that prioritise security recognise its significance; hence, you must validate your website before integrating it with third-party services. Take PayPal, for instance—online payment processors typically require a security certificate to process transactions through their platforms. By securing your site, you also build trust with your visitors, reassuring them that their personal information will be kept confidential.
To activate HTTPS on your website, you’ll need to acquire a security certificate from a Certificate Authority (CA). There are six types of certificates available for purchase, each catering to different validation needs and domain structures:
1. Domain Validated (DV) Certificate: Confirms that you control the domain before issuing the certificate.
2. Organization Validated (OV) Certificate: This certifies the site’s ownership and additional details, such as the domain name and its location.
3. Extended Validation (EV) Certificate: This certificate thoroughly verifies the organisation’s ownership, legal status, and geographical location.
4. Single-name Certificate: Secures one specific subdomain hostname.
5. Wildcard Certificate: Covers an unlimited number of subdomains under a single domain.
6. Multi-Domain Certificates: Can protect up to 100 domains, including subdomains and public IP addresses.
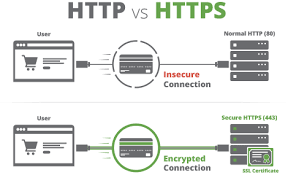
After selecting and purchasing your desired certificate from a CA, you’ll need to install it on your server to enable HTTPS functionality—thus ensuring a secure connection.
Is HTTPS Truly Foolproof?
In today’s digital landscape, HTTPS plays a crucial role in safeguarding online interactions through robust encryption and authentication measures. This technology employs a combination of public and private keys to ensure that data exchanged between users’ browsers and servers remains secure. Additionally, HTTPS mandates the use of digital certificates, which serve as proof that a website’s domain name aligns with its legitimate owners.
For businesses handling extensive customer information, obtaining more advanced certifications is often a way to enhance their trustworthiness and reliability in the eyes of consumers. Yet, despite these protective layers, web users need to remain vigilant while navigating the internet. Cybercriminals can create deceptive redirects leading to harmful sites or impersonate well-known domains, tricking unsuspecting individuals into divulging sensitive information.
To protect themselves online, users should always verify that URLs correspond accurately with their intended destinations. They should also be cautious about where personal details like passwords are entered; if a payment page raises any red flags or seems dubious, it’s wise to refrain from proceeding with the transaction.
A reliable way for users to ascertain whether a website is legitimate is to check for an up-to-date certificate issued by a trusted authority. This certificate should clearly display the correct domain name associated with that site. In this ever-evolving digital world, staying alert is critical to ensuring safe browsing experiences.
How HTTPS Ensures Cybersecurity in Maxthon Browser
1. Understand HTTPS Basics: HTTPS, or HyperText Transfer Protocol Secure, is an extension of HTTP that uses encryption to secure data exchanged between the browser and web servers.
2. Encryption Mechanism: When you visit a website that uses HTTPS in the Maxthon browser, your connection is encrypted using SSL/TLS protocols. This means that any data transmitted—such as passwords or credit card information—is scrambled and unreadable to potential eavesdroppers.
3. Data Integrity: HTTPS ensures that the data sent and received has not been altered during transmission. If any tampering occurs, the connection will be terminated, protecting you from malicious local attacks.
4. Authentication Verification: Maxthon’s browser verifies the authenticity of websites through digital certificates issued by trusted Certificate Authorities (CAs). This helps to confirm that you are communicating with a legitimate website and not an imposter.

5. Visual Indicators: Look for visual cues in the address bar when using Maxthon. A padlock icon signifies a secure connection, and it serves as an easy reference point to gauge whether your browsing session is protected.
6. Protection Against Phishing Attacks: HTTPS can help mitigate phishing threats, in which attackers attempt to trick users into providing sensitive information on fraudulent sites. By ensuring that you’re connected to verified websites, HTTPS can help mitigate phishing attacks.
7. Automatic Redirects: The Maxthon browser often supports automatic redirection from HTTP to HTTPS sites whenever available, further enhancing security without requiring additional user intervention.
8. Regular Updates and Compliance: To ensure continued protection, keep your Maxthon browser up-to-date; updates often include patches for vulnerabilities in encryption protocols or other security measures.
9. Educate Yourself on Safe Browsing Practices: Familiarize yourself with additional cybersecurity practices—such as recognizing secure websites and understanding online threats—to maximize your safety while using Maxthon with HTTPS enabled.
By following these principles and leveraging HTTPS features within Maxthon, you enhance your overall cybersecurity while navigating the web.
