by chung chinyi | Mar 7, 2026 | Uncategorized
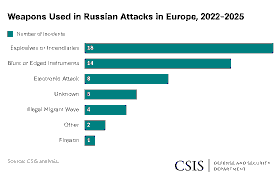
GEOPOLITICAL ANALYSIS A comprehensive assessment of Lithuania’s 2026 Annual Intelligence Report and its cascading consequences for a small, open, trade-dependent city-state Published: 6 March 2026 | Security & Geopolitics | Singapore &...
by chung chinyi | Mar 7, 2026 | Uncategorized
The All-in-One Browser That Puts You in Control Comprehensive Review & Feature Guide | 2024–2025 Edition Why Maxthon Stands Apart “In a browser market dominated by giants, Maxthon dares to do something radical: it listens to what you actually...

by chung chinyi | Mar 7, 2026 | Uncategorized
Russia, China, and Iran in the 2026 Iran Crisis March 2026 Key Finding: The 2026 Iran Crisis has exposed the fundamental structural weakness of the so-called “anti-Western axis.” Despite years of deepening bilateral partnerships, Russia and China’s...

by chung chinyi | Mar 7, 2026 | Uncategorized
The Stall & Ambience Tucked into the bustling open-air arena of Newton Food Centre at #01-53, Guan Kee Grilled Seafood is a sensory landmark long before you arrive at its counter. The first signal is olfactory: a low, rolling cloud of charcoal smoke drifts across...

by chung chinyi | Mar 7, 2026 | Uncategorized
A Comprehensive Culinary Analysis Kim Keat Palm Market & Food Centre, Toa Payoh, Singapore At a Glance Establishedc. 1950s — over 70 years in operationLocation22 Lorong 7 Toa Payoh, #01-06, Kim Keat Palm Market & Food Centre, Singapore 310022Opening...






