by chung chinyi | Dec 4, 2025 | Uncategorized
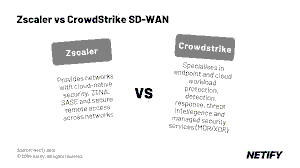
Case Study, Market Outlook, Solutions Analysis & Singapore Impact Executive Summary The cloud security market is experiencing a strategic divergence between two leading players. CrowdStrike’s endpoint consolidation model contrasts sharply with...

by chung chinyi | Dec 4, 2025 | Uncategorized
Executive Case Study & Regional Impact Analysis Executive Summary The December 2025 strategic partnership between VIAVI Solutions and QNu Labs represents a pivotal development in global quantum-safe network infrastructure. This collaboration addresses the urgent...

by chung chinyi | Dec 4, 2025 | Uncategorized
Executive Summary In December 2024, Huaxia Bank made history by issuing China’s first commercial bonds on blockchain infrastructure, accepting payments exclusively in digital yuan. The $637 million bond issuance through its subsidiary Huaxia Financial Leasing...

by chung chinyi | Dec 4, 2025 | Uncategorized
Executive Summary Singapore’s workforce is navigating a period of significant transformation as it enters 2026. Economic uncertainty, demographic shifts, and evolving workplace expectations are reshaping worker priorities and employer strategies. This case study...

by chung chinyi | Dec 4, 2025 | Uncategorized
Singapore’s hawker centres offer some of the best dim sum experiences outside of Hong Kong, with skilled chefs serving restaurant-quality bites at fraction of the cost. From ex-hotel chefs to multi-generational family operations, these stalls prove that...

by chung chinyi | Dec 4, 2025 | Uncategorized
Opening: December 11, 2025 | Bugis+, #01-19 After years of anticipation, the cult-favorite American fast-food chain is finally planting its flag in Southeast Asia, with Singapore serving as the launching pad for its ambitious regional expansion. With a substantial $97...

by chung chinyi | Dec 4, 2025 | Uncategorized
Executive Summary War insurance costs for ships sailing to the Black Sea have surged dramatically in December 2024, with rates jumping over 250% following Ukrainian drone attacks on Russian-linked tankers. This case study examines the crisis, market outlook, potential...

by chung chinyi | Dec 4, 2025 | Uncategorized
Executive Summary French President Emmanuel Macron’s December 2025 state visit to Beijing represents a critical moment in European-Chinese relations, as France attempts to position Europe as an independent strategic actor amid intensifying US-China rivalry. This...

by chung chinyi | Dec 4, 2025 | Uncategorized
The Erosion of Consensus: Transatlantic Divergence and the Perils of Expedient Mediation in the Russia-Ukraine Conflict (2025) Abstract This paper analyzes the reported skepticism expressed by French President Emmanuel Macron and German Chancellor Friedrich Merz...

by chung chinyi | Dec 4, 2025 | Uncategorized
Executive Summary Circle Asia Technologies, in partnership with Visa and Pismo, is launching Vietnam’s first AI-powered PayLater card in early 2026. This case study examines the business model, market outlook, solution architecture, long-term feasibility, and...











