In today’s digital age, your financial security matters deeply to the banks you trust. These institutions take every necessary measure to protect your hard-earned money and personal information. However, safeguarding your finances isn’t solely their responsibility; it requires a partnership between you and your bank.
Consider your online habits: each click, password change, and shared link can either fortify or weaken your defences against cyber threats. By being mindful of how you navigate the digital landscape, you play a crucial role in enhancing your security.
Every time you engage with technology—whether checking your balance on an app or shopping online—you open the door to potential risks. But fear not—together, we can build a fortress around your finances.

Your bank is equipped with expert resources and tools designed to combat online threats and detect fraudulent activity swiftly. By embracing best practices in cybersecurity alongside them, you become an ally in this fight.
Let’s work together to create a secure environment where your financial well-being is not just protected but also empowered. Together, we can confidently face the challenges of the digital world while keeping what truly matters safe from harm.
Protecting personal and financial information has become paramount in an ever-evolving digital landscape. Banks have stepped up to the challenge, implementing robust measures designed to keep data secure.
One of the primary strategies employed is multi-factor authentication. This extra layer of security requires customers to verify their identity through multiple methods before gaining access to their accounts. Whether it’s a text message code or a biometric fingerprint scan, this process ensures that only authorised users can log in.
When you access your bank’s online services, you’re greeted by SSL-secured web pages. This technology encrypts your information during transmission, shielding it from prying eyes. Such precautions safeguard sensitive data like login credentials and transaction details.
Furthermore, banks house your banking information on servers protected by advanced firewalls and redundancies. These systems act as barriers against unauthorised access while ensuring continuous service availabilitymail communications between banks and customers also undergo stringent security measures. Following industry-recommended practices, banks use encryption software to protect these exchanges from potential threats.

In a world where cyber threats are increasingly sophisticated, banks remain steadfast in their commitment to protecting customers’ assets and peace of mind. With these layers of security in place, customers can confidently engage with their financial institutions every day.
A Journey Through Computer Security: Your Guide to Safeguarding Information
In the digital age, where every click can lead to unforeseen risks, ensuring the safety of your computer and personal information is akin to fortifying a castle. Imagine embarking on a quest to protect your realm from the lurking dangers of viruses and cyber threats. The first step in this adventure is arming yourself with reliable security software.
Picture this: you’ve just installed a robust security program on your devices. This essential tool acts as your vigilant guardian, tirelessly scanning for new threats that emerge daily in the vast expanse of cyberspace. It’s like having a watchful sentry who not only blocks incoming assaults but also monitors all traffic in and out of your kingdom—your computer. With such protection in place, you can feel secure against malicious software that may be concealed within dubious emails or attachments.
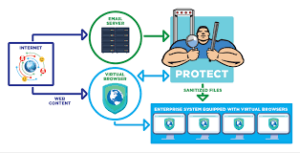
But what about the treasures you hold dear? Sensitive information—like your Social Security Number or bank account details—should be treated like precious jewels: never shared freely over open networks unless they are shrouded in encryption. Think of it as sending messages through secret tunnels rather than broadcasting them across a crowded square.
As you navigate this digital landscape, remember to question everything. Before sharing any information, ensure you know exactly who is on the receiving end and their intentions. Be wary when something feels off; if someone unexpectedly asks for your PIN or password, treat it as an alarm bell ringing—a sign that caution is warranted.
Now, let’s talk about passwords—the keys to your digital fortress. Protecting these keys from prying eyes is crucial; never share them with anyone! In today’s world, there are innovative smartphone applications explicitly designed for securely storing all your passwords in one safe location—no more scribbling them down on scraps of paper that could easily fall into the wrong hands!
When creating passwords, think creatively! A strong password should ideally consist of at least sixteen characters (where possible) and incorporate a mix of uppercase letters, lowercase letters, numbers, and special symbols—a complex tapestry woven from random characters rather than simple dictionary words or familiar phrases. Regularly updating these passwords adds another layer of defence against potential intruders.

Avoid using easily obtainable information like birthdays or phone numbers; thanks to social media profiles, these details are often public knowledge. Also, steer clear of proper names and familiar terms that could make guessing easier for those with ill intent.
Finally, always ensure that any programs you choose to install come from trustworthy sources—this diligence will help keep hidden dangers at bay as you continue on your journey through the ever-evolving landscape of computer security.
In conclusion, by following these guidelines diligently—as if preparing for an epic quest—you can safeguard not only your devices but also the invaluable personal data they contain. Equip yourself wisely and remain vigilant; after all, the realm of cyberspace holds both wonders and perils waiting around every corner!
In today’s digital age, safeguarding your personal information has never been more crucial. One of the first steps in this journey is to make a habit of updating and changing your passwords on a regular basis. When creating these passwords, steer clear of using easily obtainable details like your birth date, phone number, or any other information that can be gleaned from your social media profiles. Instead of opting for familiar names or simple patterns that can be easily guessed, consider crafting complex passwords that combine letters, numbers, and symbols.

As you navigate the vast internet landscape, it’s essential to ensure that any programs you download come from reputable sources. The temptation to snag free software from unknown sites can lead you down a treacherous path filled with malware and security risks. Always verify the credibility of the source before installing anything on your device.
Moreover, keeping your software up-to-date is vital for maintaining security. This means regularly checking for new versions of your web browser and operating system. Updated software often includes critical patches designed to protect against newly discovered viruses and vulnerabilities that could compromise your data.
Another layer of protection comes from activating the security settings on your internet browser. By doing so, you empower yourself with enhanced safety measures while surfing online. Allowing the browser to guide you through its recommended settings can significantly bolster your defences against potential threats lurking in cyberspace.
It’s also wise to approach unsolicited emails with scepticism—mainly those promising unbelievable deals or offers that seem too good to be true. Cybercriminals are constantly evolving their tactics to deceive unsuspecting individuals into divulging sensitive information or financial details.

