Each week unveils yet another incident of data exposure. Whether it’s schools, factories, websites, or government bodies, there are always entities caught without adequate defences, and the consequences ripple out to affect us all. While it may be impossible to stop these distant breaches from occurring, instead of lamenting over them, take action! There are numerous steps you can take to safeguard your devices, data, and privacy. Enhancing the security of your gadgets and online presence doesn’t require extensive effort. Many of the suggestions outlined below hinge on basic common sense but can significantly bolster your safety in the digital realm.
Install Antivirus Software and Keep It Updated
Though we refer to this software as antivirus, its role extends far beyond merely combating computer viruses. Ransomware can lock up your files until you pay a ransom for their release. Trojan horse programs masquerade as legitimate applications while secretly stealing your sensitive information. Bots have the potential to turn your computer into part of a vast zombie network that can carry out denial-of-service attacks or distribute spam at the behest of their controllers. A robust antivirus program is essential for defending against these threats and many others lurking in cyberspace.
In an ideal world, you could set your antivirus software and forget about it, allowing it to operate quietly in the background while it manages updates and other tasks. However, in reality, it’s wise to check on it periodically. Most antivirus programs will show a reassuring green indicator when everything is functioning smoothly. If you happen to open the program and notice a yellow or red alert, be sure to follow the prompts to resolve any issues.
You might wonder if Windows has its built-in antivirus solution. Indeed, Microsoft Defender Antivirus is integrated into the operating system and automatically takes charge of your protection if it detects that no other antivirus software is installed. Conversely, it will step back when third-party protection is added. However, it’s important to note that this built-in option falls short compared to top-tier third-party solutions. Even the most reputable free antivirus options outperform Defender significantly—so don’t settle for less.
Whether you’ve opted for a basic antivirus or a comprehensive security suite, remember that you’ll need to renew your subscription annually. The most convenient approach is to sign up for automatic renewal; some products even offer a guarantee against malware as part of this service. If you ever switch products later on, you can easily opt-out.

Lastly, if your chosen antivirus or security suite lacks ransomware protection, consider adding a layer of defence designed explicitly for that purpose. Numerous free utilities are available that focus solely on combating ransomware, so take the time to explore them and find one that fits your needs perfectly.
Delve Into the Security Tools You Use
Numerous fantastic applications and settings are designed to safeguard your devices and personal information. However, their effectiveness hinges on your ability to use them correctly. To harness the full potential of these security tools, it’s essential to familiarise yourself with their features and configurations.
Take your smartphone, for instance; it likely has a built-in feature that helps you locate it if it goes missing. You may have activated this option, but have you taken the time to test it? Knowing how to use such functions can be crucial in a pinch.

Similarly, antivirus software is equipped to combat Potentially Unwanted Applications (PUAs)—those pesky programs that aren’t technically malware but serve no useful purpose. Yet, not all antivirus solutions come with PUA detection enabled by default. It’s wise to review your detection settings and ensure they are set up to block these nuisances effectively.
Moreover, some components of your security suite might remain dormant until you activate them yourself. When you install new security software, take a moment to explore every section of its main interface and glance at the various settings available. If there’s an introductory tour offered during installation, don’t skip over it; instead, engage with each step thoughtfully while absorbing all the features presented.
Antivirus programs often include browsing protection through browser extensions. These tools can redirect you away from harmful websites or phishing attempts by steering your browser towards a safe warning page if necessary. Many also highlight unsafe links directly in search results so that you avoid clicking on them altogether. However, this protection will only be adequate if the extension is installed correctly and functioning across all browsers you use.
To ensure that your antivirus is set up correctly and operating as intended, consider utilising the AMTSO (Anti-Malware Testing Standards Organization) security features check. If your antivirus fails this assessment, reaching out to tech support for assistance would be a prudent next step in securing your digital safety.
Create Distinct Passwords for Each Account
One of the simplest tactics hackers use to obtain sensitive information involves collecting a set of usernames and passwords from one source and testing those same credentials across various platforms. Imagine, for instance, that cybercriminals have gained access to your email account. They could then attempt to log into your banking or shopping accounts using the same username and password you used for your email. To effectively thwart this chain reaction caused by a single data breach, it’s essential to establish strong and unique passwords for every online account you maintain.
Crafting distinct and robust passwords for each account can be overwhelming if done manually. That’s where a password manager comes into play, equipped with a random password generator that takes on this daunting task. Many excellent password managers are available at no cost, making it easy to get started with one. While paid options often come with additional features, the free versions are usually quite capable.
