Secure Browsing with Extended Zero Trust
The most recent security threat facing distributed enterprises highlights the significant cyber risks posed by the public Internet. When employees access the web for either work or personal purposes, they expose themselves to potential phishing and malware attacks....
Tips to Thwart Browser-Based Cyber Attacks
In today's digital landscape, web browsers play an essential role for businesses, granting seamless access to a wealth of websites and online content. However, they also bring with them considerable security threats. A staggering 95% of undetectable malware makes its...
Discover the Secrets Behind Every URL
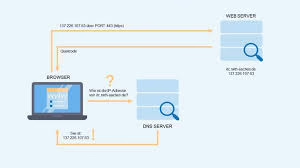
A URL, or Uniform Resource Locator, serves as a distinct marker for finding resources online, commonly referred to as a web address. Each URL is made up of several components, such as the protocol and domain name, which guide web browsers on how to access specific...
Why HTTP Is Essential for Browsing
The World Wide Web stands out as a highly favoured application that operates on the Internet. It encompasses two critical types of software: web browsers and web servers. Any device connected to the Internet is capable of running either a web browser, a web server, or...
B/S (Browser/Server) Explained
B/S Architecture Overview The term B/S refers to Browser/Server architecture, a framework that gained prominence with the advent of Internet technology. In this model, users interact with applications primarily through a web browser, such as Netscape Navigator...
How Web Applications Revolutionize Our Daily Lives
What exactly is a web application? At its core, a web application, often referred to as a web app, is software that resides on a remote server and is accessed via the Internet using a web browser. By definition, web services fall under the umbrella of web apps,...
How Websites Use Your Data
Have you ever paused to think about why certain online advertisements seem tailor-made for your likes and interests? Or how is it that websites and apps can recall your preferences each time you return? The answer lies in the realm of online tracking. Let's delve into...
Unlock Seamless Access with Single Sign-On
Throughout my journey of exploring authentication methods in web browsers, I've come across many intriguing aspects. Today, I want to delve into a particular feature that often flies under the radar: Browser Single Sign-On (SSO). Just recently, a user was taken aback...
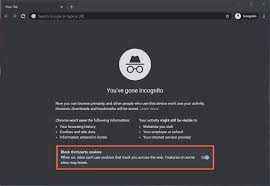
A Guide to Understanding Tracking Cookies
At the dawn of the new millennium, marketers began to embrace tracking cookies as a convenient method for connecting with their desired audiences on a broader scale. However, as time progressed, these tools lost their appeal due to increasing concerns over user...
How HTML Web Storage Changes the Way We Experience Websites
HTML Web Storage is a powerful feature that allows web applications to save data directly in the user's browser. Before the advent of HTML5, developers relied heavily on cookies for storage. This method was limited and inefficient, as cookies were sent with every...