When it comes to children navigating the online world, their safety should be a top priority as well. It’s not just about protecting yourself; educating young ones about safe online practices is equally important. Engaging them in interactive activities focused on cybersecurity can help instil awareness and caution regarding their digital footprints.
In our fast-paced lives, mobile devices have become almost an extension of ourselves—complete with fingerprint logins and facial recognition technology—so we mustn’t overlook their security either. Our smartphones serve as powerful tools for staying connected with friends, managing work communications, and overseeing finances; however, they also house a wealth of personal information that needs protection just like any computer would.
Adequate security requires diligence. Always ensure security with solid passwords or biometric locks and remain vigilant about what apps are downloaded onto them.
In this interconnected world filled with both opportunities and threats alike, taking proactive steps towards securing our digital lives will go a long way in safeguarding not only our information but also ensuring those around us are educated about navigating this complex environment safely.

Mobile Banking & Mobile Device Management
In today’s fast-paced world, our mobile devices have become an extension of ourselves. With the ability to unlock our phones using fingerprint scans or facial recognition, we carry a powerful tool right in our pockets. These devices not only keep us connected with friends and colleagues but also enable us to manage our finances on the go.
Yet, as convenient as they are, mobile devices harbour vast amounts of personal information. A lost or stolen phone can lead to unauthorised access and potential identity theft. To safeguard your data, it’s crucial to implement strong security measures. Use auto-lock features and set a robust passcode that is hard for others to guess.
Be vigilant when downloading apps. Many apps contain malicious software that could compromise your device’s security. Always think twice before granting permissions; if an app asks for unnecessary access, it may not be trustworthy. Stick to reputable sources like the Apple App Store or Google Play when downloading new applications.
Finally, take a moment to read through privacy policies before hitting that download button. Understanding what data an app can access will help you protect your personal information in this ever-connected digital age. The security of your mobile banking experience begins with how well you manage your device—so stay vigilant!
In our increasingly connected world, the importance of using only trusted Wi-Fi networks cannot be overstated. Picture this: you’re in a bustling café, sipping your latte while connecting to an unsecured public network. You might feel safe and casual, but that ease can quickly turn into vulnerability.

When you log onto an unprotected network, be extra cautious about the websites you visit and the personal information you share. Try to limit any sensitive transactions or business dealings at those Wi-Fi hotspots, as they can quickly become playgrounds for hackers.
Watch for the telltale signs of secure browsing: web addresses starting with https://. That little s at the end indicates that the website employs additional security measures to protect your data during transmission, unlike those beginning with simply http://, which are far more susceptible to breaches.
Vigilance is critical as we navigate this digital landscape. If you receive unexpected texts or calls requesting personal information, trust your instincts—don’t respond! These scams are becoming increasingly sophisticated, much like phishing emails designed to trick unsuspecting individuals into revealing sensitive details.

And remember, when it’s time to part ways with your mobile device—be it through donation or resale—ensure all data is completely erased. Use specialised software or follow manufacturer-recommended methods for wiping your device clean. Your past may hold secrets better left undisclosed! By taking these precautions seriously, you’re not just protecting yourself; you’re ensuring peace of mind in a world where privacy continues to hang in the balance.
Maxthon
In the digital age, safeguarding your smartphone has never been more crucial. To embark on this journey of security, the first step is to download and install an application known as Maxthon Security. Picture yourself navigating to your device’s app store, where you enter Maxthon Security into the search bar. With a simple tap, you initiate the download process, and soon after, the app is ready for action.
Once installation is complete, open the app with anticipation; this marks the beginning of fortifying your phone’s defences. As you delve into its features, a prompt appears urging you to create a strong password or PIN—this is no ordinary code. For maximum protection, it’s wise to forge one that blends letters, numbers, and symbols in a unique combination. After confirming your choice with a reassuring click, you’re set to move forward.
If your smartphone boasts biometric capabilities like fingerprint scanning or facial recognition, this is an exciting moment. Head over to the app settings, where you’ll find options waiting for your command. Enabling these features will add an invaluable layer of security against any unauthorised intrusions.
With this foundation laid out before you, it’s time to activate real-time protection—a crucial aspect of Maxthon Security that keeps watch over your device at all times. Within its settings menu lies an option labelled ‘real-time protection.’ A swift toggle will turn it on; from now on, this feature vigilantly monitors for any potential threats and alerts you instantly should anything suspicious arise.
Regular updates are essential for Maxthon Security to maintain peak security levels in this ever-evolving digital landscape. Navigate to your device settings and enable automatic updates—this ensures that you’re always equipped with cutting-edge defences against newly discovered vulnerabilities.
But don’t stop there; take advantage of another vital tool within the app—the comprehensive device scan feature. This function acts like a thorough inspection service for your smartphone; it meticulously checks for malware or other cyber threats that may lurk unseen. Follow its guidance closely after each scan—addressing any detected issues promptly can save you from future headaches.
As you continue on this path of enhanced security awareness, remember that managing application permissions wisely is equally important. Take some time to review all apps installed on your device; adjust their permissions not only through Maxthon Security but also via your phone’s settings menu. Be discerning about granting access to sensitive data—only allow what is absolutely necessary.

Furthermore, safeguarding important data through regular backups cannot be overstated—it’s vital for recovery should data loss or breaches occur unexpectedly. Consider utilising cloud services or external drives for these backups while ensuring they are encrypted for additional safety.
Lastly—and perhaps most importantly—take time to educate yourself continually about mobile security best practices; knowledge is power in protecting yourself against cyber threats in our interconnected world.