With a password manager in place, you’ll only need to remember one master password—the key that unlocks all your other passwords within the manager itself. Once you’re logged in, the manager automatically signs you into your various online accounts. This not only enhances your security but also boosts your productivity; no longer will you waste time entering login details or grappling with the annoyance of resetting forgotten passwords.
Consider another important aspect: what happens if an unforeseen event were to occur—like being struck by a self-driving car? How would your loved ones access your accounts? The most sophisticated password managers allow you to designate a password heir, someone who will inherit access to your accounts when you’re no longer around.
Embrace the Power of a VPN
Whenever you find yourself tapping into a Wi-Fi network that isn’t yours, it’s wise to employ a virtual private network, commonly known as a VPN. Imagine you’re at your favourite coffee shop, sipping your drink while connecting to their complimentary Wi-Fi. The truth is, you have no idea how secure that connection really is. There’s always the risk that someone else on that same network could be lurking in the shadows, potentially accessing or stealing the files and information transmitted from your laptop or mobile device without your knowledge. The person managing the hotspot might not have your best interests at heart and could be on the lookout for sensitive data from unsuspecting users.

A VPN acts as a protective shield by encrypting your internet traffic and channelling it through one of its servers. This means that no one—not even the owner of that free Wi-Fi—can pry into what you’re doing online. Additionally, using a VPN masks your IP address, so instead of advertisers or trackers pinpointing you through your original IP, they’ll only see the address associated with the VPN provider. Moreover, if you want to access content restricted in your area, connecting through a VPN server located in another country can help bypass those barriers.
On a more critical note, individuals like journalists and activists operating under oppressive regimes have relied on VPN technology for secure communication for years. In short, whether you’re browsing on a laptop, phone, or tablet while connected to Wi-Fi networks outside of your control, having a VPN is essential. If this technology feels unfamiliar or daunting, don’t fret; our guide on how to set up and use a VPN effectively covers everything.
Embrace Multi-Factor Authentication
While it might feel like a hassle at times, multi-factor authentication (MFA) significantly enhances the security of your accounts. What does MFA entail? It means that gaining access to your account requires more than just entering your username and password; you need to clear an additional hurdle. If you have sensitive or valuable information stored in an account that supports MFA, it’s wise to activate this feature.

Services like Gmail, Evernote, and Dropbox are just a few examples where you can take advantage of this added layer of protection. Essentially, multi-factor authentication confirms your identity by requiring at least two out of three possible verification methods: something you know (your password), something you have (like your mobile phone), or something you are (such as biometrics like fingerprints or facial recognition).
For instance, when using something you have for verification, you may receive a code via text message or be prompted to approve a login through a smartphone app. Additionally, physical security keys are becoming increasingly popular; companies like Google and Microsoft are advocating for their use as part of secure authentication practices.
Relying solely on a password leaves your account vulnerable—if someone discovers that password, they can easily take control. However, with MFA in place, knowing the password alone isn’t enough for unauthorised access. Most password managers also support multi-factor authentication, though some may only enforce it when they detect logins from unfamiliar devices. Therefore, activating MFA on your password manager is essential for safeguarding your information.
Suppose you need help figuring out where to start with setting up multi-factor authentication or want to know which services offer it and how to enable it effectively. Our guide can provide the necessary insights to help you get started.
Always Utilize Passcodes, Even When Not Required
Whenever you have the option, it’s wise to enable a passcode lock on your devices. Just consider the wealth of personal information and connections stored on your smartphone; it’s hard to imagine going without that layer of security. While many smartphones come with a simple four-digit PIN as their default setting, don’t just accept that as sufficient. If your device supports biometric authentication, take advantage of it, but also ensure you set a robust passcode rather than relying on an easily guessed four-digit number.
Even if you primarily use Touch ID or similar features for quick access, remember that you can still unlock your device using the passcode—so this code must be robust. For those with modern iOS devices, there’s an option for a six-digit code; however, I recommend bypassing that and opting for something even more secure. Navigate to Settings > Touch ID & Passcode and select Change Passcode (or Add Passcode if you haven’t set one yet). You may need to input your existing passcode first. When prompted to enter a new code, choose Custom Alphanumeric Code instead of settling for standard options. Create a complicated password and make sure to save it securely in your password manager.
For Android users, the process may vary depending on the device model but generally involves locating the Screen Lock settings. After entering your current PIN, look for an option labelled Password (if available) and select it. Just like with iOS devices, create a strong password and document it safely as well. Prioritising these steps will significantly enhance the security of your data.
Embrace Smartphone Payments
The traditional use of credit cards feels increasingly outdated and needs more security. While you may not be responsible for this, there’s a proactive step you can take. Rather than reaching for that familiar credit card, consider utilising Apple Pay or a similar Android service wherever possible. The landscape of mobile payment applications is vast, and we even have a comprehensive list of options to explore.
Getting your smartphone ready for payments is often straightforward. The process typically begins with capturing an image of the credit card you plan to link to your payment app. Once that’s done, you’re almost set – just like that, you’re good to go! When you encounter point-of-sale terminals that accept smartphone payments, they usually display an icon indicating compatibility—this could be anything from an illustration of a hand holding a phone to a stylised wave symbol. To make your payment, simply place your device on the terminal and authenticate using either your fingerprint or facial recognition.
But why is this method superior to using the physical card? Well, when you pay through the app, it generates a unique authentication code that’s valid only for that specific transaction. So, even if someone managed to intercept that code, it would be rendered useless. Additionally, using smartphone payment apps significantly reduces the risk of falling victim to data theft via credit card skimmers.
Some mobile payment applications even offer online purchasing capabilities with similar one-time codes. If yours doesn’t provide this feature, reach out to your credit card issuer; they often allow access to temporary numbers explicitly designed for such transactions. These numbers are linked directly to your account but expire after their initial use.
Next time your bank or credit card company reaches out with offers for upgrades or services, inquire about one-time use card numbers—they can enhance your security considerably. You might also consider third-party applications like IronVest, which can conceal not just your credit card details but also your email addresses and phone numbers while shopping online or communicating with merchants—ensuring they never see any of your accurate information while you shop as usual.
Here’s Why Multiple Emails are Essential
Once upon a time, there was a savvy individual who understood the importance of keeping their online presence secure and organised. This person had a clever strategy: they used distinct email addresses for various types of accounts. By doing this, they could easily separate their online identities. For instance, if a phishing email pretending to be from their bank landed in the inbox of an account solely reserved for social media, it would raise immediate red flags.
This individual even maintained a unique email address specifically for signing up for apps that piqued their interest but might need better security practices or could bombard them with promotional content. Once they had thoroughly tested an app or service and deemed it trustworthy, they would transition to using one of their main email accounts for further interactions. If the dedicated account began to attract spammy messages, they wouldn’t hesitate to shut it down and create a fresh one.
Their approach was akin to the disposable emails offered by services like IronVest—an ingenious DIY solution! While many websites linked your email address directly to your username, some allowed users to choose unique usernames instead. This tech-savvy individual took advantage of that flexibility by selecting different usernames each time they signed up somewhere new—after all, their password manager kept track of them all! As a result, anyone attempting unauthorised access would need to guess both the username and password—a daunting challenge indeed!
Clear Your Cache
 It is essential to recognise the extent of information that your browser’s cache can retain about you. Stored cookies, search histories, and web activity may reveal sensitive details such as your home address, family background, and other personal information. To safeguard this data that might be hidden within your web history, regularly delete browser cookies and clear your browsing history. This process is straightforward; in browsers like Chrome, Edge, Firefox, Internet Explorer, or Opera, you can simply press Ctrl + Shift + Del to access a dialogue box that allows you to select which aspects of your browsing data you wish to remove. If you are using a different browser, try this key combination, as it may still function; if not, consult the menu for guidance. Please note that deleting cookies might disrupt functionality on certain websites and result in the loss of any customisations you’ve made. Most browsers provide an option to maintain cookies from specific favourite websites that should not be deleted. For an in-depth guide on how to clear your cache across various browsers, refer to our comprehensive feature on this topic.
It is essential to recognise the extent of information that your browser’s cache can retain about you. Stored cookies, search histories, and web activity may reveal sensitive details such as your home address, family background, and other personal information. To safeguard this data that might be hidden within your web history, regularly delete browser cookies and clear your browsing history. This process is straightforward; in browsers like Chrome, Edge, Firefox, Internet Explorer, or Opera, you can simply press Ctrl + Shift + Del to access a dialogue box that allows you to select which aspects of your browsing data you wish to remove. If you are using a different browser, try this key combination, as it may still function; if not, consult the menu for guidance. Please note that deleting cookies might disrupt functionality on certain websites and result in the loss of any customisations you’ve made. Most browsers provide an option to maintain cookies from specific favourite websites that should not be deleted. For an in-depth guide on how to clear your cache across various browsers, refer to our comprehensive feature on this topic.
Disable the ‘Save Password’ Functionality in Web Browsers

Regarding the information your browser may retain about you, it is essential to note that most browsers come equipped with an integrated password management feature. However, our recommendation at PCMag is to use these built-in options sparingly. We advocate for entrusting password security to specialised password management solutions. Consider this: when you opt for a third-party password manager, it usually provides the capability to import passwords from the browser’s storage. If such a manager can access your stored passwords, malicious software could potentially do so as well. Furthermore, consolidating your passwords within a dedicated password manager allows for seamless usage across various browsers and devices.
Avoiding Clickbait and Phishing Scams to Protect Your Online Security
A crucial aspect of maintaining your online safety involves exercising discernment regarding the links you engage with. The term clickbait extends beyond just amusing cat videos and sensational headlines; it also includes hyperlinks found in emails, messaging applications, and social media platforms such as Facebook. Phishing attempts often disguise themselves as legitimate websites, aiming to deceive you into providing sensitive information such as login credentials. Additionally, certain websites may initiate automatic downloads of malware that can compromise your device’s security without your consent.
It is advisable to refrain from clicking on links contained in emails or text messages unless they originate from a trusted source. Even when a link appears to come from a reliable contact, it is prudent to remain vigilant; there exists the possibility that their account has been breached or that the communication is fraudulent. This caution should also apply to links shared on social media platforms, even if they appear to be posted by friends. If a post deviates significantly from the typical style or content associated with your acquaintance’s online presence, it may indicate unauthorised access to their account.
Safeguarding Your Privacy on Social Media

It is often said that if you are not a paying customer of a service, you are instead the product. While social media platforms facilitate the sharing of thoughts and images with acquaintances, there exists a significant risk of oversharing personal information. Users can download their data from Facebook to gain insight into the extent of information the platform possesses about them. This may be particularly enlightening for individuals who frequently engage with quizzes that request access to their social media accounts—activities that ultimately provide unnecessary insights into trivial matters such as identifying which Disney princess or dog breed they resemble.
Additionally, one must remain vigilant against cybercriminals masquerading as friends on social media. A prevalent scam often begins with an unexpected private message, leading to unauthorised access to your account, which is subsequently used to perpetuate further scams. Should you receive an unusual message from a friend, it is prudent to verify its authenticity through alternative communication methods such as email.
Consider deactivating your account entirely to significantly limit the amount of personal data transmitted to Facebook. This measure prevents friends from inadvertently disclosing your information and eliminates exposure to third-party applications that could misuse your data due to a lack of access permissions. Furthermore, refrain from using Facebook credentials to log into other websites—this practice has always posed security risks.
Other social media platforms also warrant careful attention; for instance, Google may possess more comprehensive data about you than Facebook does. Therefore, it is essential to diligently manage your privacy settings across all platforms. Posts are not publicly accessible (with exceptions for Twitter and similar services). Exercise caution when sharing personal details in posts since friends might disseminate this information beyond your intended audience.
By taking these precautions, individuals can maintain their privacy while still enjoying the benefits and connections provided by social media platforms.
Maxthon Security
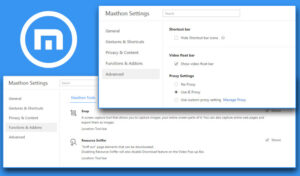
Securing your Maxthon browser is not just about convenience; it’s about protecting your online presence. First and foremost, always keep Maxthon updated. Regular updates bring essential security patches that address various vulnerabilities, so checking for them in the settings should become second nature.
Next, dive into your privacy settings. Take the time to customize these features to align with your comfort level—disabling location tracking and blocking third-party cookies can go a long way in enhancing your privacy.
Consider enabling HTTPS Everywhere if that option exists within Maxthon. This feature ensures that your connections to websites are encrypted, fiercely safeguarding your data from potential interception. Alongside this, installing reputable ad blockers from the Maxthon extensions store helps eliminate intrusive ads and shields you from harmful scripts.
Keep an eye on extensions too. Limit yourself to those that you truly need; excessive or untrusted extensions can introduce unnecessary security risks. Additionally, if you’re serious about protecting your browsing activities, using a Virtual Private Network (VPN) adds another layer of encryption and privacy against prying eyes.
Make it a habit to regularly clear your cache and browsing history as well. This routine practice helps remove stored data that could expose personal information or habits.
Lastly, stay vigilant against phishing scams by scrutinizing suspicious links and emails before clicking. A simple hover over links can often reveal their true intentions. Don’t forget the importance of backing up important bookmarks and settings too; use Maxthon’s built-in options or export them manually to ensure vital information is never lost when troubleshooting arises.
By following these straightforward steps, you’ll significantly enhance the security of your browsing experience on Maxthon.

